2007: NSA expands its program to actively recruit and train computer hackers.
One of the documents exposed by Snowden in 2013 was a 2007 NSA job posting document in which the NSA actively solicited hackers to go to work for the NSA. The trainees will be taught how to “develop an attackers mindset.” Note that the NSA goal is not merely to monitor computers but to remotely destroy them. http://www.spiegel.de/media/media-35661.pdf

September 1, 2007: The NSA begins the Prism Collection Program.
As confirmed in documents provided by Edward Snowden in 2013, the NSA started the Prism Data Collection Program to enlist major US corporations to help with mass surveillance in 2007. Its first recruit was Microsoft in September 2007.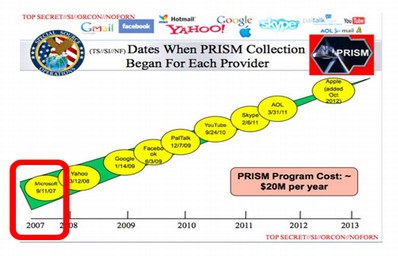
This was also the time that the startup program for all computers except Chromebooks began to change from the simple BIOS program to a complex encrypted program called UEFI. This means that not only is the operating system insecure but so is the startup program as both call back to Microsoft and the NSA using hidden backdoors.
Chromebooks use a much safer startup program called Coreboot that does not have hidden backdoors. I began researching these backdoors in 2010 in order to understand a virus called the Flame virus. I discovered that these backdoors were being used to transmit cyber weapons such as Stuxnet and Flame. I eventually learned that these cyber weapons were created by the NSA.
September 2009: Researching the history of the flame virus led to even more disturbing questions about the relationship between Microsoft and the NSA. Several newspaper reports confirmed that in 2009, Microsoft played a key role in the NSA attack on Iranian Nuclear and Oil Facilities via the development of the Stuxnet and Flame super viruses.

The Stuxnet - Flame viruses soon escaped “into the wild” and began crashing not just Iranian oil facilities but lots of other oil facilities around the world.
http://arstechnica.com/tech-policy/2012/06/confirmed-us-israel-created-stuxnet-lost-control-of-it/
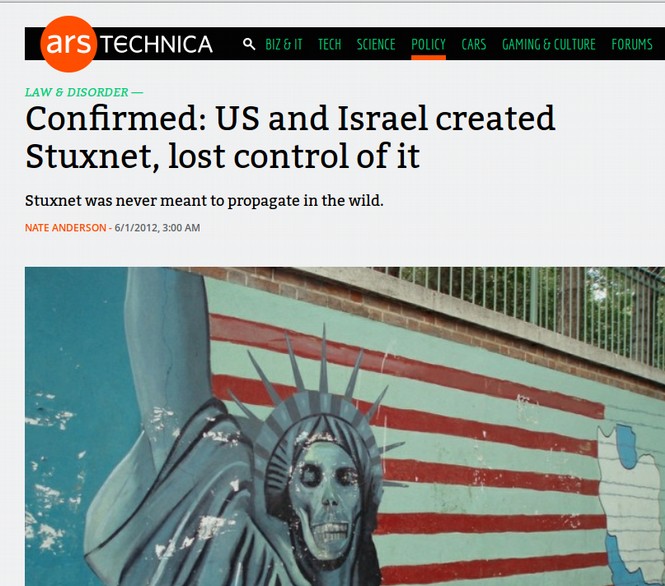
| “Flame was designed to masquerade as a routine Microsoft Update.” http://articles.washingtonpost.com/2012-06-19/world/35460741_1_stuxnet-computer-virus-malware |
Here is a 2 minute video about the dangers of the Stuxnet virus.
https://www.youtube.com/watch?v=wliTpRLTySU
April 20 2010: The Flame virus caused the BP Oil Disaster
In the summer of 2010, while researching the flame virus, I discovered evidence that the Flame virus led directly to the BP Gulf Oil Spill – the worse environmental disaster in the history of the world. This is something the American people have never been told.

July 23, 2010: At a government hearing to determine the cause of the gulf oil spill, the oil rig's chief electronic technician, Mike Williams – who miraculously survived the explosion – described the events leading up to the disaster. The full details of his testimony are listed on the following web page.
http://techrights.org/2010/10/12/deepwater-update/
Mike Williams testimony sounded exactly like what happens today whenever a Windows computer is attacked by the Flame Virus. According to Mr. Williams, for months, the computer system on the ill fated BP oil rig had been locking up, producing what the crew called the “blue screen of death.” (Note: The Blue Screen of Death most commonly occurs on Windows computers after a faulty update). When the computers were down, the safety equipment did not work and the well could not be monitored. Five weeks before the explosion, in March 2010, Mike Williams had been sent to the oil rig to fix the computer problem. Mike testified, “The computer screen would just turn blue. You'd have no data coming through."Mike explained that with the computer frozen, the drillers did not have access to crucial data about what was going on in the well. Williams described the Windows computer system as “a very unstable platform” and “bad software” that was the root cause of most of the drilling problems. This buggy Windows based control system left drillers blind when it crashed daily and was responsible for safety system bypasses that eventually destroyed the well seal and led to the explosion. On page 42 of the hearing transcript, Mike Williams stated:
“For three to four months we’ve had problems with this computer simply locking up. [sometimes it was a blue screen, sometimes a frozen display] … We had ordered replacement hard drives from the manufacturer. We had actually ordered an entire new system, new computers, new servers, new everything to upgrade it from the very obsolete operating system that it was using.” http://techrights.org/2010/10/12/deepwater-update/ |
Thus, according to Mr. Williams, the computer problems began in January 2010. Between the manufacturer and the rig, they could not get the bugs worked out of the new operating system. They couldn’t get the old software to run correctly on the new operating system. Microsoft Updates – instead of fixing the problem actually made the problems worse. This was an important clue that their computer system had been infected with the Flame super bug. Who would create such a vicious virus and why? I was not able to connect the Flame virus to the Stuxnet virus and the NSA until a shocking article was published in June 2012.
June 1, 2012: James Risen, a reporter with the NEW York Times, interviewed one of the US generals associated with the Stuxnet project and posted an article where this general described the Stuxnet deployment against Iran in detail. If you are not familiar with the NSA Stuxnet attack on Iran then please read the following article.
http://www.nytimes.com/2012/06/01/world/middleeast/obama-ordered-wave-of-cyberattacks-against-iran.html?pagewanted=2&_r=1&seid=auto&smid=tw-nytimespolitics&pagewanted=all
2010 to 2014: NSA greatly expands their cyber warfare arsenal.
Stuxnet’s was not the only cyber weapon created by the NSA. The NSA also created Flame, Gauss and Duqu. Each of these has coding patterns related to previous programs including using many of the same modules, structures and processes. These severely dangerous and harmful programs are very complex. Below is a diagram of code modules in the Duqu Driver. This is only one of more than 100 components that make up the Duqu 2.0 (2015) virus.
https://www.rsaconference.com/writable/presentations/file_upload/br-208_bencsath.pdf
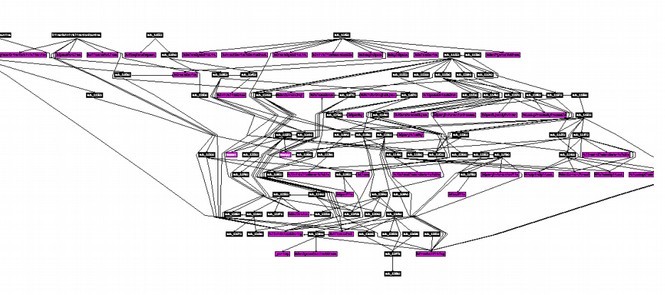
Here are a couple of links that describe the evolution of NSA cyber warfare weapons:
https://cdn.securelist.com/files/2015/06/The_Mystery_of_Duqu_2_0_a_sophisticated_cyberespionage_actor_returns.pdf
https://www.concise-courses.com/stuxnet-flame-gauss-duqu/
June 6, 2013: Snowden Provides Documents Confirming the Power of the NSA
I was about to publish a book called “Free Yourself from Microsoft and the NSA” describing the dangers of the NSA Flame Virus and Stuxnet virus as well as the dangers of open back doors in the Windows operating system in June 2013 – a book I had worked on for more than a year. Here is a link to this book if you would like to read it.https://freeyourselffrommicrosoftandthensa.org/
I realized people would think I was crazy for claiming that the NSA had produced these super weapons. But I was going to publish it anyway. Then, Edward Snowden provides thousands of documents to reporters confirming the hidden power of the NSA. If my prior research had peaked behind the curtain, the Snowden documents blew the lid off the entire NSA operation.
http://www.guardian.co.uk/world/2013/jun/06/us-tech-giants-nsa-data
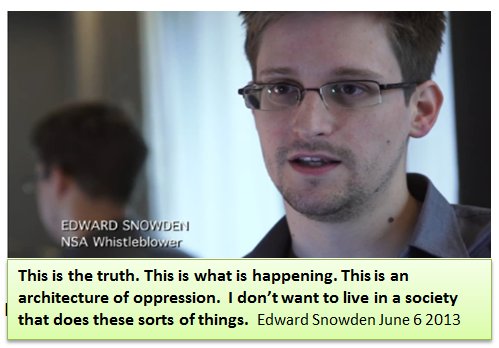
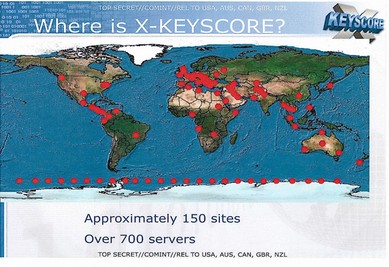
July 13, 2013: Glenn Greenwald explains how the NSA downloads documents from Windows computers. He released documents provided by Edward Snowden on a top secret NSA program called Xkeyscore (aka XKS) which is used to steal and store documents from your Windows computer. Xkeyscore is used through over 700 servers at 150 sites around the world.
http://www.theguardian.com/world/interactive/2013/jul/31/nsa-xkeyscore-program-full-presentation
February 16, 2015 Kaspersky exposed the Equation Group
Independently from Snowden, a computer security firm called Kaspersky had been analyzing the Flame and Stuxnet cyber weapons. In 2013 and 2014, they published several reports documenting how these super weapons worked. Then in February 2015, they published a report linking them all together. Kaspersky publishes a report on the “Death Star of the Malware Galaxy” which it called the Equation Group (which we know is the NSA). The relationship of Stuxnet to other NSA cyber weapons was confirmed in this detailed analysis.https://securelist.com/blog/research/68750/equation-the-death-star-of-malware-galaxy/
https://securelist.com/files/2015/02/Equation_group_questions_and_answers.pdf

The Kaspersky researchers described a group they called the Equation group which was infecting computers and websites all over the planet. The report noted that the techniques being used were linked to techniques and malware programs previously developed and used by the NSA including the Flame and Stuxnet viruses which the US used to attack Iranian computers. Here is their diagram of the relationships between the various Equation Group cyber weapons. Note that Stuxnet, Flame and Gauss are all directly related:
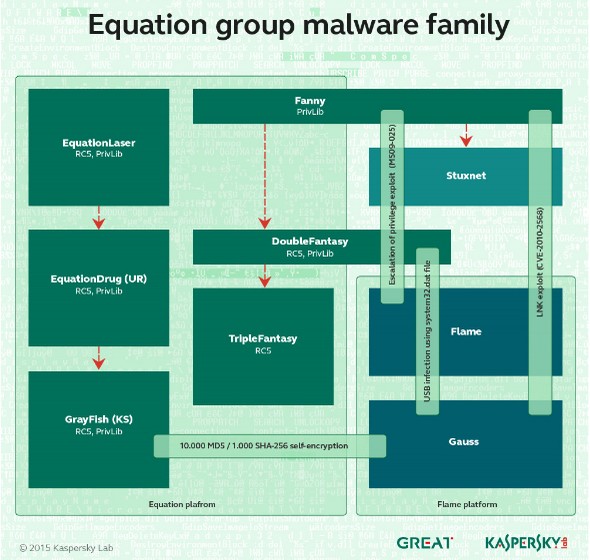
Here is a quote from their 44 page report: “All the malware we have collected so far is designed to work on Microsoft’s Windows operating system. The malware callbacks are consistent with the DOUBLEFANTASY schema, which normally injects into the system browser (for instance, Internet Explorer on Windows)… The Equation group uses a vast infrastructure that includes more than 300 domains and more than 100 servers.”
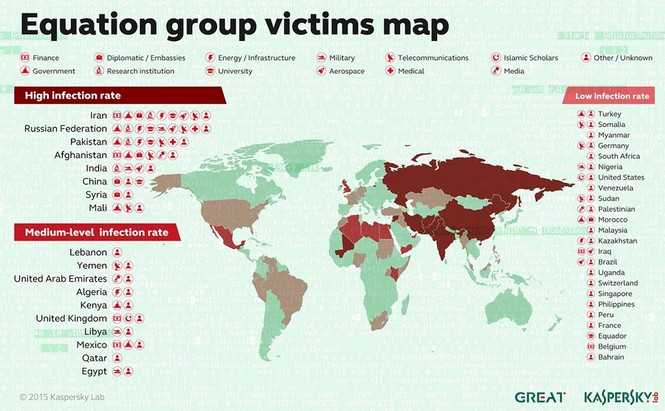
Here is a map of all of the victims of the Equation Group according to Kaspersky (Note: this map is not complete as I personally know of victims in countries not on this map). Clearly the primary targets or victims of the Equation group are China and Russia. However, we should note that the Equation Group also targets computers in the US:
April 30, 2013: The NSA/Equation Group Posts a Training Video on Youtube
Having spent years following this evolution of NSA cyber warfare weapons, it is apparent to me that tens of thousands of hackers have been trained by the NSA. Here is a 26 minute Youtube video of the NSA “Red Cell” teaching young military recruits how to hack computers. https://www.youtube.com/watch?v=HnnvVnsDCGw

Most of these hackers eventually leave the US military and then work for thousands of fake cyber security consulting firms funded directly or indirectly by the NSA. Thanks to the revelations of Edward Snowden, we also know the NSA has a network of hundreds of hacking servers in more than one hundred countries around the world.
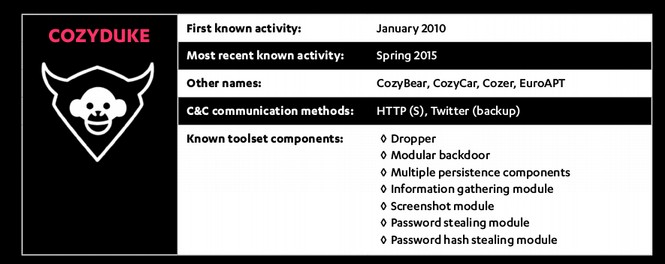
February 28, 2015: Kaspersky links Cozy Bear to Cozy Duke.
Kaspersky for several years had been the world leader in documenting the hacking activities of the Equation Group, which was responsible for cyber attacks on servers in Iran. These cyber weapons included Stuxnet, Flame, Gauss and Duqu. Kaspersky does not link Cozy Bear or the Equation group to any nation-state because they have a policy of “not getting involved in politics.” But others will later falsely claim that Kaspersky said that Cozy Bear was linked to the Russian government. We will provide quotes from the actual Kaspersky reports which imply that Cozy Bear was not Russian but rather the NSA. Here is a link to their February 28 2013 report on Cozy Duke aka Cozy Bear.https://kasperskycontenthub.com/wp-content/uploads/sites/43/vlpdfs/themysteryofthepdf0-dayassemblermicrobackdoor.pdf
Cozy Bear aka Cozy Duke was used not just to attack the US but many other countries including Russia
Here is a list of the countries that had been targeted by the Duke virus.
“Researchers found 59 unique victims in the following 23 countries: Belgium, Brazil, Bulgaria, Czech Republic, Georgia, Germany, Hungary, Ireland, Israel, Japan, Latvia, Lebanon, Lithuania, Montenegro, Portugal, Romania, Russian Federation, Slovenia, Spain, Turkey, Ukraine, United Kingdom and United States.”
So if Russia really was the source of the Duke virus, then we have to believe that the Russian Federation used this virus to attack itself. Alternately if we want to conclude that the US was the nation that built the Duke virus then we have to believe that the US attacked itself. These are not equal assumptions because, thanks to Edward Snowden, there is plenty of evidence of the NSA attacking victims in the US. We know they do this. It is part of their motto to hack everything.
June 10 2015: Kaspersky links Duqu to the Duqu 2 cyber weapon.
In June 2015 Kaspersky admitted that they had been hacked by a new cyber weapon they called Duqu 2.0. Here is a quote from Kaspersky: “Since these have never been made public and considering the main interest appears to have remained the same, we conclude the attackers behind Duqu and Duqu 2.0 are the same.”
https://cdn.securelist.com/files/2015/06/The_Mystery_of_Duqu_2_0_a_sophisticated_cyberespionage_actor_returns.pdf
So Duqu and Duqu 2 were made by the same group. But how do we know these are made by the same group that made Stuxnet, Flame and Gauss? Here we have several sources. First, we have the Kaspersky group who has done detailed analysis of all of these viruses breaking the code and structure of each down line by line. Kaspersky has written hundreds of pages of reports on this topic and they have repeatedly concluded that these viruses were all written by the same nation-state.
Another source is the NSA documents released by Snowden. In these documents are NSA presentations in which they discuss Stuxnet as being one of their “implants.” https://theintercept.com/2014/11/12/stuxnet/

The June 2015 Kaspersky report confirmed several more Stuxnet like “patterns” of the Cozy Duke hackers:
#1 Cozy Duke uses extremely expensive and rare Zero Day Exploits
Zero day exploits are security holes in software such as Microsoft Windows that not even Microsoft is aware of. The Dukes cyber weapon uses Zero Day attacks just like the Duqu Stuxnet and Flame viruses. In fact, NSA viruses often use a dozen or more zero day exploits.
#2 Cozy Duke was written with Windows Programs by Windows programmers common in the US
Analysis of the Cozy Duke code confirms that it was written using Windows programs. While it is possible that Russian hackers could use Windows computers and programs to write the virus, it is much more likely that they would use Linux computers and programs for security reasons (after all, they know how insecure Windows is and how easy it would be to be hacked by the NSA if they were using Windows programs). By contrast, the NSA often uses Windows programs and programmers because they have a direct relationship with Microsoft. Note that the Equation group cyber weapons were also all written using Windows programs.
#3 Cozy Duke use in the Ukraine declined after US Puppets Took Over Ukraine
Here is a quote from one of the 2015 reports analyzing Cozy Duke:
“Contrary to what might be assumed, we have actually observed a drop instead of an increase in Ukraine-related campaigns from the Dukes following the country’s political crisis. This is in stark contrast to some other suspected Russian threat actors (such as Operation Pawn Storm [10]) who appear to have increased their targeting of Ukraine following the crisis.”
In other words, Pawn Storm saw its use go up after the US CIA backed group took over Ukraine while a much more powerful weapon called Cozy Duke was used less. The Russians would have no reason to use their most powerful cyber weapon less after the CIA backed coup in Ukraine. The only ones with this kind of motive would be the NSA.
https://www.f-secure.com/documents/996508/1030745/dukes_whitepaper.pdf
#4 The Cozy Bear Referral Servers are in Panama, France, Germany, the US and Turkey
After infecting computers and servers, Cozy Bear calls home to the mother ship. According to the Kaspersky analysis, Cozy Bear is programmed to contact specific servers in Panama, France, Germany, the US and Turkey. These five countries all have a strong NSA CIA presence. None of these countries has a close relationship to Russia – especially not in 2014. Understanding that IP addresses can be faked, these are the IP addresses of the mother ship as provided by Kaspersky:
200.63.46.23
95.128.72.24
72.34.47.186
188.40.99.143
85.95.236.114
Here is a review of these IP addresses using http://whatismyipaddress.com
200.63.46.23 is a server owned by Panamaserver.com. They are listed as a clean server meaning there have been no reports of them attacking people. This means that people were unaware of who was attacking them and where the attackers were located.
95.128.72.24 is a clean server owned by cl-turbo.celeo.net in Paris France. This domain name has no apparent services so how does it make money and stay in business?
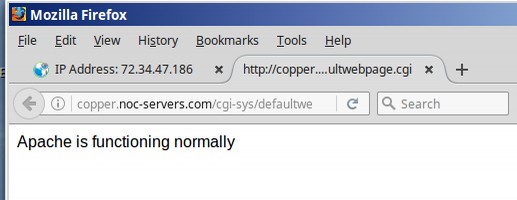
72.34.47.186 is a clean server owned by IHNetworks LLC in Los Angeles CA. They use the domain name copper.noc-servers.com. This domain name has no apparent services. So how does it make money and stay in business? I was able to confirm that this server is using a Linux Apache server program and is also using Cpanel. But that was as far as I could get. Here is a screen shot of this URL:
IHNetworks LLC appears to be a web hosting company that purchased a Texas based web hosting company called Eleven2 in 2012 but continued to use the user name of the former company apparently to hide the fact that the company was bought.
http://www.webhostingtalk.com/showthread.php?t=1431081
IHNetwork hosts about 4,000 domain names (most from Eleven2). Most of these domain names have very low traffic. Even at $100 per domain per year, this is only $400,000 annually which would barely pay for the server much less the staff. Here is a link to all of the domain names hosted by IHNetworks and their current traffic levels. https://w3bin.com/hoster/77
Yet despite this fact, IHNetworks claims on their home page to have servers and data centers located around the world! http://ihnetworks.com/
Here is a screen shot of all of the five web hosts that they have bought:

So where is this company getting all of the money to buy these web hosts and pay for servers and data centers all around the world? This company appears to have an unlimited amount of money but its known income is only $400,000 per year! Also, exactly how is it related to Cozy Bear given that it is highly unlikely Cozy Bear would want to use servers located in the US and subject to US laws if Cozy Bear was really from Russia.
188.40.99.143 is a clean corporate server located in Germany. The Internet Service Provider is Hetzner Online AG. This one appears to be a real web hosting company that has been in existence since 1997. Perhaps the NSA just has an account here.
85.95.236.114 is a clean broadband server in Turkey. Just about anyone can use a broadband server so there is no real way to research this connection other than to confirm that the IP address is actually located in Turkey (which I did).
#5 Cozy Bear aka Cozy Duke uses a Twitter account to call the mother ship
The primary method that Twitter uses to communicate with the mother ship is a Twitter handle that uses common phrases about the weather. Should the Twitter account be taken down, Cozy Bear has a backup communication method that uses Google. Given the known relationships between Google, Twitter and the NSA, it is unlikely that Russian hackers would use either of these corporations as their primary means of communicating between their hacking tools and the Home servers. Here is a graphic of Cozy Duke aka Cozy Bear from Kaspersky confirming it uses Twitter to communicate.
#6 Fancy Bear also used a US Registrar for one of their hacking domain names.
One of the ways Fancy Bear gains access to computers and servers is by fooling folks to click on a PDF link that activates the cyber weapon. This is linked to a domain name called PDFRegistry.net. Here is the ownership status of this domain name:
Domain Name: PDFREGISTRY.NET
Registrar: 1&1 INTERNET SE
Sponsoring Registrar IANA ID: 83
Whois Server: whois.1and1.com
Referral URL: http://registrar.1and1.info
Name Server: NS-US.1AND1-DNS.COM
1 and 1 is a major US domain name registrar. The domain name was created on April 12 2015, was updated on September 30 2016 and is paid through 2017. Here is the problem with the Russians using a US domain registrar: current US laws allow the FBI nearly instant access to any and all US servers. This should not be allowed. But it is allowed which is why I recommend that website owners host their domain names on servers that are outside of the US. Certainly the Russians are fully aware of the danger of using US web hosts in terms of instant FBI access without even seeking a warrant from a judge. There is no way Russians are going to use US registrars or web hosts for their secret cyber weapon hacking programs. However, the NSA would have nothing to fear from using US servers as the NSA and FBI are best friends.
August, 2015 Fancy Bear used a fake domain name for the Electronic Freedom Foundation to fool folks into downloading their cyber weapons.
Fancy Bear who would later use a DNC related fake domain name to attack folks in March 2016, also used an EFF fake domain name to hack people in August 2015. This is very relevant because one of the world’s biggest opponents of NSA mass hacking is the Electronic Freedom Foundation (EFF). This group has actually filed lawsuits against the NSA and has posted detailed articles explaining to people how they can use tools such as Linux to protect against NSA hacking attacks.
The real domain name for the EFF is https://www.eff.org/

However the Fancy Bear Cyber weapon used the fake domain name Electronicfrontierfoundation.org to fool folks into downloading their cyber weapon.
https://www.eff.org/deeplinks/2015/08/new-spear-phishing-campaign-pretends-be-eff
EFF has since purchased this domain name and redirected it to their real domain name in order to try to protect their clients. However, the malicious use of this fake domain name clearly is intended to harm the Electronic Freedom Foundation and those who trust the EFF. No rational person would believe that Russia would want to deliberately undermine one of the NSA’s biggest opponents. But there is no doubt that the NSA would want to undermine the EFF and their supporters.
NSA learns how to cover their tracks to hide it is the source of most cyber weapons
To better understand the extreme lengths that the NSA goes to in order to confuse folks about its viruses, let’s read a quote from page 43 of one of the most recent Kaspersky Duqu virus manuals: “In the case of Duqu, the attackers use multiple proxies and jumping points to mask their IP connections. This makes tracking an extremely complex problem. Additionally, the attackers have tried to include several false flags throughout the code, designed to send researchers in the wrong direction. For instance, one of the drivers contains the string “ugly.gorilla”, which obviously refers to 9Wang Dong, a Chinese hacker believed to be associated with the APT1/Comment Crew. The usage of the Camellia cypher previously seen in APT1 samples is another false flag planted by the attackers to make researchers believe they are dealing with APT1 related malware. “
https://cdn.securelist.com/files/2015/06/The_Mystery_of_Duqu_2_0_a_sophisticated_cyberespionage_actor_returns.pdf
In other words, the makers of Duqu (who we know are NSA coders) want us to think they are Chinese hackers when they are not. These NSA hackers even faked time stamps on their activities to make us believe they are operating in a Russian time zone when in fact they are operating in the US Eastern Time Zone.
September 15, 2015 Duqu 2 uses Easily faked time stamps
In June 2016, Crowdstrike issued a report claiming that Cozy Bear and Fancy Bear were Russian hackers. The source document for this claim was a September 15, 2015 report written by a computer security firm called F Secure.
https://www.f-secure.com/documents/996508/1030745/dukes_whitepaper.pdf
This report mistakenly used easily faked time stamps as evidence that the Duke viruses were written by Russians. Here is a quote from the conclusion of the F Secure 2015 Report: “Attribution is always a difficult question, but attempting to answer it is important in understanding these types of threats and how to defend against them... The Dukes have consistently operated large-scale campaigns against high-profile targets...We therefore believe the Dukes to be a single, large, well-coordinated organization with clear separation of responsibilities and targets. This leaves us with the final question: which country? We are unable to conclusively prove responsibility of any specific country for the Dukes.
All of the available evidence however does in our opinion suggest that the group operates on behalf of the Russian Federation. Kaspersky noted that based on the compilation timestamps, the authors of the Duke malware appear to primarily work from Monday to Friday between the times of 6am and 4pm UTC+0 [11] . This corresponds to working hours between 9am and 7pm in the UTC+3 time zone, also known as Moscow Standard Time, which covers, among others, much of western Russia, including Moscow and St. Petersburg.”
However, since we know the NSA has altered the time stamps on previous programs, it would be a simple matter for them to also alter the time stamps on Cozy Duke. Here is a quote from Kaspersky about why they never attribute any cyber weapon to any nation:
“Cyber-spies can stage false-flag operations: the evidence we use to attempt to identify attackers includes timestamps, words in particular languages in the malware code, names or nicknames, and the geographical locations of the command-and-control servers used. But such evidence is always circumstantial and can easily be forged.”
http://media.kaspersky.com/en/Duqu-2-0-Frequently-Asked-Questions.pdf
It is therefore possible to imagine that the time stamps on the Cozy Duke code are valid and that it was therefore written by Russians. However, such a naive claim ignores all of the other evidence – especially the fact that all the Cozy Duke “call home” server IP addresses are in the US or in countries friendly to the US - which leads to the conclusion that it was the NSA that wrote Cozy Duke. If we conclude that the NSA wrote Cozy Duke, then we must also conclude that it was the NSA and not Russia that hacked the DNC servers. Since the NSA motto is to hack everything, it should not surprise anyone that the NSA was hacking DNC servers – because the NSA hacks all servers.
All of the above was reported and known prior to the DNC hacker attacks. Now that we have a better understanding of how Cozy Bear and Fancy Bear work, and the fact that both are far more likely to be NSA cyber weapons than Russian cyber weapons, let’s get back to the DNC hack.

