September 15, 2016 Server Company Provides Analysis of Hacker Locations
While nearly all of the servers claimed to be involved in the Russian Hacking attacks were not in Russia and have failed to provide any analysis from their server logs (I really wonder why this is because all servers have server logs), one Russian company that was caught up in the cyber attack did take the time to analyze their logs and issue a press release with their findings. Since this is what every server company should have done, I will quote from an English translation of their press release which was written in Russian.This company has since been attacked as being owned by Russian criminals and I want to make it clear that I have no way of verifying their report. I am simply quoting them to show the public what could be done if a server company wanted to help us discover the truth – namely they should all publish their logs. Also I am certain that the FBI can get a warrant for all logs of all servers in the US. The fact that the FBI has not done this (or has not released information about the logs if they have done this) is a strong indication that the FBI is not really interested in providing the public with additional information about the locations of communications from the hackers to the servers. Here is the source document which will be translated for you if you visit the page with a Chrome Browser.
https://chronopay.com/blog/2016/09/15/chronopay-pomogaet-king-servers-com/
Here is an edited version of their press release (I edited to make it shorter by eliminating text that was not related to the server logs. I also bolded the important parts):
“King Servers (https://www.king-servers.com), which owns servers from which the hacker allegedly performed attacks on the United States Democratic Party, states the absence of any «Russian trace» in this cybercrime nor its own involvement...King Servers, owned indeed by Russian nationals, provides VPS and VDS rental services of the equipment, physically located in the Netherlands. Earlier, after the FBI alert (https://s.yimg.com/dh/ap/politics/images/boe_flash_aug_2016_final.pdf) and analysis from Threat Connect (https://threatconnect.com/blog/state-board -election -rabbit-hole /), the world's leading media were spreading information about the discovery of the so-called «Russian trace» in the attacks on the United States democratic party in Illinois. The «Russian trace» was mostly presented as the use of King Servers services, stating that the company belongs to Russian citizens. As of September 15, neither King Servers received any complaints or appeals for any server misuse or abuse, nor any public authority did any attempts for servers withdrawal. Due to that King Servers found out about the issue related to that attack only on September 15, at 7 am Moscow time, and immediately shut down identified servers.
The analysis of the internal data allows King Services to confidently refute any conclusions about the involvement of the Russian special services in this attack. Attackers rented two servers using probably fabricated personal and identification data. After the attack servers were wiped out. However, King Servers maintains logs of accessing administrative control panel. After log analysis, King Servers obtained a list of about 60 of all possible IP addresses of «hackers», none of which belongs to any Russian ip range. Attackers were logging into administrative control panel mainly from Scandinavian countries (Norway, Sweden) and from the European Union (Italy).
Payment for servers were done through semi-anonymous Russian payment system, albeit very well-known in Russia for virtually open collaboration with US security agencies at least since 2011, when American security experts close to the state intelligence and counterintelligence agencies in the United States. With high probability, attacker's servers were controlled by one person, since there are lots of IP matches between two accounts...King Servers retained all the investigation materials, copies of server log files and correspondence and is ready to provide them to any interested party, law enforcement agencies or media, in accordance with the law.”
Many people have asked me what evidence it would take to convince me that Russian government agents did hack the DNC. One of the things it would take would be a pattern of evidence linking the “call home” servers to IP addresses that eventually linked in a chain back to Russia. Note above that they were able to isolate the accounts and ID every single transaction just like a bank can trace a financial transaction. They then provided some useful information – that the hackers were logging in from servers mainly in Norway, Sweden and Italy. I realize that this does not mean that the hackers were actually in any of these countries. But we can go to the servers in those countries and eventually trace the hacker back to their source servers.
I am not saying this would be easy. But I am certain that the NSA has this capability. The American people deserve much better then the nonsense and BS we have been given by the US intelligence agencies. What I am asking for is exactly what William Binney and Edward Snowden are asking for. Real hard evidence. It is a complete lie that providing this evidence would compromise either sources or methods. Server logs are an open book. Why haven’t we been given the server logs of the Fancy Bear servers in San Jose California??? Either give us the logs or stop making these unproven accusations.
October 7 2016: US issues Press Release Blaming Russia for DNC Hack
James Clapper, the person who lied to Congress in March 2013 about the NSA Mass Surveillance Program, issued a press release blaming Russia for hacking the DNC. Once again, there was not one shred of actual evidence. Just a series of unsupported allegations. This is ridiculous.https://www.dhs.gov/news/2016/10/07/joint-statement-department-homeland-security-and-office-director-national
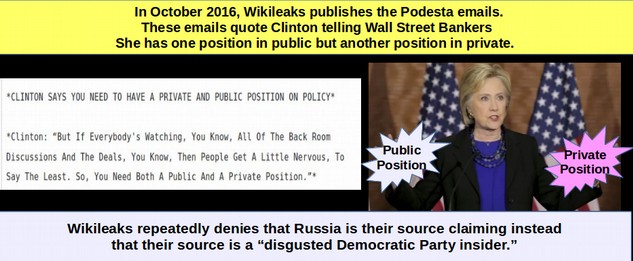
October to November 2016: Over the course of a month, Wikileaks publishes more than 58,000 emails hacked from the Gmail account of John Podesta.
John Podesta was Clinton’s campaign manager. Many are highly incriminating and cast Clinton in a very bad light. Apparently all of the Podesta emails are true.https://wikileaks.org/podesta-emails/
November 2 2016: Wikileaks says Russia is not the source
Wikileaks has repeatedly refused to name any of their sources. However, on November 3 2016, Julian Assange told a reporter John Pilger “We can say that the Russian government is not the source.”http://theduran.com/julian-assange-is-on-the-record-we-can-say-that-the-russian-government-is-not-the-source/
November 8 2016: Media claims odds of Hillary winning as high as 90%.
But in a surprise (at least to the main stream media), Trump wins. Clinton was predicted to win Pennsylvania, Michigan and Wisconsin. She lost all of these Rust Belt states and several other states she was supposed to win. A fact rarely reported In the media is that folks in the rust belt states reported voting for Trump because he promised to get their jobs back while Clinton largely ignored the unemployment problem by falsely claiming their had been an economic recovery. It is not likely that the email scandal played more than a minor role in these Rust Belt states. Americans are not going to vote for Trump just because Putin wants them to. They voted for Trump because they thought he would help them get their jobs back. Here is the prediction from one news source on the day of the election predicting a Clinton win.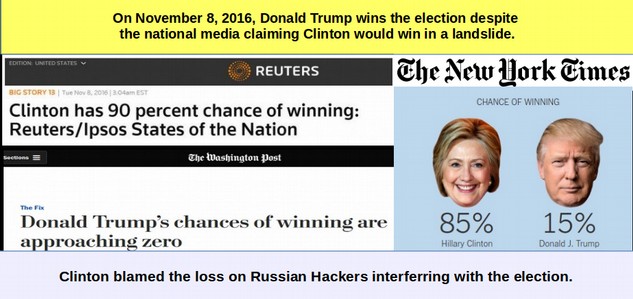
November 24, 2016 The Washington Post issued a story claiming that Russian propaganda help spread fake news through a list of 200 fake news websites.
CIA backed WaPo linking to a list by an anonymous group called Propornot – a group which was later confirmed to be associated with the US military. Some of the news websites on the list threatened to sue the Washington Post which amended the article on December 7 2016 by stating that they could not vouch for the credibility of the list.https://www.washingtonpost.com/business/economy/russian-propaganda-effort-helped-spread-fake-news-during-election-experts-say/2016/11/24/793903b6-8a40-4ca9-b712-716af66098fe_story.html?utm_term=.52946c5d5643
November 30 2016: Congress passed bill authorizing Ministry of Truth for 2017
Congress approved a measure within the National Defense Authorization Act for US State Department to act against propaganda with. The legislation authorized funding of $160 million over a two-year-period. While some claimed that the bill was a response to Russian hacking, the bill appears to have first been written in March 2016.December 9, 2016: President Obama ordered US Intelligence Agencies to conduct an investigation into Russia's attempts to influence the 2016 US. election — and provide a report before he leaves office on January 20, 2017.
December 14 2016: Craig Murray, one of their leaders of Wikileaks said that their source was not a Russian but rather a “disgusted Democratic party insider.”
http://www.dailymail.co.uk/news/article-4034038/Ex-British-ambassador-WikiLeaks-operative-claims-Russia-did-NOT-provide-Clinton-emails-handed-D-C-park-intermediary-disgusted-Democratic-insiders.htmlHere is a quote from the Wikileaks Daily Mail article: 'Neither of [the leaks] came from the Russians,' Murray said. 'The source had legal access to the information. The documents came from inside leaks, not hacks. The leakers were motivated by 'disgust at the corruption of the Clinton Foundation and the tilting of the primary election playing field against Bernie Sanders.”
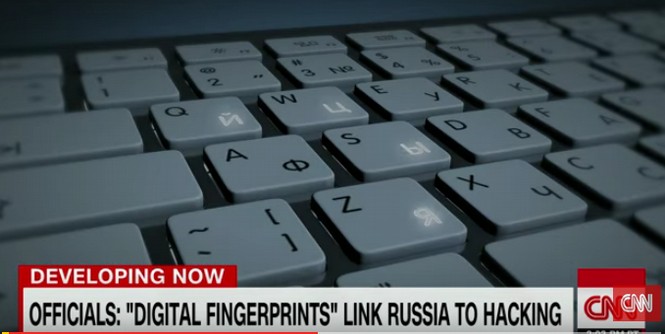
December 16 2016: Digital Fingerprints Turn Out to be Paw Prints
US intelligence officials say that newly identified "digital fingerprints" indicate Moscow was behind the DNC hacks. The administration traced the hack to the specific keyboards -- which featured Cyrillic characters -- that were used to construct the malware code. Apparently, the experts forgot that the NSA undoubtedly has Cyrillic Keyboards and uses them whenever they want to fool folks into thinking they are Russians Meanwhile, Russians are most likely to be using American key boards.http://abcnews.go.com/Politics/video/russias-digital-fingerprints-election-hacking-code-44248807
Cyber Security Analyst Justin Harvey claimed that the hack “called home to Russia and had a Russian signature.” (Justin never bothered to provide the IP addresses confirming that the hackers called Russia – everything we have seen so far is hacks calling servers in countries friendly to the US). But back to Justin “It was written in Moscow’s time zone and seemed to have gaps on Russian holidays. “We saw the Cyrillic alphabet being used.” The beacon transmitted the hacked information to an IP address overseas that had been used in other Russian attacks. (an apparent reference to the Pakistan Crook Servers we debunked earlier. Justin Harvey has written several reports going back to June 2016 all of which agreed with Dimitri at Crowdstrike and one of which made the Godaddy server error. His background is with Fidelis, FireEye and Mandiant – all part of the NSA cyber network cheer leading for Crowdstrike).
Harvey said, the clearest evidence was the IP address that that malicious software used to phone home. “It was an IP address that had been previously seen in other Russian-attributed attacks, including the German parliament, the Bundestag, they encountered a breach last year with the same malware, the same IP address, and then also attributed to the Russians”. (Another reference to the Pakistan Crook Servers we debunked earlier. Of course, no one would ever believe Justin if he explained that the server being used was in Pakistan and run by a group called Crook Servers.)
December 22, 2016: Smoking Gun Alert…Dimitri, Crowdstrike & Ukraine
Dimitri issued another fake report, this time claiming that Fancy Bear Russian Hackers who attacked the DNC had also used a Android App to infect Ukrainian military cell phones to target and kill them. Dimitri was actually interviewed by the PBS News Hour and NBC News about this. As we noted earlier, Dimitri is with the Atlantic Council. Here is a quote from another article about the hawkish nature of the Atlantic Council: “The Atlantic Council is funded in part by the US State Department, NATO, the governments of Latvia and Lithuania, the Ukrainian World Congress, and the Ukrainian oligarch Victor Pinchuk—has been among the loudest voices calling for a new Cold War with Russia. As I pointed out in the pages of The Nation in November, the Atlantic Council has spent the past several years producing some of the most virulent specimens of the new Cold War propaganda.” https://www.thenation.com/article/is-skepticism-treason/Once again, it turns out that Dimitri’s claims are not just not supported, they have been proven to be false. The guy who actually made the Android App called the Crowdstrike report “delusional” noting that if the App was infected it would easily have been spotted. A technical advisor to the Ukrainian military then tracked down the Ukrainian units that used the App and found that they “reported no losses” - thus completely contradicting the claims made by Dimitri of massive losses. Here is a quote from the Ukrainian military advisor: “I personally know hundreds of gunmen in the war zone. None of them told me of D-30 losses caused by hacking or any other reason,” Narozhnyy stressed to the VOA. The article noted that some malware was found on some Android phones. But instead of the malware reporting to Russian servers, it was reporting to servers in the US!
http://www.voanews.com/a/skeptics-doubt-ukraine-hack-link-to-dnc-cyberattack/3649234.html
Here is what security consultant Jeffrey Carr has to say about Dimtri’s delusional report:
“Crowdstrike’s latest report regarding Fancy Bear contains its most dramatic and controversial claim to date; that GRU-written mobile malware used by Ukrainian artillery soldiers contributed to massive artillery losses by the Ukrainian military. “It’s pretty high confidence that Fancy Bear had to be in touch with the Russian military,” Dmitri Alperovich told Forbes.
Crowdstrike’s core argument has three premises:
#1: Fancy Bear (APT28) is the exclusive developer and user of X-Agent [1]
#2: Fancy Bear developed an X-Agent Android variant specifically to compromise an Android ballistic computing application called Попр-Д30.apk for the purpose of geolocating Ukrainian D-30 Howitzer artillery sites[2]
#3: The D-30 Howitzers suffered 80% losses since the start of the war.[3]
If all of these premises were true, then Crowdstrike’s prior claim that Fancy Bear must be affiliated with the GRU [4] would be substantially supported by this new finding. Dmitri referred to it in the PBS interview as “DNA evidence”. In fact, none of those premises are supported by the facts. This article is a summary of the evidence that I’ve gathered during hours of interviews and background research with Ukrainian hackers, soldiers, and an independent analysis of the malware by CrySys Lab. My complete findings will be presented in Washington D.C. next week on January 12th at Suits and Spooks.
X-Agent Is In The Wild
Crowdstrike, along with FireEye and other cybersecurity companies, have long propagated the claim that Fancy Bear and all of its affiliated monikers (APT28, Sednit, Sofacy, Strontium, Tsar Team, Pawn Storm, etc.) were the exclusive developers and users of X-Agent. We now know that is false.
No GPS functionality in the malware or the original application
The first iteration of the POPR-D30 Android app designed by Ukrainian military officer Jaroslav Sherstuk (and the only iteration allegedly impacted by this malware) was a simple ballistics program that calculated corrections for humidity, atmospheric pressure, and other environmental factors that determine accuracy of the D-30 Howitzer. It did not have the capability to connect to WiFi, nor to receive or transmit any data.[6]
The Android APK malware doesn’t use GPS nor does it ask for GPS location information from the infected phone or tablet.[7] That’s a surprising design flaw for custom-made malware whose alleged objective was to collect and transmit location data on Ukrainian artillery to the GRU.
In Eastern Ukraine, mobile phone service was poor even before the war. It has only grown worse since. In fact, Crowdstrike hasn’t provided any evidence that the malware-infected Android app was used by even a single Ukrainian soldier.
Conclusion
Part of the evidence supporting Russian government involvement in the DNC and related hacks (including the German Bundestag and France’s TV5 Monde) stemmed from the assumption that X-Agent malware was exclusively developed and used by Fancy Bear. We now know that’s false, and that the source code has been obtained by others outside of Russia. The GRU, according to Crowdstrike, developed a variant of X-Agent to infect an Android mobile app in order to geolocate and destroy Ukraine’s D-30 howitzers. To do this, they chose an artillery app which had no way to send or receive data, and wrote malware for it that didn’t ask for GPS position information? Crowdstrike never contacted the app’s developer to inform him about their findings. Had they performed that simple courtesy, they might have learned from Jaroslav Sherstuk how improbable, if not impossible, their theory was.
Major media outlets including the The Washington Post, CNN, NBC News, and PBS Newshour ran the story without fact-checking a single detail. Motherboard, Forbes, SC Magazine, and other media did the same. Only VOA and Bloomberg took the time to question Crowdstrike’s claims and do some of their own investigating.
Crowdstrike invented a “devastating” cyber attack out of thin air and called it DNA evidence of Russian government involvement.
//medium.com/@jeffreycarr/the-gru-ukraine-artillery-hack-that-may-never-have-happened-820960bbb02d#.whzgobmeu">https://medium.com/@jeffreycarr/the-gru-ukraine-artillery-hack-that-may-never-have-happened-820960bbb02d#.whzgobmeu
In short, the primary basis for claiming that Fancy Bear is Russian (the monopoly of X Agent) has been proven to be false.
If you need still more evidence that Dimitri is not trustworthy, here is some more information about Dimitri and Crowdstrike:
Here is Dmitri claiming that the only nation interested in hacking people is Russia.
http://www.nytimes.com/2016/12/13/us/politics/russia-hack-election-dnc.html?_r=0
I guess Dmitri is unaware that the NSA motto is “Hack Everything.” This is strange because Dmitri is also a group linked to the FBI and CIA called the Atlantic Council. President Obama’s National Security Advisor, James Jones is the former head of the Atlantic Council. Other members include famous war hawks like Chuck Hagel, Susan Rice and Richard Holbrooke. As for funding, Crowdstrike not only gets funding from Google but also from the US State Department. (Just go to their donor page to see the entire list).
This brings up an important question: Why is the US State Department funding this obviously war hawk group?
If this were not enough, the President of Crowdstrike, Shawn Henry was the former head of the FBI Cyber Division. No wonder the FBI agrees with and promotes Crowdstrike!
Perhaps that is just a coincidence. But news articles about and by CrowdStrike suggest they exist to ratchet up cyber-war tensions with Russia, China, and North Korea based on hyped-up network security «vaporware» products they sell at top dollar prices to tech-ignorant government customers.
http://www.strategic-culture.org/news/2016/12/25/obama-halloween-temperamentally-president-war-with-russia.html
We will get back to this “Cyber Warfare as a Business Model” in a minute. First, we need to review the Grizzly Steppe Report.