June 12 2016: Wikileaks Announces Clinton Data Release is Imminent
At 5:59 pm, Julian Assange announces that they have documents relating to Hillary Clinton which are pending publication and that it would be “enough evidence” to indict her. This appears to be the first public announcement about the DNC leak and/or hack. But he did not reference the DNC… Just the Clinton email private server scandal. He had already posted 32,000 emails from the Clinton private server. He did state that there were more leaked emails to come. Perhaps he did not want to mention the DNC because the DNC hack was not yet public and he wanted to protect his source(s).http://www.itv.com/news/update/2016-06-12/assange-on-peston-on-sunday-more-clinton-leaks-to-come/
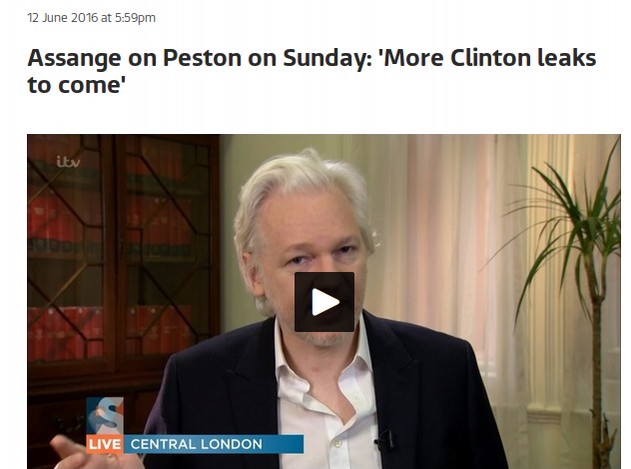
Here is a quote from the June 12, 2016 article:
“Julian Assange, founder of Wikileaks, said on Sunday that the journalist organization is planning to release upcoming leaks in relation to US presidential hopeful Hillary Clinton. Speaking to Peston on Sunday, Mr Assange said Wikileads has further information relating to claims circulating since 2015 that Clinton had in the past used her family's private email server for official communications.”
June 12 2016:According to Guccifer 2.0, the DNC resets their network, kicking “him” out of it on this date. But he does not go public until after the Washington Post story three days later. There are several reasons to conclude that this claim by Guccifer is false and that if he ever had access to the DNC, that access ended on May 1 2016.
June 14, 2016: CIA backed Washington Post Breaks DNC Hack to the Public
Apparently in response to the June 12 2016 Wikileaks announcement, the DNC decided to go public with a story posted by their friends at the Washington Post. On June 14th, the Washington Post revealed that “Russian government hackers” had penetrated the computer network of the Democratic National Committee.”
June 14, 2016: Crowdstrike releases DNC Hack Report
Three hours later, CrowdStrike issued a report called Bears in the Midst outlining some of the details and IP addresses of both attacks. While referring to their previous report in May, they did not provide a link to it. Dmitri Alperovitch stated: “CrowdStrike stands fully by its analysis and findings identifying two separate Russian intelligence-affiliated adversaries present in the DNC network in May 2016.” Of course, if he is so confident in his previous report, then why didn’t he link to the May report so we can all read it?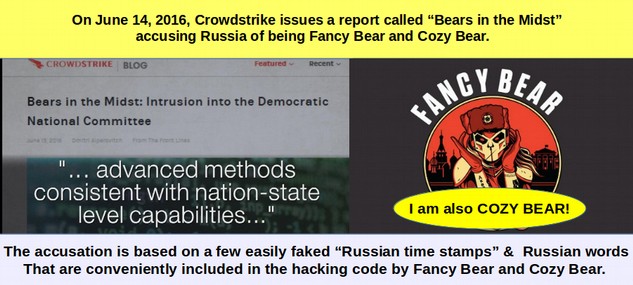
The main person making this claim of Fancy Bear and Cozy Bear attacking the DNC and being Russian is Dmitri Alperovitch who is one of the founders of Crowdstrike. Crowdstrike rose to the national spotlight in June 2016 because they were handpicked by the DNC to investigate who hacked the DNC servers. Dimitri concluded that not just one but two Russian groups called Cozy Bear and Fancy Bear hacked the DNC. Dimitri “evidence” was finding a malware program called Duke (also known as Cozy Duke) was used in the attack. Dmitri then claimed that Cozy Duke aka Fancy Duke were “known” Russian hacking programs (based on the 2015 F Secure Time stamp assumption).

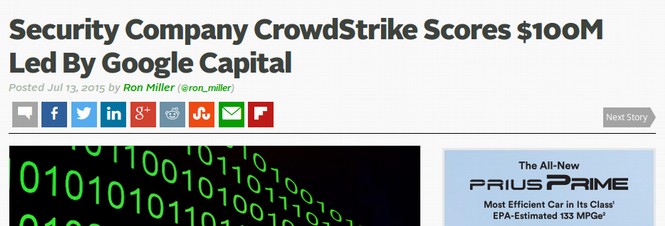
But in order to evaluate whether Crowdstrike is a trustworthy source, we should follow the money. It turns out that Crowdstrike got $100 million in funding from Google who in turn gets hundreds of millions in funding indirectly from the US military.
https://techcrunch.com/2015/07/13/security-company-crowdstrike-scores-100m-led-by-google-capital/
If you are not yet aware of the close relationships between Google, Facebook, the CIA, DARPA and the NSA, you might want to watch this 53 minute documentary.
https://www.youtube.com/watch?v=5WNkDfxTPbI
As for Crowdstrike. it is not the only fake security firm paid hundreds of millions of dollars to do the dirty work of the US military. There are more than 100 other consultants who would just as gladly point the finger at Russia – especially if it meant getting a one hundred million dollar payoff.
In addition Crowdstrike was the group that made the claim that the Sony Hackers were from North Koreans who “stole administrator credientials” when in fact it turned out to be a disgruntled Sony employee who already had administrator credentials. For those who may not remember, in 2014, Sony was attacked using a malware that prevented them from even turning on their computers.
Here is a December 14, 2014 quote from Dimitri expressing confidence that he knows beyond any shadow of a doubt that the hackers must be North Korean:
“The co-founder of CrowdStrike, a security firm that focuses heavily on identifying attribution and actors behind major cybercrime attacks, said his firm has a “very high degree of confidence that the FBI is correct in” attributing the attack against Sony Pictures to North Korean hackers, and that CrowdStrike came to this conclusion independently long before the FBI came out with its announcement last week.
“We have a high-confidence that this is a North Korean operator based on the profiles seen dating back to 2006, including prior espionage against the South Korean and U.S. government and military institutions,” said Dmitri Alperovitch, chief technology officer and co-founder at CrowdStrike.”
https://krebsonsecurity.com/2014/12/the-case-for-n-koreas-role-in-sony-hack/
Other cyber security experts almost immediately began poking holes in Dmitri’s claim that it was North Korea. Here are some quotes:
“Skeptics note that the few malware samples they have studied indicate the hackers routed their attack through computers all over the world. One of those computers, in Bolivia, had been used by the same group to hack targets in South Korea. But that computer, as well as others in Poland, Italy, Thailand, Singapore, Cyprus and the United States, were all freely available to anyone to use, which opens the list of suspects to anyone with an Internet connection and basic hacking skills. (Also) the attackers used commercial software wiping tools that could have been purchased by anyone.
They also point out that whoever attacked Sony had a keen understanding of its computer systems — the names of company servers and passwords were all hard-coded into the malware — suggesting the hackers were inside Sony before they launched their attack. Or it could even have been an inside job… The simpler explanation is that it was an angry “insider,” Mr. Rogers wrote. “Combine that with the details of several layoffs that Sony was planning, and you don’t have to stretch the imagination too far to consider that a disgruntled Sony employee might be at the heart of it all.”
https://bits.blogs.nytimes.com/2014/12/24/new-study-adds-to-skepticism-among-security-experts-that-north-korea-was-behind-sony-hack/?_r=0
The initial communication from the hacker(s) was about employee grievances due to Sony's restructuring and layoff plan. Here is a quote from a December 24, 2015 CNN article: “Upon closer examination, security experts, hackers and people familiar with Sony's computer networks are uniting with this disheartening reality: Anyone could have pulled this off. It could have been a disgruntled Sony employee, profit-seeking hackers, North Korea -- or a combination of the three… this hack actually started as an extortion attempt on Nov. 21 when Sony executives got emails saying: "The compensation for it, monetary compensation we want."
http://money.cnn.com/2014/12/24/technology/security/sony-hack-facts/
So given that Dimitri was so wrong about the Sony hack, why would the DNC hire him to investigate the DNC hack? And why would anyone believe anything Dimitri has to say? We will reveal more about Dimitri and Crowdstrike as we go along.
Details of the June 15 Crowdstrike Report:
According to CrowdStrike, the COZY BEAR hack in 2015 relied on the SeaDaddy implant while the FANCY BEAR hack in 2016 used X-Agent malware. SeaDaddy was discussed in the 2015 F Secure report. It is associated with Cozy Bear. X Agent is more of a problem. We will review it when we get to December 2016 and the false claim made by Crowdstrike that X Agent was used by Russia to target Ukrainian troops via Android phones. But for now, let’s stay focused on the June 15th report.
Here are the IP addresses Crowdstrike associated with Cozy Bear:
185.100.84.134 is a Romanian broadband server.
58.49.58.58 is a Chinese broadband server.
218.1.98.203 is another Chinese broadband server.
187.33.33.8 is a Brazil broadband server.
Here are the IP addresses Crowdstrike associated with Fancy Bear:
185.86.148.227 is a clean Swedish server that has no listed purpose.
45.32.129.185 is another server from our Choopa LLC friends in San Jose CA.
23.227.196.217 is a corporate server associated with Swiftway Communications located in that hot bed of commies otherwise known as Wilmington Delaware. They are an Internet Service Provider (ISP) in business since 2005 and they have servers in the US, Europe and Asia with customers in over 90 countries around the world. One of their customers seems to be Fancy Bear. Their website is: http://www.swiftway.net/
I could not find anything connecting any of the above servers to Russia. Broadband servers are not evidence of anything. And servers in the US are strong evidence that the hackers are NOT Russians. I do not question these IP addresses being associated with Cozy Bear and Fancy Bear. But I do question these IP addresses somehow being connected to Russian Hackers.
June 15, 2016: Guccifer 2 surfaces and claims to be the lone DNC Hacker
GUCCIFER 2.0 posted a Wordpress blog titled “DNC’s servers hacked by a lone hacker.” This online persona claimed to have given “thousands of files and mails” to Wikileaks, while mocking Crowdstrike. He claimed to be Romania but could not speak Romanian. He uses the “)))” smiley emoticon used by those using a Cyrillic keyboard. The metadata for the documents that Guccifer 2.0’s posts is taken from the founder of the Soviet Union’s secret police. He therefore seems to be some kind of plant. He is working for someone. But it is impossible to tell who as he is a pretty bad actor and makes several basic mistakes. For example, he posted a Word document that had the name of a famous Russian in the properties section of the document – thus leading reporters to conclude that he was Russian. But Guccifer could just as easily been the NSA posing as a Romanian but really intended to be exposed as a Russian. Moreover setting up a website for folks to download documents and being interviewed by the press is not exactly how most hackers work. Guccifer may have hacked the DNC and gotten a bunch of files. Security at the DNC was so lax that a teenager could have hacked them.
But based on his statements and actions, I do not think Guccifer 2 is Russian or NSA or Cozy Bear or Fancy Bear. We will not spend much more time on Guccifer for this reason. Also, there are several facts that are much more relevant that we do want to cover – such as who is Fancy Bear and who is Cozy Bear.
June 17, 2016: German Hack Smoking Gun turns out to be Smoke & Mirrors
Another member of the NSA club called Threat Connect issued a brief report on Crowdstrike IP addresses called Fancy Bears and Where to Find Themhttps://www.threatconnect.com/blog/tapping-into-democratic-national-committee/
This report appeared to provide a “smoking gun” confirming that Fancy Bear was Russian. But like all of the other smoking guns, even a little research reveals it was all smoke and mirrors. In their June 15 2016 report, Crowdstrike claimed that the IP address 176.31.112.10 is controlled and/or used by Fancy Bear as it was hard coded into the malware and was involved in the Fancy Bear attack in Germany in 2015. As this is the main evidence that the DNC March 22 2016 attack was from Fancy Bear, we need to also look at the Germany attack for evidence of Russian hackers.
First is a quote from a Crowdstrike Cheerleader named Thomas Rid:
“One of the strongest pieces of evidence linking GRU to the DNC hack is the equivalent of identical fingerprints found in two burglarized buildings: a reused command-and-control address—176.31.112[.]10—that was hard coded in a piece of malware found both in the German parliament as well as on the DNC’s servers. Russian military intelligence was identified by the German domestic security agency BfV as the actor responsible for the Bundestag breach. The infrastructure behind the fake MIS Department domain was also linked to the Berlin intrusion through at least one other element, a shared SSL certificate.”
http://motherboard.vice.com/read/all-signs-point-to-russia-being-behind-the-dnc-hack
It sounds like an open and shut case, doesn’t it? There is only one problem. Almost every sentence in the above paragraph is false (kind of like the Vermont Power Grid story was false). But don’t take it from me. Here is a quote from security consultant Jeffrey Carr:
“Problem #1: The IP address 176.31.112[.]10 used in the Bundestag breach as a Command and Control server has never been connected to the Russian intelligence services. In fact, Claudio Guarnieri, a highly regarded security researcher, whose technical analysis was referenced by Rid, stated that “no evidence allows to tie the attacks to governments of any particular country.”
Problem #2: The Command & Control server (176.31.112.10) was using an outdated version of OpenSSL vulnerable to Heartbleed attacks. Heartbleed allows attackers to steal data including private keys, usernames, passwords and other sensitive information. The existence of a known security vulnerability that’s trivial to exploit opens the door to the possibility that the systems were used by one rogue group, and then infiltrated by a second rogue group, making attribution even more complicated.
Problem #3: The BfV published a newsletter in January 2016 which assumes that the GRU and FSB are responsible because of technical indicators, not because of any classified finding; to wit: “It is assumed that both the Russian domestic intelligence service FSB and the military foreign intelligence service GRU run cyber operations.”
//medium.com/@jeffreycarr/can-facts-slow-the-dnc-breach-runaway-train-lets-try-14040ac68a55#.9o758bkf5">https://medium.com/@jeffreycarr/can-facts-slow-the-dnc-breach-runaway-train-lets-try-14040ac68a55#.9o758bkf5
But don’t take Jeffrey’s word for it. Let’s go to the source. This is the source document for the May 20 2015 German hack that was reported on June 19 2015 which thankfully was printed in English as my German is a little rusty. .
https://netzpolitik.org/2015/digital-attack-on-german-parliament-investigative-report-on-the-hack-of-the-left-party-infrastructure-in-bundestag/
Here is a quote from the report: “Attributes of one of the artifacts and intelligence gathered on the infrastructure operated by the attackers suggest that the attack was perpetrated by a state-sponsored group known as APT28. Previous work published by security vendor FireEye in October 2014 suggests the group might be of Russian origin.” So the author relies on the Fire Eye conclusion that APT 28 is Russian which in turn was based on the F Secure Report which in turn was based on easily changed time stamps.
But it may be that the hacker of the German server was not Russian or American because the hacker made a very basic mistake. Here is the quote:
“The Command & Control server (176.31.112.10) appears to be using an outdated version of OpenSSL and be vulnerable to Heartbleed attacks. The same C&C server might have been the subject of 3rd-party attacks due to this vulnerability.”
Here is one more quote from the German report:
“(German hack) Artifact #2 was compiled by the authors on April 22nd 2015, which suggests that the compromise may only have lasted a couple of weeks...Previous work by security vendor FireEye suggests the group might be of Russian origin, however no evidence allows us to tie the attacks to governments of any particular country.”
One important final quote: “The address, 176.31.112.10, is a dedicated server provided by the French OVH hosting company, but is apparently operated by an offshore secure hosting company called CrookServers.com and seemingly located in Pakistan.
By researching historical data relevant to C&C 176.31.112.10, we discovered that on February 16th 2015, the server was sharing an SSL certificate with another IP address allocated to CrookServers and also hosted at OVH: 213.251.187.145“.
Our Comments on the German Hack Smoking Gun
Whether there was a third party attack or not, using an outdated version of Open SSL with a very widely publicized vulnerability that could destroy the whole apple cart seems like something that only a teenager wannabe hacker would do – not Russian hackers and not NSA hackers. The program was compiled just before the May 2015 hack. This seems to indicate that it was some kid that got hold of a program not even realizing that it suffered from the Heartbleed problem. Moreover, there seems to be little motive for Russia to hack the server of a left leaning political party in Germany. Finally, there is no way Russian hackers are going to be using servers in Pakistan by a hosting company called Crook Servers. The only hackers I know that are that arrogant are the NSA Equation Group. I could see the NSA hacking the German server due to their motto to “hack everything.” But there is no way that the Equation group would overlook the Heartbleed problem. So my conclusion is that the German hacker was not even Fancy Bear. It was simply some teenager out for a joy ride. And the smoking gun? It was more like smoke and mirrors.
July 7, 2016: Threat Connect Proves they have no idea what they are talking about
Threat Connect posted a short blog trying to explain the significance of Named Servers being associated with the Russian Hackers. Sadly, during their explanation, they incorrectly claiming that Godaddy uses named servers called GoDaddy. Here is a quote: “For example, if five domains are registered through GoDaddy, all five of those domains by default will use GoDaddy name servers like NS1.GODADDY[.]COM and NS2.GODADDY[.]COM.”
https://www.threatconnect.com/blog/whats-in-a-name-server/
There are two problems with this claim. First, their example is factually wrong. In fact, Godaddy named servers are not under the name Godaddy. They are under the name Domain Control. As the millions of people who have GoDaddy accounts know, their named servers use the names ns38.domaincontrol.com, ns39.domaincontrol.com, etc. It does not inspire much confidence when these so-called security experts do not even know the names of the world’s most over-crowded servers.
Second, Russian Hackers would never use GoDaddy servers because they are located in the US with a US corporation under draconian US laws. Russian hackers also would not use servers located in Russia. But there are many European countries with strong privacy laws were Russian hackers would be least likely to be caught or disturbed. Switzerland comes to mind as a good place to have one’s data if one did not want to be shut down by the FBI and the NSA.
July 10, 2016: DNC staffer Seth Rich killed in Washington DC
At 4:19 am. Seth Rich, the Voter Expansion Data Director for the DNC was shot twice in the back and killed in a Washington DC suburb. His girlfriend stated “ "There had been a struggle. His hands were bruised, his knees are bruised, his face is bruised, and yet he had two shots to his back, and yet they never took anything." Some claimed that Seth Rich was the source of the DNC leak to Wikileaks and that he was shot for betraying the Democratic Party leaders. https://en.wikipedia.org/wiki/Murder_of_Seth_RichJuly 22, 2016: Wikileaks published DNC Leak Documents
Just before the Democratic National Convention, Wikileaks published more than 19,000 DNC emails with more than 8,000 attachments confirming that the DNC had colluded with the Clinton campaign to block Bernie Sanders from the nomination. Many Sanders supporters at the convention walked out in protest. This same day, Guccifer 2.0 claims they gave the files to WikiLeaks, four hours later WikiLeaks says that anyone claiming to know who their source is “has no credibility.”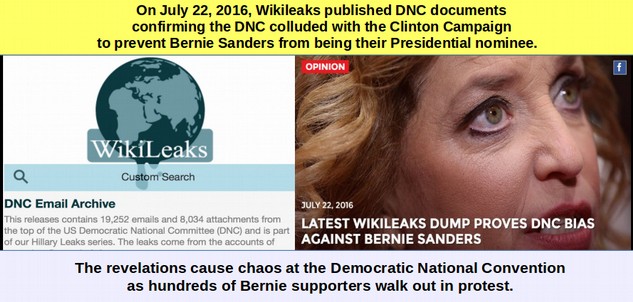
July 24 2016: Wikileaks issues Tweet Implying Source is an Insider
WikiLeaks says their sources do not set the date for releases and that they have more DNC documents coming. Another tweet implies their source may have been an insider.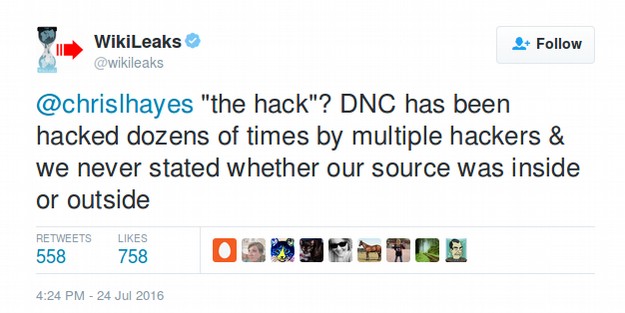
A later tweet indicated it was an inside job or a leak – not a hack.
July 24, 2016: Debbie Wasserman Schultz, chair of Democratic National Committee, resigned from the DNC and was immediately hired by Clinton.
July 25, 2016: During an exclusive interview with Democracy Now!, Julian Assange, Editor in Chief of the anti-secrecy website WikiLeaks, said that “no one knows WikiLeaks sources. Claiming one source or another is simply speculation.”
July 30, 2016: The Russian Government FSB reports, through RT, that over twenty high profile Russian organizations and government agencies have been hacked by sophisticated malware to give an example that it is not just organizations in the US that are hacked.
July 31, 2016: Former NSA Lead Administrator, William Binney says the Hack was not done by Russians but by the NSA
On a New York Radio Show, the person who knows more about the power of the NSA than almost anyone in America, former head spy, William Binney explained why the hack was much more likely to be done by the NSA than by the Russians. William Binney worked for NSA for 36 years, retiring in 2001 as the technical director of world military and geopolitical analysis and reporting; he created many of the collection systems still used by NS
During the radio program, Binney specifically referred to the fact that the network server log keeps a record of every IP address that contacts every server. It is these server logs that could provide important clues as to who the hackers really are. But they have never been released.
“William Binney threw his hat into the DNC hack ring by stating that the Democratic National Committee’s server was not hacked by Russia but by a disgruntled US. intelligence worker…concern over Hillary Clinton’s disregard of national security secrets when she used a personal email and consistently lied about it. Binney also proclaimed that the NSA has all of Clinton’s deleted emails, and the FBI could gain access to them if they so wished.”
http://theduran.com/nsa-whistleblower-says-dnc-hack-not-done-russia-us-intelligence/
August 10, 2016: Wikileaks offers $20,000 reward for help in finding Seth Rich killer They issued the following statement: “We treat threats towards any suspected WikiLeaks sources with extreme gravity. This should not be taken to imply that Seth Rich was a source to WikiLeaks or that his murder is connected to our publications.” Later that same day, Wikileaks leader Julian Assange appeared on Dutch television and stated "Whistle-blowers go to significant efforts to get us material and often very significant risks. As a 27-year-old, works for the DNC, was shot in the back, murdered just a few weeks ago for unknown reasons as he was walking down the street in Washington." When the interviewer protested that the murder may have been a robbery, Assange replied “"No. There is no finding. So… I’m suggesting that our sources take risks." Here is a link to the interview. https://www.youtube.com/watch?v=Kp7FkLBRpKg
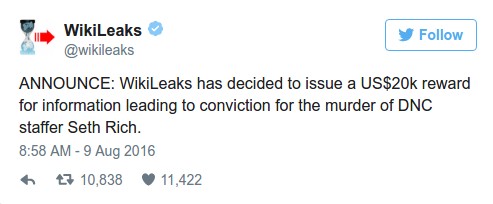
Despite the Wikileaks reward, the Seth Rich murder case has never been solved and remains open today.

