50 years later, another American war hero, General (and then President) Dwight Eisenhower, warned of a growing “military industrial complex” that was a threat to our democracy. Here is a link to his speech. https://www.youtube.com/watch?v=8y06NSBBRtY
Today, the US has more than 700 military bases around the world and numerous bases here in the US. Including secret spending for our new Global War on Terror, as mentioned at the start of this article, the US spends more than one trillion dollars per year on war – much more than the rest of the world combined. http://www.globalresearch.ca/the-worldwide-network-of-us-military-bases/5564
The purpose of this worldwide network of chaos is not to protect Americans but simply to increase corporate profits by sucking one trillion dollars a year out of the American economy – money that could have been used to provide free higher education and health care for every American. Because of this annual feast of a trillion dollars being shelled out, our elected officials have been corrupted with a vast bribery and kickback scheme that has turned our elections into a “pay to play” bidding war between various wealthy corporations. These same corporations monopolize the American media with the goal of scaring the American people into supporting this war machine into voting for war hawks willing to do the bidding of their corporate masters. This same “warfare as a business” model is now being used to create Permanent Cyber War on the Internet. Folks with websites need to be aware of this because you will certainly be caught in the crossfire of this cyber warfare machine.

Thus, the most important thing to know about the current campaign to launch a cyber war against Russia is that it will create massive corporate profits. In the summer of 2016, there was a conference on how to profit from the coming cyber war. This conference was documented in the following article:
https://theintercept.com/2016/08/19/nato-weapons-industry/
False Allegations have been used before to start wars… Doesn’t Anyone Remember the Gulf of Tonkin Incident?
This means that the US is about to start a cyber war with Russia over a hacking incident created by our own NSA. This is nearly identical to the Gulf of Tonkin incident that was used as an excuse by the US military to go to war against Vietnam in the 1960s. That incident turned out to be completely false. Yet millions of people died. The NSA claimed that there was a North Vietnamese attack on August 4 1964. But in 2003, former US Secretary of State Robert McNamara admitted that the the August 4 1964 attack never happened. Moreover, there is substantial evidence that it never happened. The Vietnamese leaders also have confirmed that it never happened. The entire Vietnam War disaster was based on a lie – just like the Iraq War was based on a lie. https://en.wikipedia.org/wiki/Gulf_of_Tonkin_incident

Why Would Our Own Government Lie to Us?
Many readers protested to our previous article asking why our own government would lie to us. I am not certain but I think it has something to do with making money. The Cyber Warfare Industry has become BIG BUSINESS accounting for billions of dollars in corporate sales and profits since 911. All of the attacks on US corporations have forced all of them to hire cyber consultants and buy expensive cyber products to protect their computers and data. There is a danger in developing such a business model as it could lead to nuclear war with Russia. It could also lead to some former NSA employees deciding to take down the US electric grid or US nuclear power plants. We therefore should understand cyber warfare and a business model and take steps to provide real security for our computers, databases and websites.
This is why we should all question the assertion of government officials and their paid consultants like Dimitri at Crowdstrike when they claim that the only possible explanation for the data breach at the DNC or the Podesta email account is highly trained Russian Hackers. When the government or paid consultants make such ridiculous claims, we should all be able to immediately recognize that they are not telling us the truth. Sadly, many American hawks have called for a cyber war against Russia based on these false allegations:
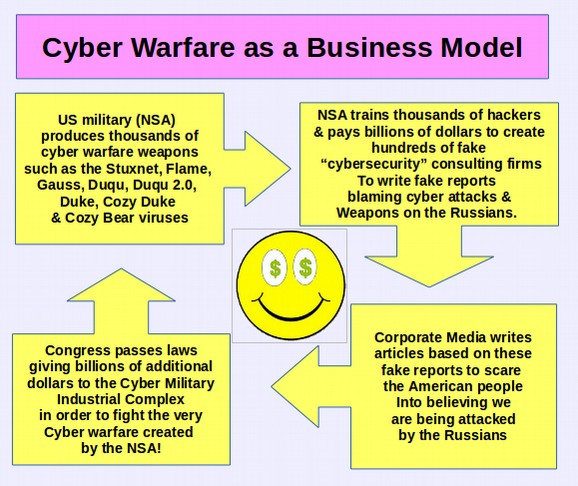
Here is a diagram of how this cyber warfare as a business model works:
The plan to drum up fear of Russians hiding under our beds was in the works long before the November election. Here are a couple of quotes from the article:
“Retired Army Gen. Richard Cody, a vice president at L-3 Communications, the seventh largest U.S. defense contractor, explained to shareholders in December 2015 that the industry was faced with a historic opportunity (to make massive profits off frightened Americans).”
“Speaking to investors at a conference hosted by Credit Suisse in June, 2016, Stuart Bradie, the chief executive of KBR, a military contractor, discussed “opportunities in Europe,” highlighting the increase in defense spending by NATO countries in response to “what’s happening with Russia and the Ukraine.”
“The Aerospace Industries Association, a lobby group for Lockheed Martin, Textron, Raytheon, and other defense contractors, argued in February that the Pentagon is not spending enough to counter “Russian aggression on NATO’s doorstep. Think tanks with major funding from defense contractors, including the Atlantic Council, have similarly demanded higher defense spending to counter Russia.”
What a minute... Don’t we know someone on the Atlantic Council? Now I remember, our friend Dimitri the founder of Crowdstrike is with this war hawk group – the guy who is absolutely certain that Russia is behind Cozy Bear and Fancy Bear stands to make huge profits from scaring the hell out of Americans. That is after all part of the Cyber Warfare Business model. First comes fear based on false claims. Then comes massive profits. As long as we allow people to make billions of dollars from telling lies, we should expect to see more lies being told.
Who has a very long history of hacking elections is not Russia – but the US CIA
The best predictor of future behavior is past behavior. If we look at the past behavior of the NSA and CIA, it is neither good or honest. Instead of pointing the finger at Russia, we need to take a closer look at our own government. There is a Wikipedia page devoted just to the number of countries whose elections were hacked by the CIA.
https://en.wikipedia.org/wiki/United_States_involvement_in_regime_change
Whole books books have been written about this. Just since World War II, our leaders have not only hacked elections in at least 56 other countries, but they have kidnapped and killed the elected leaders of some of these countries. This is much more evil than having Abby Martin say bad things on a talk show two years before an election.
Here is just a partial list (* indicated a successful overthrow):
China 1949 to early 1960s, Albania 1949-53, East Germany 1950s, Iran 1953 *, Guatemala 1954 *, Costa Rica mid-1950s, Syria 1956-7, Egypt 1957, Indonesia 1957-8, British Guiana 1953-64 * Iraq 1963 * North Vietnam 1945-73 Cambodia 1955-70 * Laos 1958 *, 1959 *, 1960 * Ecuador 1960-63 * Congo 1960 * France 1965 Brazil 1962-64 * Dominican Republic 1963 * Cuba 1959 to present Bolivia 1964 * Indonesia 1965 * Ghana 1966 * Chile 1964-73 * Greece 1967 * Costa Rica 1970-71 Bolivia 1971 * Australia 1973-75 * Angola 1975, 1980s Zaire 1975 Portugal 1974-76 * Jamaica 1976-80 * Seychelles 1979-81 Chad 1981-82 * Grenada 1983 * South Yemen 1982-84 Suriname 1982-84 Fiji 1987 * Libya 1980s Nicaragua 1981-90 * Panama 1989 * Bulgaria 1990 * Albania 1991 * Iraq 1991 Afghanistan 1980s * Somalia 1993 Yugoslavia 1999-2000 * Ecuador 2000 * Afghanistan 2001 * Venezuela 2002 * Iraq 2003 * Haiti 2004 * Somalia 2007 to present Honduras 2009 Libya 2011 * Syria 2012 Ukraine 2014 *
https://williamblum.org/essays/read/overthrowing-other-peoples-governments-the-master-list
What is not mentioned in the above list is the CIA “Dirty Tricks” campaign in the 1996 Russian election.
Here is a quote from a December 18, 2016 article explaining what happened:
“(Current CIA Director) Brennan and his cabal of dark players know fully well that it is the CIA that has pioneered in the art and science of election manipulation. In 1996, it was Russia that bore the brunt of CIA election manipulation with its agents-of-influence in Moscow and other large cities, namely the National Endowment for Democracy (NED) and George Soros’s Open Society Institute and Foundation, engaged in political dirty tricks aimed at undermining the electoral chances of the Russian Communist Party presidential candidate Gennady Zyuganov. The CIA, Soros’s operatives, and the NED printed and distributed fake campaign flyers claiming to have originated with the Zyuganov's campaign. The flyers advocated returning Russia to Stalinism and re-launching the Cold War against the West. The CIA and their allies also helped to manipulate election returns and shaved votes from Zyuganov's total, particularly in Tatarstan and Bashkortostan. This helped the favored U.S. candidate, Boris Yeltsin, achieve a second-round victory of 54-to-40 percent over Zyuganov. In 2012, then-President Dmitry Medvedev said, «There is hardly any doubt who won [the '96 election]. It was not Boris Yeltsin».”
http://www.strategic-culture.org/news/2016/12/18/cia-meddles-us-election-as-has-countless-foreign-polls.html
Can you image the outrage that would occur in the US if Russian agents had passed out fliers in major US cities and rigged the actual vote count in several states in 2016? Sadly, the CIA, has not limited itself to kidnapping and killing foreign leaders, it has also conducted “disinformation” campaigns against antiwar protesters here in the US (especially during the opposition to US bombing in the Vietnam War).

Not surprisingly, the CIA is now one of the chief cheerleaders for launching a cyber warfare attack against Russia. What is really needed is an end to the CIA and the NSA. In the meantime, we all need to learn how to protect ourselves against the crazy people currently running the US government.
Conclusion… How to Really Protect Yourself from NSA Cyber Weapons
The first step in protecting yourself from the NSA is to stop using Windows or Apple computers and start using Linux computers. According to Edward Snowden, the NSA has direct access to both Apple and Microsoft (both of whom are NSA Prism Partners). I explain this open back door problem in greater detail in a book called “Free Yourself from Microsoft and the NSA” which you can download for free at the following link:https://freeyourselffrommicrosoftandthensa.org/phocadownload/Free%20Yourself%20from%20Microsoft%20and%20the%20NSA%20Complete%20Book%2016%20MB.pdf
If you do not have time to read the entire 435 page book, it basically explains that Microsoft placed an internet browser inside the core of its operating system in 1997 allowing Microsoft access to your computer whenever you are online so they can check to make sure you have a valid current license. The NSA later demanded and got access to this backdoor. Unfortunately, hackers also have access to this backdoor – which is why there is no such thing as a secure Microsoft computer.
Since Apple is also a PRISM partner, the NSA is able to directly access Apple and Microsoft computers whenever they connect to the Internet (using pre-installed backdoors). This is why Edward Snowden uses Linux computers and programs.
Having confirmed that Windows and Apple computers are not secure, I have written a free book and website on how anyone can convert an inexpensive Chromebook computer into a Linux computer. Here is a link to this website:
https://learnlinuxandlibreoffice.org/
In addition to placing backdoors in Windows and Apple computers, it appears that the NSA has also placed backdoors in the most popular website building program called Wordpress. I have therefore written a free book and website on how to build a more secure website and database system using the Joomla web building platform. Here is a link to this website:
https://createyourowninteractivewebsite.com/
But both of these are only temporary solutions. The real problem is the NSA itself and the entire Cyber Industrial Complex. We will not have real security until we get rid of the NSA. Here is a quote from former CIA Agent Robert Steele who has been a consistent critic of the claim that Russia hacked our elections: “I am deeply offended by the lies being told by the US Government – and more specifically, by the Central Intelligence Agency (CIA), Federal Bureau of Investigation (FBI), and Department of Homeland Security (DHS) with the explicit approval of the Director of National Intelligence (DNI) and the President – with respect to the Russians “hacking” the US election… The only intelligence services that persistently spy on US politicians across every device they own are the US intelligence services, specifically NSA.”
From: The Russians Did Not “Hack” the US Election – a Few Facts from a Former CIA Spy, Global Research, January 08, 2017
http://www.globalresearch.ca/the-russians-did-not-hack-the-us-election-a-few-facts-from-a-former-cia-spy/5567215
How are we going to get rid of this NSA Cyber Warfare monster?
I think the solution is to stop reading the corporate controlled main stream media and start reading the Independent Alternative media. This was one reason we started Turning Point News – to promote Independent News Websites. There is strength in diversity. As far as we are concerned the more independent websites there are, the harder it will be for the NSA to shut us all down. For a list of our favorite independent news websites, see the following link.
https://turningpointnews.org/our-favorite-independent-media-sources
Finally, please share the link to this article with everyone you know who is interested in learning the truth about the Russian hacking allegations. Together, we can and will take back our democracy.
As always, we look forward to your questions and comments.
Regards,
David Spring M. Ed.
Turning Point News.org
07

