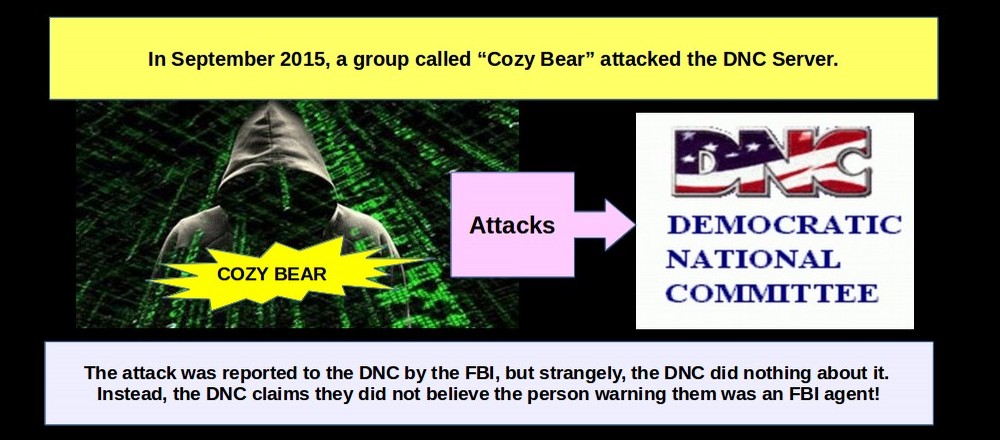
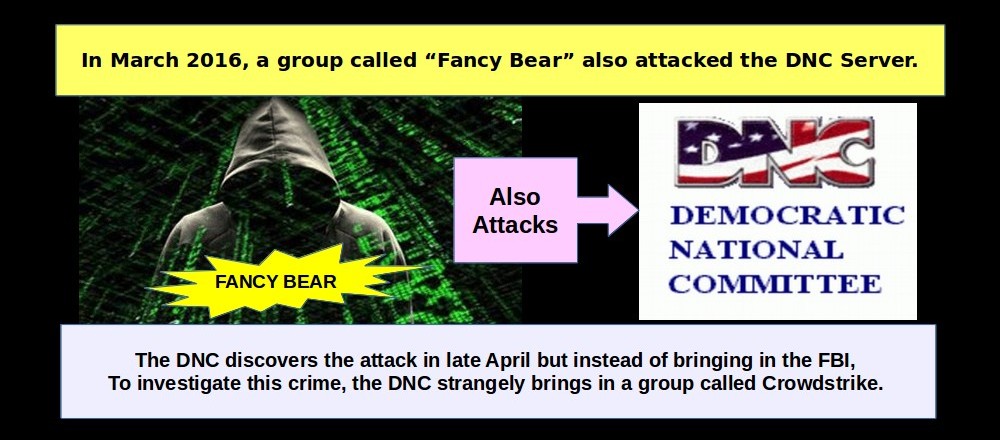
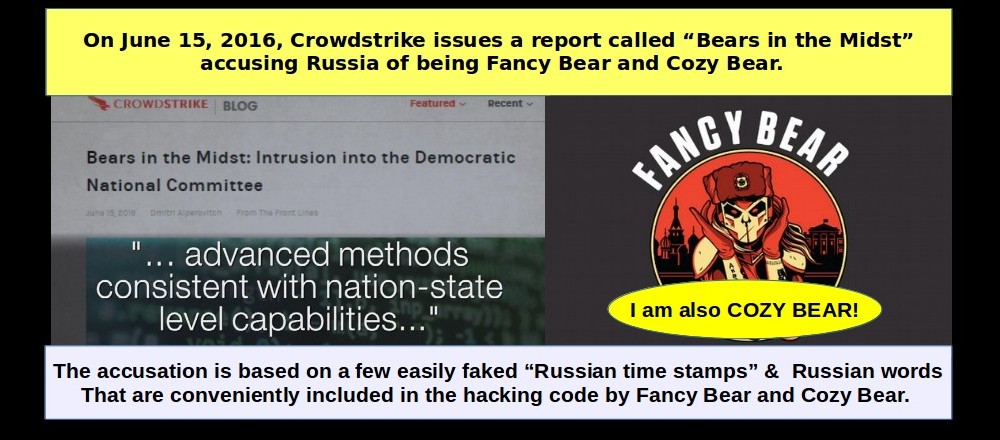
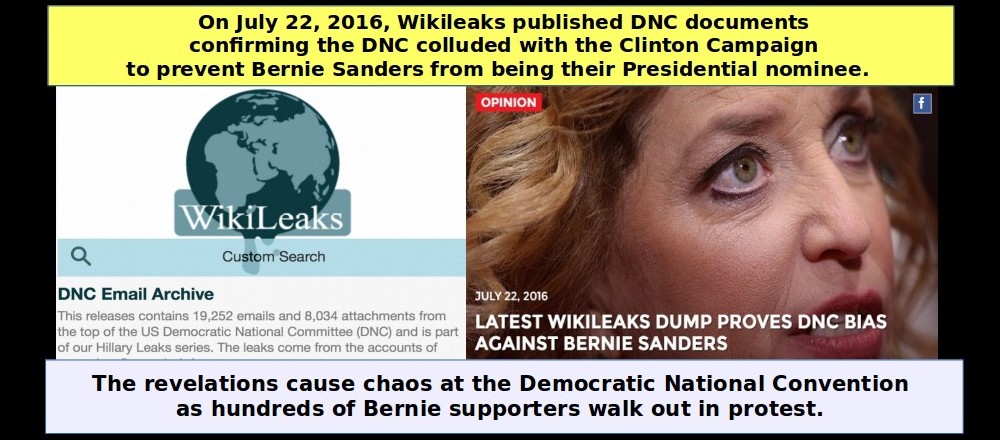
Welcome to Turning Point News! We live in Washington State and are concerned about civil liberties and preserving Internet freedom. Our goal is to shine a light in the darkness. We provide well-researched independent analysis to offer our readers an alternative to propaganda from the main stream media. We believe that the people should be in charge of the government rather than the government in charge of the people. Please help us spread the word by sharing our articles on social media.
A week before Christmas, the US Senate Intelligence Committee released a 101 page report accusing Russia of depressing Democrat voter turnout in the 2016 Presidential election - mainly by targeting African-Americans on social media. Here is the link to the Senate Russia report: https://disinformationreport.blob.core.windows.net/disinformation-report/NewKnowledge-Disinformation-Report-Whitepaper.pdf
Among the “evidence” given in the report was this picture of Jesus wearing a Trump campaign hat.

Do you think that this meme would influence anyone to change their vote in the 2016 election?
The report also claimed seven Facebook pages were used to affect the outcome of the US elections. The only one of these pages that is still in existence is a page called Friends of Russia. Here is an image of their Facebook page in October 2016:
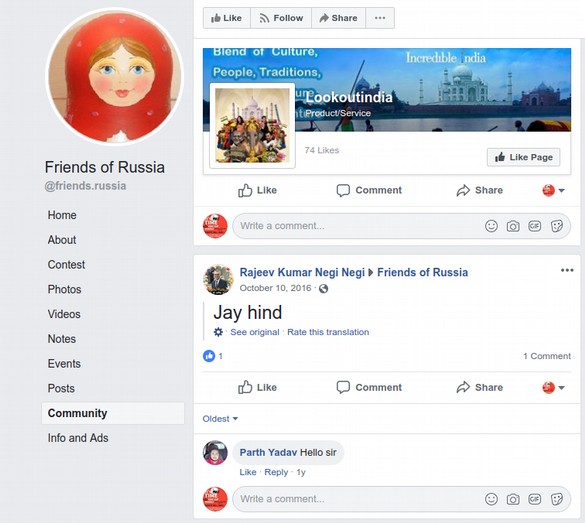
There were no posts on this page about either Trump or Clinton. The only post was from someone named Parth Yadav who wrote “Hello Sir.” This post could not have possibly affected the outcome of the US election.
The Senate report went on to list all of the 61,483 Facebook posts that were in their database. None of these posts were actually published in the Senate report. But the report did note that only 2.9 percent of these posts even mentioned Clinton and only 4.2 percent of the posts mentioned Trump. Here is a screen shot from the report.
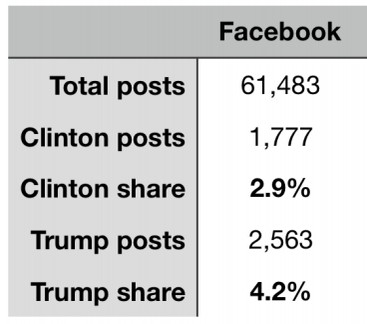
It is true that there were 800 more posts for Trump in the Senate Database than their were for Clinton. But keep in mind that half of these 61,483 posts occurred AFTER the election was over. Also keep in mind that Facebook has billions of posts every day. So even 62,000 posts is much less than one tenth of one percent of all Facebook posts. Could 400 posts swing an election?
False Allegations Against a Single Black Website
Surprisingly, most of the 101 page Senate Report was spent claiming that the Russians spent most of their efforts trying to convince black voters to not vote for Hillary Clinton. Here is a quote from the Senate Russia Report:
“The most prolific IRA (Russian spy group) efforts on Facebook and Instagram specifically targeted Black American communities and appear to have been focused on developing Black audiences and recruiting Black Americans as assets.”
The Senate “Russian” report repeatedly claimed that the main weapon used by the Russians to suppress the turn out of black voters was a website called blackmattersus.com – a website that is still in existence.
Among the “evidence” given in the report was this picture of Jesus wearing a Trump campaign hat.

Do you think that this meme would influence anyone to change their vote in the 2016 election?
The report also claimed seven Facebook pages were used to affect the outcome of the US elections. The only one of these pages that is still in existence is a page called Friends of Russia. Here is an image of their Facebook page in October 2016:

There were no posts on this page about either Trump or Clinton. The only post was from someone named Parth Yadav who wrote “Hello Sir.” This post could not have possibly affected the outcome of the US election.
The Senate report went on to list all of the 61,483 Facebook posts that were in their database. None of these posts were actually published in the Senate report. But the report did note that only 2.9 percent of these posts even mentioned Clinton and only 4.2 percent of the posts mentioned Trump. Here is a screen shot from the report.

It is true that there were 800 more posts for Trump in the Senate Database than their were for Clinton. But keep in mind that half of these 61,483 posts occurred AFTER the election was over. Also keep in mind that Facebook has billions of posts every day. So even 62,000 posts is much less than one tenth of one percent of all Facebook posts. Could 400 posts swing an election?
False Allegations Against a Single Black Website
Surprisingly, most of the 101 page Senate Report was spent claiming that the Russians spent most of their efforts trying to convince black voters to not vote for Hillary Clinton. Here is a quote from the Senate Russia Report:
“The most prolific IRA (Russian spy group) efforts on Facebook and Instagram specifically targeted Black American communities and appear to have been focused on developing Black audiences and recruiting Black Americans as assets.”
The Senate “Russian” report repeatedly claimed that the main weapon used by the Russians to suppress the turn out of black voters was a website called blackmattersus.com – a website that is still in existence.
By Elizabeth Hanson M. Ed.
January 1, 2017
In this article I compare the headlines of mainstream news to the headlines of independent news as an example of why we need independent news. I also give suggestions on how to ascertain the truth when reading news articles on the Internet.
In November of 2016, the Washington Post published a blacklist of 200 websites which they deem as promoting Russian propaganda and thus dangerous to U.S. consumers of news. It was published by a group called “Prop or Not”.
https://www.washingtonpost.com/business/economy/russian-propaganda-effort-helped-spread-fake-news-during-election-experts-say/2016/11/24/793903b6-8a40-4ca9-b712-716af66098fe_story.html?utm_term=.3a6e770f8ac7
Here's the link to the Prop or Not list -http://www.propornot.com/p/home.html
The Washington Post has many excellent reporters and has published some great stories over the years, so when I first heard about this list, I thought “Oh… it probably lists some sites like Russia Today (RT), sites directly related to Russia.
However, much to my surprise upon reading their list of propaganda websites, I found that the Prop or Not list contains the ten websites I have read almost daily for many years. Here in alphabetical order:
#1: Black Agenda Report
#2: Consortium news
#3: Counterpunch
#4: Global Research
#5: Naked Capitalism
#6: Oped news
#7: Truthdig
#8: Truthout
#9 Washingtonsblog
#10: Zerohedge
The Washington Post's Prop or Not team also provides us with this graphic to scare the living bejesus out of people, in hopes, I assume, to deter Americans from visiting any of the sites they deem as propaganda and to show us that they mean business:

The team at Prop or Not then goes on to tell us that we should be reading news from these main stream media news sources instead of independent news sources. Here is a quote from their website:
“Obtain news from actual reporters, who report to an editor and are professionally accountable for mistakes. We suggest NPR, the BBC, the New York Times, the Wall Street Journal, the Washington Post, Buzzfeed News, VICE, etc, and especially your local papers and local TV news channels. Support them by subscribing, if you can!”
Comparing Headlines of Prop or Not Approved Sites versus Independent News Sites
Here's a look of some of their recent headlines of Prop or Not's trusted media sources regarding Russian hacking and the subsequent sanctions Obama is putting on Russia.
NPR: “US. Officials Say Russia Hacked A Vermont Utility”
New York Times: “U.S. Sanctions Russia Over Election Hacking”
Wall Street Journal: “Obama Strikes Back at Russia for Election Hacking”
Washington Post: Obama administration announces measures to punish Russia for 2016 election interference
These mainstream news headlines are being widely read by Americans and will likely have the effect of pushing most Americans into agreeing with sanctions and perhaps further aggressions against Russia.
We saw how believing in weapons of mass deception led to aggressions against Iraq and resulted in well over 100,000 civilian deaths between 2003 and 2010.
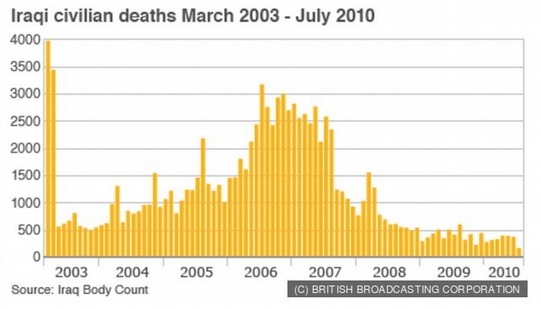
http://www.bbc.com/news/world-middle-east-11107739
And there were no weapons of mass destruction found. Ever since 9 / 11, millions of Americans have become disillusioned with the mainstream news, and its framing of news related to subjects like trade agreements, foreign policy, banker misdeeds, the economy and education have been reading news from independent media.
Let's compare those “ra-ra sanctions against Russia” headlines to the headlines in some of the independent media Americans read which are on the Prop or Not list:
Black Agenda Report - “Freedom Rider: Syria, Russia and American Desperation”
Consortium news - “Details Still Lacking on Russian ‘Hack”
Counterpunch - “We Do Not Live in “Post Truth” World, We Live in a World of Lies and We Always Have”
Global Research- “Obama’s Sanctions against Moscow “Intended to Box In Donald Trump”. Evidence that Hacking of DNC Accusations are Fake”
Opednews - “DHS FBI Claim of Russian Hacking is Fake News”
Truthdig - “Experts Aren’t Convinced by FBI and Homeland Security Report on Alleged Russian Hacking”
Washingtonsblog - “Creator of NSA's Global Surveillance System Calls B.S. On Russian Hacking Report”
Zerohedge - "Something Stinks" - Like Iraq WMD Fiasco, Russia Story Doesn't Add Up
While the mainstream media reported the Russian Hacker story as if it were the truth, alternative news sources reported why the Russian Hacker story might not be true.
Six Principles for Evaluation the Truth
I'm a teacher with a background in Linguistics. An always interesting question to answer with my students is how do you know if a media source is telling the truth?
I follow these six principles:
#1: Have they told the truth in the past? (Weapons of mass destruction, Economic recovery)
#2: Who is funding the site? (Gates money, CIA money)
#3: Is there power or money to be gained by the corporate rich by publishing this story? (Overthrow of Ukraine, Syria, Libya, Iraq, private charter schools)
#4: Are they willing to tell the truth even if the truth isn't popular? (Federal Reserve continuously bailing out failing banks, the labor participation rate, GMO crops and farmers)
#5: Do they provide the underlying links to source documents? Are the links they provide real source documents or are they linked to fake source documents? (The Russian hacking evidence)
#6: Does the information seek to damage our civil liberties or to game the economy against us? (TPP, repealing Glass-Steagal)
Also, I recognize my own bias and don't automatically discount others' views. For example, I still read news from the sites that Prop or Not wants me to read even though I dislike Prop or Not. I'm not saying that all Mainstream news is fake. Just some of it.
Why is this subject so important?
Our rights to free speech hanging by a thread. In addition to Prop or Not's black listing 200 websites, the federal government has just granted $160 million to create, as part of the 2017 National Defense Authorization Act, a center to combat propaganda aimed against the U.S. (You'd wonder why anyone in the middle east might hold some anger against the U.S.) Here is part of a recent article from Alternet:
Obama Just Signed off on a Shadowy New 'Anti-Propaganda' Center That Will Be Handed Over to Trump
Without meaningful debate, the provision was included in the 2017 defense bill.
By Sarah Lazare / AlterNet
December 30, 2016
“….Termed the Global Engagement Center, the body is granted broad and ill-defined powers to surveil the “populations most susceptible to propaganda,” compile reporting and social media messaging critical of the U.S. government and disseminate pro-American propaganda… (Also) The language indicates that federal authorities will have a new mechanism for monitoring social media and reporting that is critical of the U.S. government.”
See http://www.alternet.org/human-rights/obama-just-signed-shadowy-new-anti-propaganda-center-will-be-handed-over-trump
The legislation to create this Global Engagement Center had been in the works since June of this year, well before the election. We can only wonder what else has been and is in the works to be launched against both the American people and people worldwide. I'll tell you one thing that has been in the works - tensions against Russia.
Another Example of the Need for Independent Media
Today at the gym I was watching the TV while on the treadmill and all of the mainstream channels were talking about the Russians hacking into…. Then when I came home I read an article by Glenn Greenwald, a very trusted journalist who I've read for years and who I've never seen lie.
https://theintercept.com/2016/12/31/russia-hysteria-infects-washpost-again-false-story-about-hacking-u-s-electric-grid/
In this article, Greenwald reviews the false claims made by the Washington Post and then says,
“The Post’s story also predictably and very rapidly infected other large media outlets. Reuters thus told its readers around the world: “A malware code associated with Russian hackers has reportedly been detected within the system of a Vermont electric utility.”
WHAT’S THE PROBLEM here? It did not happen. There was no “penetration of the U.S. electricity grid.” The truth was undramatic and banal. Burlington Electric, after receiving a Homeland Security notice sent to all U.S. utility companies about the malware code found in the DNC system, searched all its computers and found the code in a single laptop that was not connected to the electric grid.”
This is why we need Independent Media
Just like with Iraq, the fabled Weapons of Mass Destruction against the US Electric grid was all made up by our recklessly dishonest main stream media. Glenn’s article is proof yet again, that we need to embrace independent news. Great danger lies in believing information because it's shiny. In closing, many of us have been seeing this crackdown on free speech and free thought for years and over the last few weeks it's been amplified. If we allow a controlled media, and police each other for signs of transgression in thought and word, we ourselves will be building up a society which I don't think any of us really wants.
About the author:
Elizabeth Hanson M. Ed. Is a college instructor from Seattle Washington and co-founder of turningpointnews.org. She is also a co-author of the book, “Weapons of Mass Deception, The War against our public schools.” https://weaponsofmassdeception.org/
Elizabeth can be reached atThis email address is being protected from spambots. You need JavaScript enabled to view it.
January 1, 2017
In this article I compare the headlines of mainstream news to the headlines of independent news as an example of why we need independent news. I also give suggestions on how to ascertain the truth when reading news articles on the Internet.
In November of 2016, the Washington Post published a blacklist of 200 websites which they deem as promoting Russian propaganda and thus dangerous to U.S. consumers of news. It was published by a group called “Prop or Not”.
https://www.washingtonpost.com/business/economy/russian-propaganda-effort-helped-spread-fake-news-during-election-experts-say/2016/11/24/793903b6-8a40-4ca9-b712-716af66098fe_story.html?utm_term=.3a6e770f8ac7
Here's the link to the Prop or Not list -http://www.propornot.com/p/home.html
The Washington Post has many excellent reporters and has published some great stories over the years, so when I first heard about this list, I thought “Oh… it probably lists some sites like Russia Today (RT), sites directly related to Russia.
However, much to my surprise upon reading their list of propaganda websites, I found that the Prop or Not list contains the ten websites I have read almost daily for many years. Here in alphabetical order:
#1: Black Agenda Report
#2: Consortium news
#3: Counterpunch
#4: Global Research
#5: Naked Capitalism
#6: Oped news
#7: Truthdig
#8: Truthout
#9 Washingtonsblog
#10: Zerohedge
The Washington Post's Prop or Not team also provides us with this graphic to scare the living bejesus out of people, in hopes, I assume, to deter Americans from visiting any of the sites they deem as propaganda and to show us that they mean business:

The team at Prop or Not then goes on to tell us that we should be reading news from these main stream media news sources instead of independent news sources. Here is a quote from their website:
“Obtain news from actual reporters, who report to an editor and are professionally accountable for mistakes. We suggest NPR, the BBC, the New York Times, the Wall Street Journal, the Washington Post, Buzzfeed News, VICE, etc, and especially your local papers and local TV news channels. Support them by subscribing, if you can!”
Comparing Headlines of Prop or Not Approved Sites versus Independent News Sites
Here's a look of some of their recent headlines of Prop or Not's trusted media sources regarding Russian hacking and the subsequent sanctions Obama is putting on Russia.
NPR: “US. Officials Say Russia Hacked A Vermont Utility”
New York Times: “U.S. Sanctions Russia Over Election Hacking”
Wall Street Journal: “Obama Strikes Back at Russia for Election Hacking”
Washington Post: Obama administration announces measures to punish Russia for 2016 election interference
These mainstream news headlines are being widely read by Americans and will likely have the effect of pushing most Americans into agreeing with sanctions and perhaps further aggressions against Russia.
We saw how believing in weapons of mass deception led to aggressions against Iraq and resulted in well over 100,000 civilian deaths between 2003 and 2010.

http://www.bbc.com/news/world-middle-east-11107739
And there were no weapons of mass destruction found. Ever since 9 / 11, millions of Americans have become disillusioned with the mainstream news, and its framing of news related to subjects like trade agreements, foreign policy, banker misdeeds, the economy and education have been reading news from independent media.
Let's compare those “ra-ra sanctions against Russia” headlines to the headlines in some of the independent media Americans read which are on the Prop or Not list:
Black Agenda Report - “Freedom Rider: Syria, Russia and American Desperation”
Consortium news - “Details Still Lacking on Russian ‘Hack”
Counterpunch - “We Do Not Live in “Post Truth” World, We Live in a World of Lies and We Always Have”
Global Research- “Obama’s Sanctions against Moscow “Intended to Box In Donald Trump”. Evidence that Hacking of DNC Accusations are Fake”
Opednews - “DHS FBI Claim of Russian Hacking is Fake News”
Truthdig - “Experts Aren’t Convinced by FBI and Homeland Security Report on Alleged Russian Hacking”
Washingtonsblog - “Creator of NSA's Global Surveillance System Calls B.S. On Russian Hacking Report”
Zerohedge - "Something Stinks" - Like Iraq WMD Fiasco, Russia Story Doesn't Add Up
While the mainstream media reported the Russian Hacker story as if it were the truth, alternative news sources reported why the Russian Hacker story might not be true.
Six Principles for Evaluation the Truth
I'm a teacher with a background in Linguistics. An always interesting question to answer with my students is how do you know if a media source is telling the truth?
I follow these six principles:
#1: Have they told the truth in the past? (Weapons of mass destruction, Economic recovery)
#2: Who is funding the site? (Gates money, CIA money)
#3: Is there power or money to be gained by the corporate rich by publishing this story? (Overthrow of Ukraine, Syria, Libya, Iraq, private charter schools)
#4: Are they willing to tell the truth even if the truth isn't popular? (Federal Reserve continuously bailing out failing banks, the labor participation rate, GMO crops and farmers)
#5: Do they provide the underlying links to source documents? Are the links they provide real source documents or are they linked to fake source documents? (The Russian hacking evidence)
#6: Does the information seek to damage our civil liberties or to game the economy against us? (TPP, repealing Glass-Steagal)
Also, I recognize my own bias and don't automatically discount others' views. For example, I still read news from the sites that Prop or Not wants me to read even though I dislike Prop or Not. I'm not saying that all Mainstream news is fake. Just some of it.
Why is this subject so important?
Our rights to free speech hanging by a thread. In addition to Prop or Not's black listing 200 websites, the federal government has just granted $160 million to create, as part of the 2017 National Defense Authorization Act, a center to combat propaganda aimed against the U.S. (You'd wonder why anyone in the middle east might hold some anger against the U.S.) Here is part of a recent article from Alternet:
Obama Just Signed off on a Shadowy New 'Anti-Propaganda' Center That Will Be Handed Over to Trump
Without meaningful debate, the provision was included in the 2017 defense bill.
By Sarah Lazare / AlterNet
December 30, 2016
“….Termed the Global Engagement Center, the body is granted broad and ill-defined powers to surveil the “populations most susceptible to propaganda,” compile reporting and social media messaging critical of the U.S. government and disseminate pro-American propaganda… (Also) The language indicates that federal authorities will have a new mechanism for monitoring social media and reporting that is critical of the U.S. government.”
See http://www.alternet.org/human-rights/obama-just-signed-shadowy-new-anti-propaganda-center-will-be-handed-over-trump
The legislation to create this Global Engagement Center had been in the works since June of this year, well before the election. We can only wonder what else has been and is in the works to be launched against both the American people and people worldwide. I'll tell you one thing that has been in the works - tensions against Russia.
Another Example of the Need for Independent Media
Today at the gym I was watching the TV while on the treadmill and all of the mainstream channels were talking about the Russians hacking into…. Then when I came home I read an article by Glenn Greenwald, a very trusted journalist who I've read for years and who I've never seen lie.
https://theintercept.com/2016/12/31/russia-hysteria-infects-washpost-again-false-story-about-hacking-u-s-electric-grid/

In this article, Greenwald reviews the false claims made by the Washington Post and then says,
“The Post’s story also predictably and very rapidly infected other large media outlets. Reuters thus told its readers around the world: “A malware code associated with Russian hackers has reportedly been detected within the system of a Vermont electric utility.”
WHAT’S THE PROBLEM here? It did not happen. There was no “penetration of the U.S. electricity grid.” The truth was undramatic and banal. Burlington Electric, after receiving a Homeland Security notice sent to all U.S. utility companies about the malware code found in the DNC system, searched all its computers and found the code in a single laptop that was not connected to the electric grid.”
This is why we need Independent Media
Just like with Iraq, the fabled Weapons of Mass Destruction against the US Electric grid was all made up by our recklessly dishonest main stream media. Glenn’s article is proof yet again, that we need to embrace independent news. Great danger lies in believing information because it's shiny. In closing, many of us have been seeing this crackdown on free speech and free thought for years and over the last few weeks it's been amplified. If we allow a controlled media, and police each other for signs of transgression in thought and word, we ourselves will be building up a society which I don't think any of us really wants.
About the author:
Elizabeth Hanson M. Ed. Is a college instructor from Seattle Washington and co-founder of turningpointnews.org. She is also a co-author of the book, “Weapons of Mass Deception, The War against our public schools.” https://weaponsofmassdeception.org/
Elizabeth can be reached at
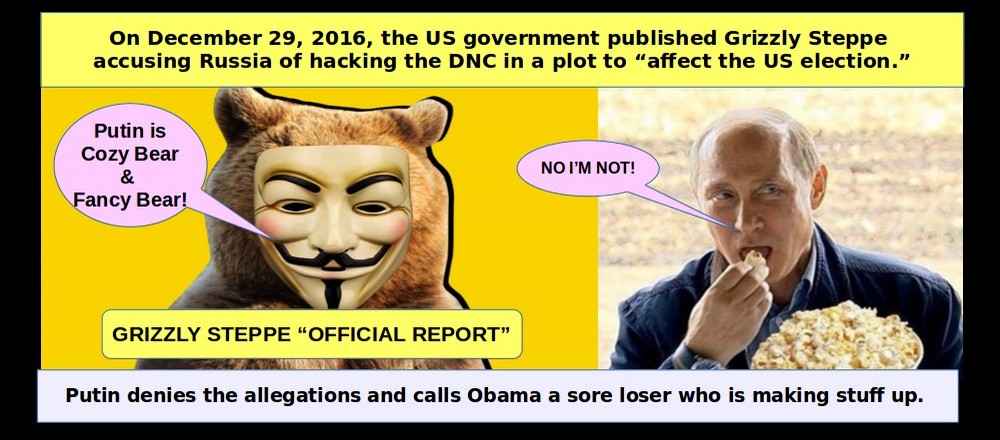
On December 29, 2016, the Hill posted an article discussing a 13 page report by the FBI and DHS claiming that their 13 page report was “evidence” of Russian hacking in US elections.
http://thehill.com/policy/national-security/312132-fbi-dhs-release-report-on-russia-hacking
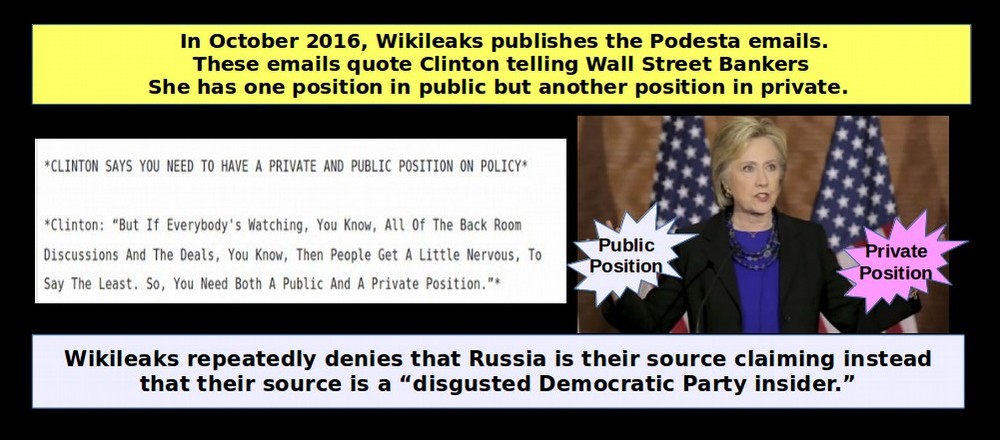
Wikileaks has repeatedly stated that the source of its leaks was a disgruntled Democratic Party insider.
http://www.dailymail.co.uk/news/article-4034038/Ex-British-ambassador-WikiLeaks-operative-claims-Russia-did-NOT-provide-Clinton-emails-handed-D-C-park-intermediary-disgusted-Democratic-insiders.html
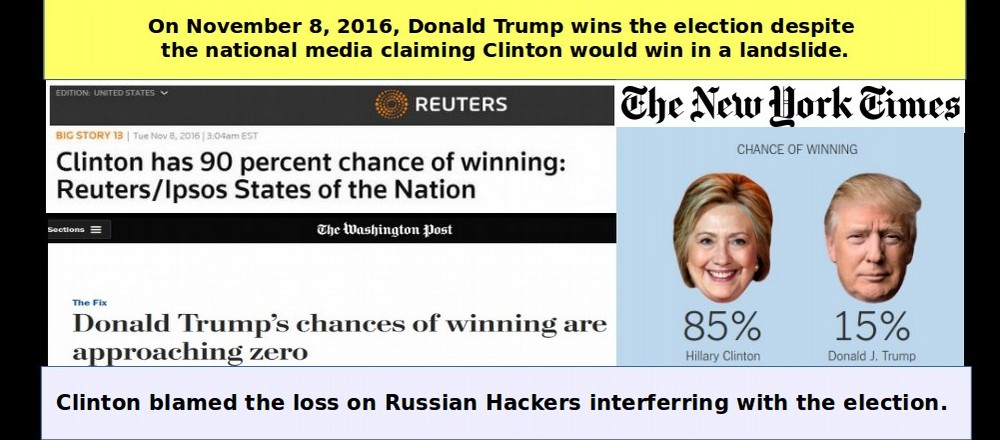
However, President Obama issued a press release on December 29 2016 using the DHS-FBI report to justify increasing sanctions against Russia.
https://www.whitehouse.gov/the-press-office/2016/12/29/statement-president-actions-response-russian-malicious-cyber-activity
I therefore decided to see what the evidence was of Russian involvement in US Elections. The Hill article linked to this 13 page government press release as its proof of Russian hacking.
https://www.us-cert.gov/sites/default/files/publications/JAR_16-20296.pdf
The government press release written by DHS-FBI did not mention Wikileaks in its report. Nor did the report provide any evidence of Russian hacking in the US elections. Instead, the press release stated that “technical indicators” of Russian hacking were in the “CSV file and XML file attached with the PDF.” However, there was no CSV or XML file or link attached with the PDF. I was eventually able to find these two files at this link.
https://www.us-cert.gov/security-publications/GRIZZLY-STEPPE-Russian-Malicious-Cyber-Activity
To see the evidence of Russian hacking first hand, I downloaded the CSV file and converted it into a spreadsheet. The CSV file and the XML file both contained the same data. Here is the XML link to this data which can be viewed online in a web browser.
https://www.us-cert.gov/sites/default/files/publications/JAR-16-20296.xml
Both files provide a list of 895 “indicators” of Russian Hacking. Unfortunately, nearly all of these indicators are simply IP addresses. In other words, it is a list of 895 servers from from more than 40 countries around the world. But the list also includes a few website domain names. (Domain names are simply the name of the website such as Youtube.com). I looked up these website domain names with the the following tool which tells us who owns the domain names and where they are located:
https://www.whois.net/
My review of these domain names confirmed that none of these domain names have any relationship to Russian government hackers. Here are the results for four of the domain names provided by the DHS and the FBI as evidence of Russian hacking:
ritsoperrol.ru is not in use. It is registered to a private person. The named server hosting the domain is nserver: ns0.xtremeweb.de. This is a German web hosting and consulting company whose address and phone number are publicly listed on their website. It is highly unlikely that Russian hackers would use a public German web host to register and host their domain names.
littlejohnwilhap.ru is not in use and is available to be purchased. It is unlikely that Russian hackers would use a domain name like this to launch a cyber attack on the US.
wilcarobbe.com is taken and is not in use. It is registered to Arsen Ramanov in Groznenskaya Russia. His address, phone number and email address are all publicly listed. It is highly unlikely that Russian hackers would use a domain name that was publicly listed. Hackers are not idiots.
one2shoppee.com is taken and is registered with GoDaddy.com. It is not currently in use. But it is highly unlikely that Russian Hackers would register their domain names with GoDaddy – which is a US server. In fact, it is very unlikely that Russian hackers would ever use any US servers. They would only use their own servers.
How did these four domain names get on a list of Russian hackers? It is possible that some unknown agents took over these domain names and may have used them for some kind of hacking activity. However, the agents could have just as easily been from the US as from Russia. In fact, it is not likely that these domain names were taken over by Russian hackers for the simple reason that Russian hackers are way too smart to be using these silly tactics.
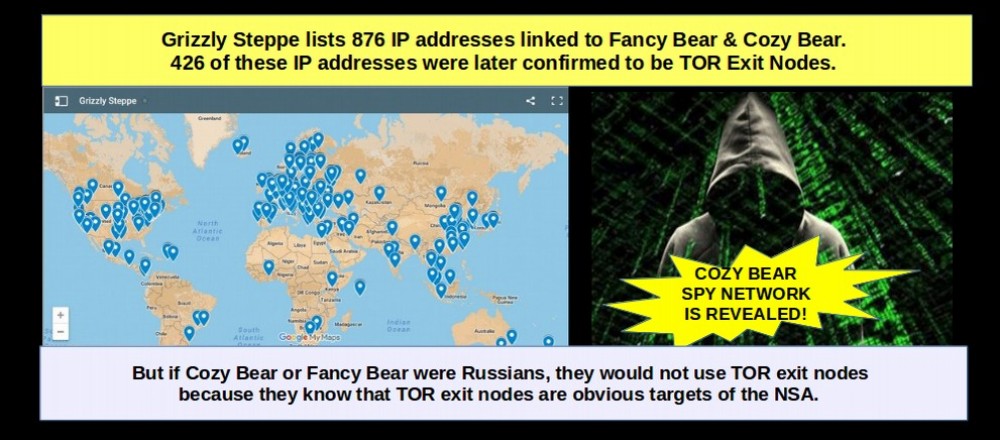
None of the 885 IP addresses have any confirmed relationship to Russian Government Hackers
An IP address is simply a numerical designation for a server. The 885 IP addresses listed in the DHS – FBI CSV file were even more interesting. The IP addresses were located on servers from the US and more than 40 nations around the world including more than 30 IP addresses supposedly located in China. Here are a few of the IP addresses
167.114.35.70
185.12.46.178
46.102.152.132
178.20.55.16
I looked up several of these IP addresses using the following tool:
http://whatismyipaddress.com/ip-lookup
Here are a four examples of IP addresses in the DHS-FBI report:
167.114.35.70 is a Canadian Corporate server specializing in the promotion of Bitcoin. They are within a few miles of the US border.
185.12.46.178 is a Swiss corporate server associated with the domain name leavesorus.com. The domain name leavesorus.com is currently available to be purchased. This indicates that this is a fake domain name and likely a fake corporation.
46.102.152.132 is another Swiss corporate server this one specializing in emails and associated with the domain name maxsultan.xyz which is a fake domain name. This also indicates that this is another fake corporation.
178.20.55.16 is a proxy server with no known location but has been used as a TOR router exit node. A proxy server is another name for a mirror or server used to bounce information from one server to another in order to hide the true location of the original server. This proxy server is associated with the domain name nos-oignons.net. This domain name was registered on December 31 2012 and is valid until December 31 2017. In other words, whoever got this domain name paid for its use for 5 years. But they did registered the domain name anonymously. The website associated with this server appears to be a group in France promoting the TOR router. They became an association in May 2013 – 5 months after getting the domain name. The group currently has 5 members and it costs one Euro to join this group. Their website was reported 9 days ago as having been infected with the Zues virus. This infection does not leave tracks on server logs. So it is difficult to tell where it came from. Removal of this virus requires a complete rebuild of the server. In short, some agency decided to take out this server and then use it to make a cyber attack on some US government agency and thus have the IP address listed on the DHS-FBI list as one of 895 indicators of Russian hacking.
Many of the IP addresses yielded the same dead end or otherwise highly suspicious result - meaning that some very large agency is using hundreds of servers in various countries around the world as a front for hacking attacks. I recently researched a series of attacks on my personal websites from hundreds of IP addresses using hundreds of servers that were supposedly located in the Ukraine. I was able to confirm the exact location in the Ukraine that was supposedly being used to launch literally thousands of attacks on my websites. However, it is not credible that anyone in the Ukraine has the millions of dollars needed to be running hundreds of servers in a remote Ukrainian location. Nor is it likely that anyone in rural Ukraine would even have the knowledge to take care of hundreds of servers even if they did have the millions of dollars needed to plow into buying these servers. Nor are they likely to have the knowledge needed to be running very complex cyber attacks. Ukraine is just not a good location for servers. This experience convinced me that attacks were being launched from other locations and were merely being routed through Ukraine in order to mislead people about where the attacks were really coming from.
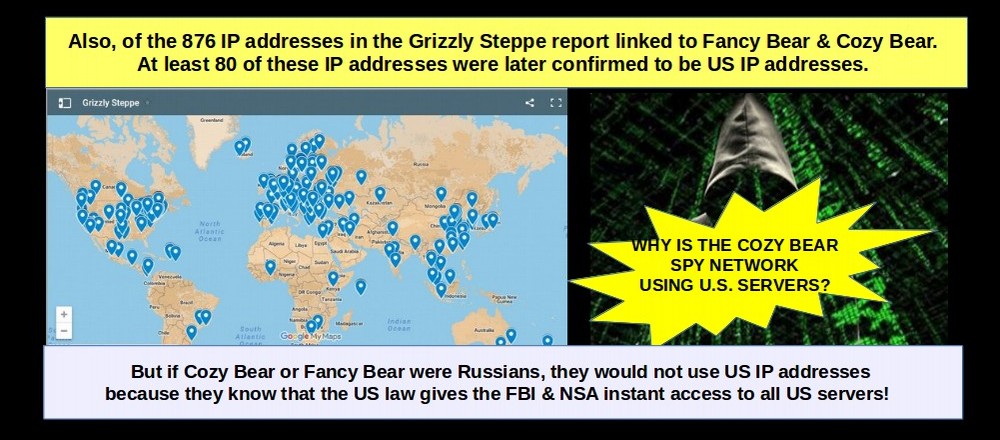
Next, the CSV file provided by DHS-FBI listed the physical location of all 885 IP addresses. What is most ironic is that, only two of the 885 IP addresses were from servers in Russia. The most common location of the hacking servers was the United States. Over 30 of the servers were supposedly located in China. But it is known that the NSA has the ability to use satellite mirrors to hide the locations of their servers – making folks believe that the attacks are coming from China (or Ukraine or Mongolia) when in fact they are coming from servers located in the US.
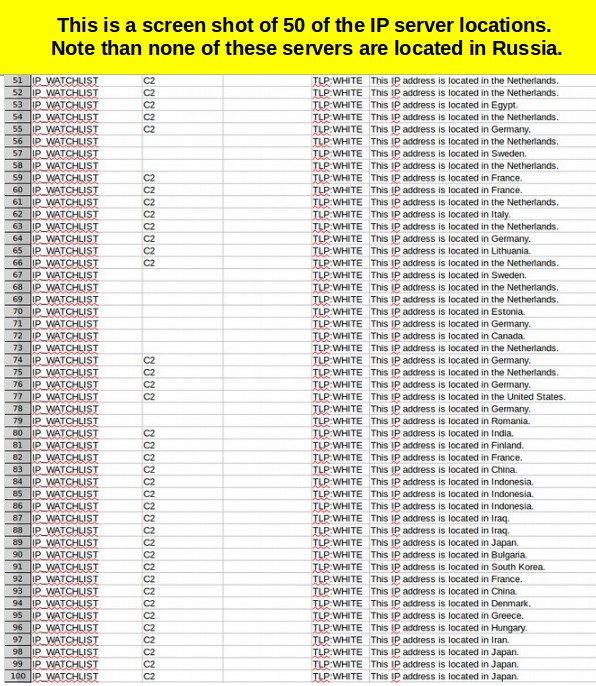
Here are 50 more servers. Again, no Russians:
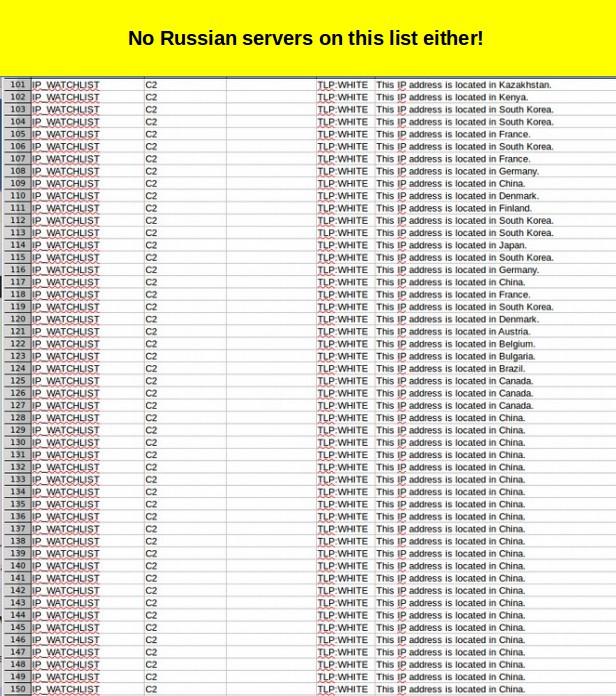
Here are 50 more servers. How can servers in the US be used as evidence of Russian hacking?
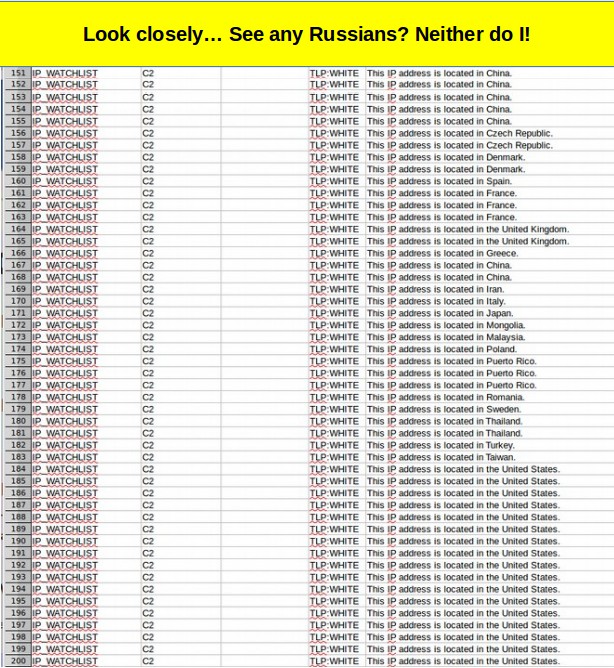
Here is another batch of 50 servers. Again, no Russians.
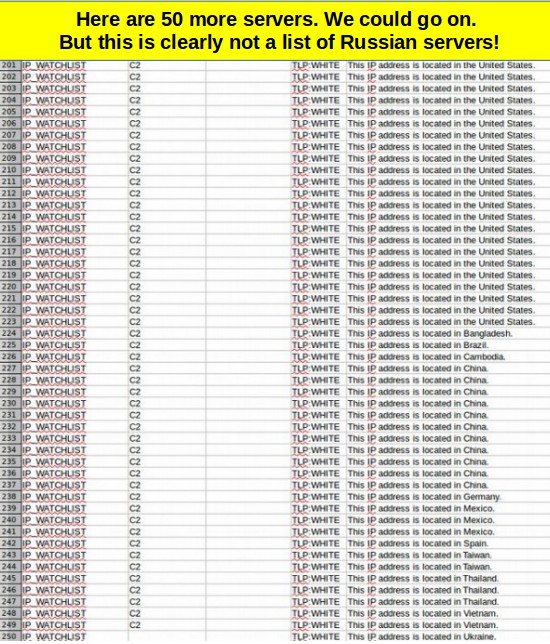
Wait a Minute… Is this the Smoking Gun???
Actually, there were two Russian servers located on lines 259 and 261. Here are the IP addresses.
93.171.203.244
95.105.72.78
Here is more information about each of these:
93.171.203.244 This is a clean broadband server located near Ufa which is a city in Russia with one million people. It is associated with an organization called Miragroup Ltd. The website is rxbrothers.ru. Naturally, this is a fake domain name which is available to be purchased. Miragroup is actually a corporation located in Great Britain.
95.105.72.78 is another clean broadband server located near Ufa. The organization is JSC Ufanet and the website is ufanet.ru which is a public broadband service started in 1997. Someone apparently is using this broadband service to hack the US government. Could this be the smoking gun that the Russian government is attacking the US? Think about it. If you were a Russian hacker, would you really use a public server located in some Russian town? I don’t think so. This is more like evidence that some hacker was using the local public library.
Imagine someone launching a cyber attack from the Seattle Public library – and then our government declaring that they have evident that the mayor of the City of Seattle was responsible for the attack because “nothing happens in Seattle without the approval of the Mayor!”. This is worse than a silly accusation. It is ridiculous. It is irresponsible.
Real Russian Hackers do not use Windows Servers
Only three of the servers provided in the DHS/FBI report included detailed information (despite the fact that the IP addresses provided information on all 895 servers and that DHS/FBI certainly have detailed information on all of the servers). All three servers listed in the report were Windows servers. It is highly unlikely that Russian hackers or Chinese hackers would be using Windows servers. Instead, all real hackers use Linux servers because Linux servers are much more secure than Windows servers.
https://techlog360.com/top-15-favourite-operating-systems-of-hackers/
If there really was evidence of Russian hacking, the NSA would have it
Former NSA leader turned whistleblower William Binney recently stated that if the Russians really did hack the Democratic Party servers, the NSA would certainly have real evidence (not the nonsense put out in the DHS-FBI CSV file). Here is his quote from a December 29 2016 article by Glenn Greenwald: “The bottom line is that the NSA would know where and how any “hacked” emails from the DNC, HRC or any other servers were routed through the network. This process can sometimes require a closer look into the routing to sort out intermediate clients, but in the end sender and recipient can be traced across the network.”
https://theintercept.com/2016/12/29/top-secret-snowden-document-reveals-what-the-nsa-knew-about-previous-russian-hacking/
Edward Snowden has not only confirmed that the NSA has this ability – but that he himself used an NSA program called XKEYSCORE to monitor such attacks.
https://theintercept.com/2016/07/26/russian-intelligence-hack-dnc-nsa-know-snowden-says/
Anyone with any kind of technical background in defending against hacker attacks would understand that what Binney, Snowden and Greenwald are saying is true. The evidence of their truth – most of which was supplied by Snowden from NSA documents – is overwhelming.

Conclusion
An important research principle is to follow the money. People around the world need to ask themselves who has the money and technical ability to be running hundreds and perhaps thousands of real servers and real IP addresses from fake corporations using fake websites in fake locations in more than 40 nations around the world? What agency has already been proven to be running mass surveillance on billions of people in more than 40 nations all around the world? Whose military cyber budget is more than 10 times larger than the cyber warfare budget of the rest of the world combined? There is certainly an elephant in the room – but it is not a Russian elephant.
At a televised press conference on April 2016, former NSA agent, Edward Snowden asked the Russian leader Vladimir Putin if the Russian government engaged in mass surveillance of millions of people in a manner similar to the NSA. Putin replied that Russian law prohibited the Russian government from engaging in mass surveillance. Putin then pointed out that the Russian military budget was less than 10% of the US military budget. So even if they wanted to engage in mass surveillance, they simply did not have the money.
https://www.theguardian.com/world/video/2014/apr/17/snowden-putin-russia-surveillance-phone-in-video
People also need to ask themselves why the FBI DHS chose to place their evidence in a CSV file and XML file rather than a normal document or spreadsheet. If this were real evidence, it would have been placed directly in the PDF report for everyone to read – not hidden away in a file the general public has little ability to read.
Finally, for the FBI or the DHS to claim that the XML-CSV file contains evidence or even indicators of Russian hacking is simply a false statement. It is a perfect example of fake news. Any news agency promoting this claim without doing even the most basic of research that would easily confirm it is false, should be listed as a fake news agency.
The real question that we should all be asking is why the DHS and FBI would destroy their reputation by posting such a fake report?
Several years ago, our CIA claimed that Iraq had weapons of mass destruction. We now know that Iraq had no weapons of mass destruction – meaning that we went to war and spent over a trillion dollars on a fake report. Is this new fake report a pretext for launching a cyber war against Russia? Is it intended to justify increasing US military spending?
It is hard to say what the real purpose of this fake DHS-FBI report is. But the fact that this silly list of IP addresses was the best evidence they could provide should be a strong indication that there really is no evidence of Russian hacking. Instead, it is more likely that Wikileaks is telling the truth in stating that they got the emails from a disgruntled Democratic Party insider.

About the author
David Spring M. Ed. is a retired college instructor from Seattle Washington who specializes in website design and security. David recently founded an independent news site called Turning Point News.org in order to speak truth to power and shine a light in the darkness. You can reach david at the following email address:This email address is being protected from spambots. You need JavaScript enabled to view it.
http://thehill.com/policy/national-security/312132-fbi-dhs-release-report-on-russia-hacking
Wikileaks has repeatedly stated that the source of its leaks was a disgruntled Democratic Party insider.
http://www.dailymail.co.uk/news/article-4034038/Ex-British-ambassador-WikiLeaks-operative-claims-Russia-did-NOT-provide-Clinton-emails-handed-D-C-park-intermediary-disgusted-Democratic-insiders.html
However, President Obama issued a press release on December 29 2016 using the DHS-FBI report to justify increasing sanctions against Russia.
https://www.whitehouse.gov/the-press-office/2016/12/29/statement-president-actions-response-russian-malicious-cyber-activity
I therefore decided to see what the evidence was of Russian involvement in US Elections. The Hill article linked to this 13 page government press release as its proof of Russian hacking.
https://www.us-cert.gov/sites/default/files/publications/JAR_16-20296.pdf
The government press release written by DHS-FBI did not mention Wikileaks in its report. Nor did the report provide any evidence of Russian hacking in the US elections. Instead, the press release stated that “technical indicators” of Russian hacking were in the “CSV file and XML file attached with the PDF.” However, there was no CSV or XML file or link attached with the PDF. I was eventually able to find these two files at this link.
https://www.us-cert.gov/security-publications/GRIZZLY-STEPPE-Russian-Malicious-Cyber-Activity
To see the evidence of Russian hacking first hand, I downloaded the CSV file and converted it into a spreadsheet. The CSV file and the XML file both contained the same data. Here is the XML link to this data which can be viewed online in a web browser.
https://www.us-cert.gov/sites/default/files/publications/JAR-16-20296.xml
Both files provide a list of 895 “indicators” of Russian Hacking. Unfortunately, nearly all of these indicators are simply IP addresses. In other words, it is a list of 895 servers from from more than 40 countries around the world. But the list also includes a few website domain names. (Domain names are simply the name of the website such as Youtube.com). I looked up these website domain names with the the following tool which tells us who owns the domain names and where they are located:
https://www.whois.net/
My review of these domain names confirmed that none of these domain names have any relationship to Russian government hackers. Here are the results for four of the domain names provided by the DHS and the FBI as evidence of Russian hacking:
ritsoperrol.ru is not in use. It is registered to a private person. The named server hosting the domain is nserver: ns0.xtremeweb.de. This is a German web hosting and consulting company whose address and phone number are publicly listed on their website. It is highly unlikely that Russian hackers would use a public German web host to register and host their domain names.
littlejohnwilhap.ru is not in use and is available to be purchased. It is unlikely that Russian hackers would use a domain name like this to launch a cyber attack on the US.
wilcarobbe.com is taken and is not in use. It is registered to Arsen Ramanov in Groznenskaya Russia. His address, phone number and email address are all publicly listed. It is highly unlikely that Russian hackers would use a domain name that was publicly listed. Hackers are not idiots.
one2shoppee.com is taken and is registered with GoDaddy.com. It is not currently in use. But it is highly unlikely that Russian Hackers would register their domain names with GoDaddy – which is a US server. In fact, it is very unlikely that Russian hackers would ever use any US servers. They would only use their own servers.
How did these four domain names get on a list of Russian hackers? It is possible that some unknown agents took over these domain names and may have used them for some kind of hacking activity. However, the agents could have just as easily been from the US as from Russia. In fact, it is not likely that these domain names were taken over by Russian hackers for the simple reason that Russian hackers are way too smart to be using these silly tactics.
None of the 885 IP addresses have any confirmed relationship to Russian Government Hackers
An IP address is simply a numerical designation for a server. The 885 IP addresses listed in the DHS – FBI CSV file were even more interesting. The IP addresses were located on servers from the US and more than 40 nations around the world including more than 30 IP addresses supposedly located in China. Here are a few of the IP addresses
167.114.35.70
185.12.46.178
46.102.152.132
178.20.55.16
I looked up several of these IP addresses using the following tool:
http://whatismyipaddress.com/ip-lookup
Here are a four examples of IP addresses in the DHS-FBI report:
167.114.35.70 is a Canadian Corporate server specializing in the promotion of Bitcoin. They are within a few miles of the US border.
185.12.46.178 is a Swiss corporate server associated with the domain name leavesorus.com. The domain name leavesorus.com is currently available to be purchased. This indicates that this is a fake domain name and likely a fake corporation.
46.102.152.132 is another Swiss corporate server this one specializing in emails and associated with the domain name maxsultan.xyz which is a fake domain name. This also indicates that this is another fake corporation.
178.20.55.16 is a proxy server with no known location but has been used as a TOR router exit node. A proxy server is another name for a mirror or server used to bounce information from one server to another in order to hide the true location of the original server. This proxy server is associated with the domain name nos-oignons.net. This domain name was registered on December 31 2012 and is valid until December 31 2017. In other words, whoever got this domain name paid for its use for 5 years. But they did registered the domain name anonymously. The website associated with this server appears to be a group in France promoting the TOR router. They became an association in May 2013 – 5 months after getting the domain name. The group currently has 5 members and it costs one Euro to join this group. Their website was reported 9 days ago as having been infected with the Zues virus. This infection does not leave tracks on server logs. So it is difficult to tell where it came from. Removal of this virus requires a complete rebuild of the server. In short, some agency decided to take out this server and then use it to make a cyber attack on some US government agency and thus have the IP address listed on the DHS-FBI list as one of 895 indicators of Russian hacking.
Many of the IP addresses yielded the same dead end or otherwise highly suspicious result - meaning that some very large agency is using hundreds of servers in various countries around the world as a front for hacking attacks. I recently researched a series of attacks on my personal websites from hundreds of IP addresses using hundreds of servers that were supposedly located in the Ukraine. I was able to confirm the exact location in the Ukraine that was supposedly being used to launch literally thousands of attacks on my websites. However, it is not credible that anyone in the Ukraine has the millions of dollars needed to be running hundreds of servers in a remote Ukrainian location. Nor is it likely that anyone in rural Ukraine would even have the knowledge to take care of hundreds of servers even if they did have the millions of dollars needed to plow into buying these servers. Nor are they likely to have the knowledge needed to be running very complex cyber attacks. Ukraine is just not a good location for servers. This experience convinced me that attacks were being launched from other locations and were merely being routed through Ukraine in order to mislead people about where the attacks were really coming from.
Next, the CSV file provided by DHS-FBI listed the physical location of all 885 IP addresses. What is most ironic is that, only two of the 885 IP addresses were from servers in Russia. The most common location of the hacking servers was the United States. Over 30 of the servers were supposedly located in China. But it is known that the NSA has the ability to use satellite mirrors to hide the locations of their servers – making folks believe that the attacks are coming from China (or Ukraine or Mongolia) when in fact they are coming from servers located in the US.

Here are 50 more servers. Again, no Russians:

Here are 50 more servers. How can servers in the US be used as evidence of Russian hacking?

Here is another batch of 50 servers. Again, no Russians.

Wait a Minute… Is this the Smoking Gun???
Actually, there were two Russian servers located on lines 259 and 261. Here are the IP addresses.
93.171.203.244
95.105.72.78
Here is more information about each of these:
93.171.203.244 This is a clean broadband server located near Ufa which is a city in Russia with one million people. It is associated with an organization called Miragroup Ltd. The website is rxbrothers.ru. Naturally, this is a fake domain name which is available to be purchased. Miragroup is actually a corporation located in Great Britain.
95.105.72.78 is another clean broadband server located near Ufa. The organization is JSC Ufanet and the website is ufanet.ru which is a public broadband service started in 1997. Someone apparently is using this broadband service to hack the US government. Could this be the smoking gun that the Russian government is attacking the US? Think about it. If you were a Russian hacker, would you really use a public server located in some Russian town? I don’t think so. This is more like evidence that some hacker was using the local public library.
Imagine someone launching a cyber attack from the Seattle Public library – and then our government declaring that they have evident that the mayor of the City of Seattle was responsible for the attack because “nothing happens in Seattle without the approval of the Mayor!”. This is worse than a silly accusation. It is ridiculous. It is irresponsible.
Real Russian Hackers do not use Windows Servers
Only three of the servers provided in the DHS/FBI report included detailed information (despite the fact that the IP addresses provided information on all 895 servers and that DHS/FBI certainly have detailed information on all of the servers). All three servers listed in the report were Windows servers. It is highly unlikely that Russian hackers or Chinese hackers would be using Windows servers. Instead, all real hackers use Linux servers because Linux servers are much more secure than Windows servers.
https://techlog360.com/top-15-favourite-operating-systems-of-hackers/
If there really was evidence of Russian hacking, the NSA would have it
Former NSA leader turned whistleblower William Binney recently stated that if the Russians really did hack the Democratic Party servers, the NSA would certainly have real evidence (not the nonsense put out in the DHS-FBI CSV file). Here is his quote from a December 29 2016 article by Glenn Greenwald: “The bottom line is that the NSA would know where and how any “hacked” emails from the DNC, HRC or any other servers were routed through the network. This process can sometimes require a closer look into the routing to sort out intermediate clients, but in the end sender and recipient can be traced across the network.”
https://theintercept.com/2016/12/29/top-secret-snowden-document-reveals-what-the-nsa-knew-about-previous-russian-hacking/
Edward Snowden has not only confirmed that the NSA has this ability – but that he himself used an NSA program called XKEYSCORE to monitor such attacks.
https://theintercept.com/2016/07/26/russian-intelligence-hack-dnc-nsa-know-snowden-says/
Anyone with any kind of technical background in defending against hacker attacks would understand that what Binney, Snowden and Greenwald are saying is true. The evidence of their truth – most of which was supplied by Snowden from NSA documents – is overwhelming.

Conclusion
An important research principle is to follow the money. People around the world need to ask themselves who has the money and technical ability to be running hundreds and perhaps thousands of real servers and real IP addresses from fake corporations using fake websites in fake locations in more than 40 nations around the world? What agency has already been proven to be running mass surveillance on billions of people in more than 40 nations all around the world? Whose military cyber budget is more than 10 times larger than the cyber warfare budget of the rest of the world combined? There is certainly an elephant in the room – but it is not a Russian elephant.
At a televised press conference on April 2016, former NSA agent, Edward Snowden asked the Russian leader Vladimir Putin if the Russian government engaged in mass surveillance of millions of people in a manner similar to the NSA. Putin replied that Russian law prohibited the Russian government from engaging in mass surveillance. Putin then pointed out that the Russian military budget was less than 10% of the US military budget. So even if they wanted to engage in mass surveillance, they simply did not have the money.
https://www.theguardian.com/world/video/2014/apr/17/snowden-putin-russia-surveillance-phone-in-video
People also need to ask themselves why the FBI DHS chose to place their evidence in a CSV file and XML file rather than a normal document or spreadsheet. If this were real evidence, it would have been placed directly in the PDF report for everyone to read – not hidden away in a file the general public has little ability to read.
Finally, for the FBI or the DHS to claim that the XML-CSV file contains evidence or even indicators of Russian hacking is simply a false statement. It is a perfect example of fake news. Any news agency promoting this claim without doing even the most basic of research that would easily confirm it is false, should be listed as a fake news agency.
The real question that we should all be asking is why the DHS and FBI would destroy their reputation by posting such a fake report?
Several years ago, our CIA claimed that Iraq had weapons of mass destruction. We now know that Iraq had no weapons of mass destruction – meaning that we went to war and spent over a trillion dollars on a fake report. Is this new fake report a pretext for launching a cyber war against Russia? Is it intended to justify increasing US military spending?
It is hard to say what the real purpose of this fake DHS-FBI report is. But the fact that this silly list of IP addresses was the best evidence they could provide should be a strong indication that there really is no evidence of Russian hacking. Instead, it is more likely that Wikileaks is telling the truth in stating that they got the emails from a disgruntled Democratic Party insider.

About the author
David Spring M. Ed. is a retired college instructor from Seattle Washington who specializes in website design and security. David recently founded an independent news site called Turning Point News.org in order to speak truth to power and shine a light in the darkness. You can reach david at the following email address: