Background… Why Fake Finger Prints are Important
On June 15, 2016, a private security firm called Crowdstrike issued a report called “Bears in the Midst” which accused (Russian) groups called Fancy Bear and Cozy Bear of hacking the DNC servers. The accusation was based on the presence of “Russian finger prints” such as Russian Time stamps found in the attacking software. Crowdstrike claimed that these Russian fingerprints were all over the smoking gun found on the DNC server. But we later learned that Crowdstrike is actually an inside group of former FBI cyber warfare leaders who had been working with the DNC for over 9 months and had been working with the CIA for years in an effort to promote the CIA war in the Ukraine.
On December 29, 2016, US spy agencies released a report called Grizzly Steppe which included 876 “Command and Control” IP (Internet server) addresses which supposedly were “evidence” of a vast network of Russian hackers. After this release, I spent the next two weeks researching these 876 Internet servers (see map with their locations below).
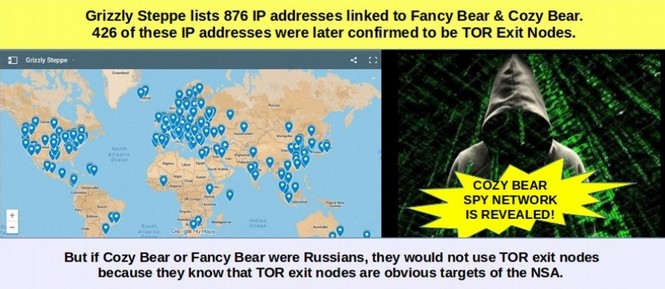
On January 10, 2017, I published an 85 page report called “Hack Everything” that included the results of our extensive research into these 876 Internet server addresses. We found that 426 of these Internet servers were TOR “Exit Node” servers. Russians would not use TOR servers because TOR servers are constantly being attacked by the NSA. Since there are only 1,000 to 2,000 TOR servers in the world, this amazing connection could not be a coinicidence.
I also found that over 80 of the Command and Control Internet servers in the Grizzly Steppe report were located in the US. Russian hackers are unlikely to use even one US server because the NSA and FBI have instant access to every commercial server in the US thanks to the US Patriot Act. Equally strange, nearly all of the remaining Command and Control servers were located in countries friendly to the US. I therefore concluded that the list of IP addresses in the Grizzly Steppe report had nothing to do with Russia and instead was a list of servers compromised by the NSA. In other words, the DNC hack was an NSA operation. The NSA motto is “Collect Everything.” But in order to collect everything, the NSA has to hack everything.
To support this contention, I provided a mountain of additional evidence that both Cozy Bear and Fancy Bear were and still are NSA operations related to the NSA “Equation” Cyber Warfare group. This evidence takes up the bulk of my 85 page “Hack Everything” report. A central claim in my report was that the NSA used Fake Fingerprints to mislead researchers into thinking that Cozy Bear and Fancy Bear are Russian cyber weapons. But other more hidden evidence points directly to the NSA.
The reason I had this mountain of hidden evidence was that I had been studying the NSA for several years. I had concluded several years earlier (in about 2012) that the NSA was the Equation Group and that the Equation Group was linked to both Fancy Bear and Cozy Bear. In other words, while the general public had never heard of Fancy Bear and Cozy Bear, I had been studying them (and several other NSA hacking programs) for several years. I provided a history of Fancy Bear and Cozy Bear and other NSA hacking programs in my 85 page report. I had also concluded years ago that the NSA was using Fake Finger Prints to mislead people into thinking that Fancy Bear and Cozy Bear were Russian Cyber Warfare weapons when in fact both Fancy Bear and Cozy Bear were US Cyber Warfare weapons.
On March 8, 2017, discussing the CIA fake fingerprinting programs, two high ranking former US Intelligence leaders confirmed that is was the NSA and not the Russians who hacked the DNC servers (with one claiming it was former NSA officiers): https://www.youtube.com/watch?v=ij0ShwRx5bc
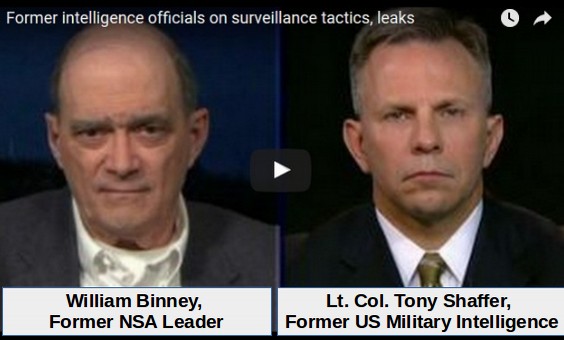
“A lot of the software (such as the fake fingerprinting programs) the CIA uses came from the NSA.” William Binney, Former NSA leader
“We did it... former members of NSA, retired intelligence officers used these tools to break in there (into the DNC servers) and get the information out.”
Lieutenant Colonel Tony Shaffer, Former US Military Senior Intelligence leader
The DNC Attacks Were Both Hacks and Leaks
Ever since June 2016, there has been an intense debate about whether the DNC attack was a hack from an outsider or a leak from a DNC insider. Crowdstrike claims the DNC was hacked (by Cozy Bear and Fancy Bear) - but Wikileaks claims they got the documents from a leak by an insider.
In my 85 page report, I provided a mountain of evidence confirming that there were in fact several attacks on the DNC server and that the attacks were BOTH hacks from the outside and leaks from the inside.
Why the New Wikileaks Documents are Important
The new Wikileaks documents are important for several reasons. First, they confirm that the CIA uses Finger Print misdirection as well as “borrowed” cyber weapons to hide their attacks. If the CIA uses finger print misdirection, we can be confident that the NSA does the same. In fact, we can be pretty sure that the CIA got these misdirection methods from the NSA.

Second, the Wikileaks documents confirm that the CIA failed to adequately secure their cyber weapon arsonal and lost control over thousands of cyber weapons – increasing the likelihood that rogue hackers will now be able to use these CIA cyber weapons to launch their own hacks against people and businesses. One way that this control was lost was by “declassifying” top secret documents and cyber warfare programs. The Wikileaks CIA Press Release described why the CIA declassified much of their cyber warfare weapons:
“How the CIA dramatically increased proliferation risks… the CIA structured its classification regime such that for the most market valuable part of "Vault 7" — the CIA's weaponized malware (implants + zero days), Listening Posts (LP), and Command and Control (C2) systems — The CIA made these systems unclassified. Why the CIA chose to make its cyberarsenal unclassified reveals how concepts developed for military use do not easily crossover to the 'battlefield' of cyber 'war'. To attack its targets, the CIA usually requires that its implants communicate with their control programs over the internet. If CIA implants, Command & Control and Listening Post software were classified, then CIA officers could be prosecuted or dismissed for violating rules that prohibit placing classified information onto the Internet. Consequently the CIA has secretly made most of its cyber spying/war code unclassified.”
In a moment, we will cover how these programs were used on commercial servers to create a “Hacker Heaven.”.
Third, the Wikileaks documents confirm that the CIA has the ability to hide data and malware inside of jpeg and png image files. I have previously written about this hacking method because I have seen it being used in my work on website security. But this is the first confirmation of this tool.
Fourth, the Wikileaks documents confirm that the CIA has over 22,000 servers in the US (although it is uncertain how many of these are Command and Control Servers and how many are simply CIA compromised servers.). This means that the CIA has a huge presence in the US even though they are not supposed to have any presence in the US. While Wikileaks has for the moment redacted the names and locations of these 22,000 IP addresses (apparently to protect the guilty), they did release two CSV files containing lists of servers – including Command and Control servers in Russia! Below is an image of some of these IP addresses listed in the CSV files. I am sure Russian leaders are looking into this matter right now.
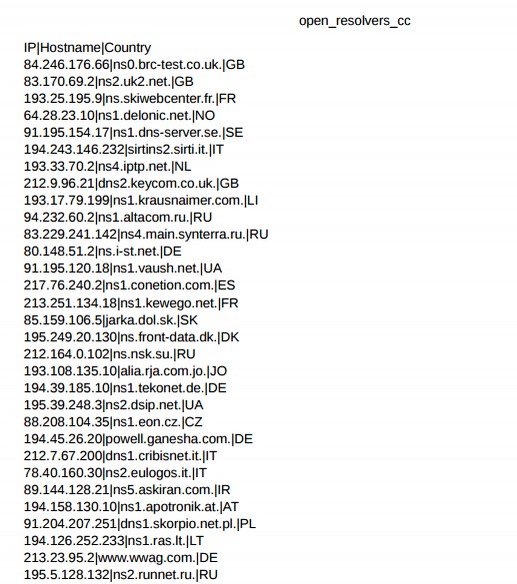
https://wikileaks.org/ciav7p1/cms/page_31227915.html
Here is a brief analysis of just one of the above IP addresses:
94.232.60.2 is a broad band server in Russia owned by a company called Infanet CJSC which has 2048 IP addresses but does not appear to offer any services. Their website was registered in 2008. Here is there address and website:
| Cheboksary, Russia, Altacom.ru and alfatelecom.cz Their mail is handled by yandex.ru. |
|
“To exfiltrate data back to the CIA or to await further instructions the malware must communicate with CIA Command & Control (C2) systems placed on internet connected servers. But such servers are typically not approved to hold classified information, so CIA command and control systems are also made unclassified."
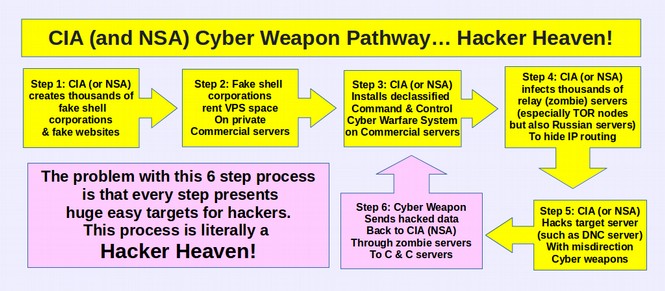
What the general public may not know or understand is that there are several different kinds of Internets. The public is only aware of the public Internet. But corporations and the US military have their own private servers and their own private intranets. In order of security, the most secure method is to buy your own private servers and not hook them up to the public internet at all. Alternately, you could have a firewall between your private server and the public internet. The problem with this method is that the private IP address associated with the private server would be exposed. So instead, in an effort to make it look like they are just normal traffic on the normal public Internet, the CIA (and NSA) have been spending huge amounts of money renting space on thousands of commercial servers.
There are three basic ways to rent space on commercial servers. The first is to rent the entire server. The second way is to rent a section of a commercial server. This is called a Virtual Private Server or VPS. The third way is to simply rent a block of data in a folder on a commercial server. This is called “Shared Hosting” and it is what most low tranffic websites do. None of these methods are very secure as they rely entirely on a third party to protect the server from attack. Also, these commercial servers are always connected to the public Internet. Because of this, commercial servers are always under constant attacks from hackers with hundreds of attacks every hour every day.
The Wikileaks documents reveal that the CIA was and is renting space on commercial servers hooked up to the public internet to relay hacked information. Based on my research of NSA IP addresses, the NSA is doing the same thing. So this is not just a CIA shortcoming. This is an entire completely insecure way of transmitting data. By law, the NSA and CIA are not allowed to transmit secret data over the public Internet for the important reason that the public internet is not really that secure. But rather than following the law and doing the smart thing and keeping top secret documents off the public internet, the CIA (and NSA) simply declassified top secret information so they could transmit it over the public internet. This is worse than insane. This is worse than reckless. This is treason on a massive scale.
According to various Wikileaks CIA documents, here is what the CIA and NSA are doing:
Sixth, Wikileaks documents confirm that the NSA is the Equation Group as CIA operatives refer to the Equation group as an NSA operation. Until now, there was strong evidence that the Equation Group was the NSA. Now it is a fact. This matters because the Equation Group has been responsible for producing some of the most dangerous cyber weapons in existence. We now can be certain that these weapons were produced with more than one trillion dollars in US tax payer funds (the budgets for the NSA and CIA for the past 15 years).
Seventh, the Wikileaks documents include a CIA article called “What did Equation do wrong, and how can we avoid doing the same?” This article refers specifically to the Kaspersky Report on the Equation Group (which I quoted and discussed in detail in my 85 page report). The CIA authors then detail numerous ways the CIA can trick Kaspersky (and other cyber warfare researchers) in order to hide the CIA cyber warfare attacks. We can be certain that Kaspersky and other researchers are reviewing these new Wikileaks documents and adjusting their research methods right now.
Eighth, and perhaps most important, the Wikileaks Vault 7 documents includes tables of Zero Day exploits used by the CIA to attack Windows and Apple computers. Zero Day exploits are attack methods that the manufacturers are not aware of and thus have not fixed. They are extremely dangerous open back doors into computer systems.
What is shocking about these tables is that the CIA admits to “buying” these dangerous hacking methods from hackers. These tables confirm that the NSA also buys Zero Day exploits. This is also not only an extreme misuse of US tax payer dollars, it is a violation of federal law which requires that these exploits be given to corporations such as Apple and Microsoft so they can patch their code and prevent cyber attacks from bringing down the entire US economy. Zero Day attacks are like nuclear weapons. The last thing the US should be doing is hording them and/or paying hackers for them as these attack methods can cause horrific damage to computer systems all over the globe once they get into the wrong hands. This is completely insane.
Here is a portion of this table with Apple Zero Day exploits:
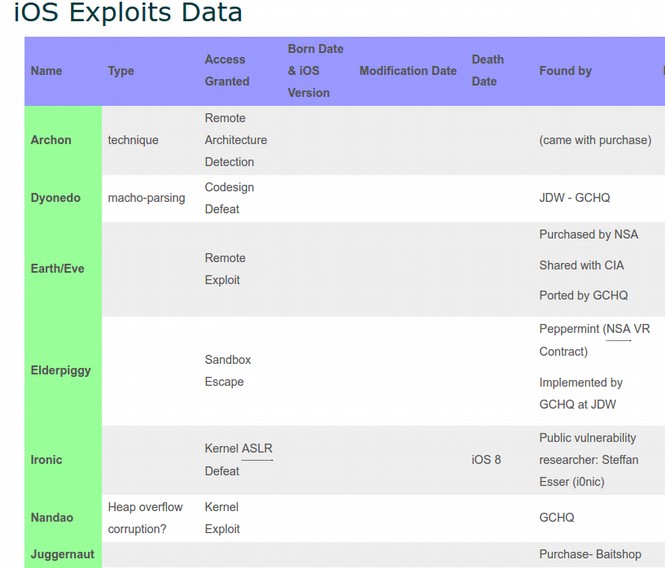
The above table also confirms that there is close cooperation between the NSA and CIA in that they are sharing many of the same extremely dangerous cyber warfare weapons. In short, both the NSA and CIA need to be stopped before they destroy the entire planet.
Here is what Edward Snowden had to say about the US government paying to weaken the security of US technologies:"The CIA reports show the USG developing vulnerabilities in US products, then intentionally keeping the holes open. Reckless beyond words. Why is this dangerous? Because until closed, any hacker can use the security hole the CIA left open to break into any iPhone in the world."
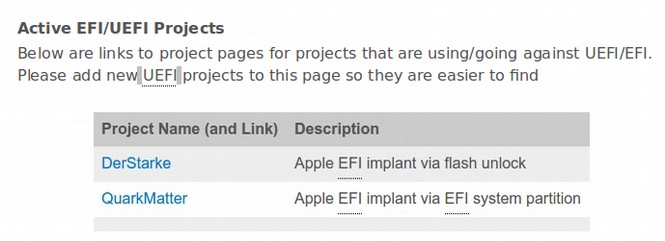
There are many other shocking cyber weapons confirmed for the first time in the Wikileaks CIA documents. For example, they have a whole division devoted to exploiting weaknesses in the UEFI computer start up program. These exploits mean that all Apple and/or Microsoft computers can be remotely “bricked” at a moments notice to the point where your computer will simply turn itself off and can not be turned on again. I have been writing about this danger for several years. Finally, thanks to these new Wikileaks documents, we have proof positive that this kind of extremely dangerous UEFI boot cyber warfare is in fact occuring.
A final important point is that Wikileaks has confirmed that there is no way to protect the public from cyber warfare weapons. Once produced, it is inevitable that at some point hackers will get hold of them. Our only real security is to not produce cyber weapons in the first place. In a press conference on March 9, 2017, Julian Assange stated that cyber weapons cost companies around the world “billions of dollars” in losses. I think this is a major understatement. In fact, cyber weapons have caused companies trillions of dollars in losses. As just one example, a cyber weapon created by the Equation Group (NSA) was the underlying cause of the BP Gulf Oil Spill – which caused devastation to the entire SE section of the US.
Assange also noted during his March 9 2017 press conference that eventually consumers around the world will no longer trust US technology manufacturers – which will also cost US corporations billions of dollars. The mere fact that US corporations have already been confirmed to be Prism Partners of the NSA should cause folks even in the US to not trust US technology firms. The new Wikileaks revelation that the CIA has compromised 22,000 servers in the US should make it clear that we cannot trust US web servers and web hosts – a fact that I wrote about in a book over a year ago.
https://createyourowninteractivewebsite.com/1-start-here/1-3-how-to-protect-your-website
The only good news is that, as I have also written about for many years, the CIA (and the NSA) are having trouble hacking Linux computers. This is almost certainly due to the distributed nature of Linux operating systems (there are more than 100 variations) and the fact that the Linux operating system specifically excludes web browsing tools from the core of the operating system. Below is an image of the CIA Linux hacking page confirming that CIA efforts to hack Linux computers is still incomplete:
Clearly the NSA and CIA are trying very hard to break into the Linux operating system. But so far, their only success has been by compromising the UEFI startup program. This is why I recommend that even if you are using a Linux computer, you should not use the UEFI startup program and instead to use the COREBOOT startup program. Meanwhile the Apple and Windows pages in the Wikileaks documents are filled with hundreds of attacking methods. The Windows page has hundreds of attack methods divided into several categories:
As I have written about repeatedly over the years, the CIA (and the NSA) often use fake Windows Updates to attack Windows computers through the web browser that is buried deep in the core of the Windows operating system. It is not just the CIA and NSA that use these open back doors, but nearly all hackers. Bottom line is that if you are concerned about security, you should not be using Windows or Apple computers. You should be using Linux. For more information on this subject, see my website: https://learnlinuxandlibreoffice.org/
We Owe a Great Deal to Courageous Whistleblowers
The only way we even know about these CIA cyber weapons that have been released into the wild is thanks to the courage of whistleblowers. There is no question that the person who released this information to Wikileaks will now be the subject of a massive manhunt by the US Deep State. If caught they will almost certainly be tortured and possibly even killed. There will also be increased efforts to bring down Wikileaks and destroy Julian Assange. We have already seen what the Deep State did to Chelsea Manning. A similar fate might await Edward Snowden. We should therefore never forget the sacrifices these patriots have made to protect what remains of our freedom and our right to know the truth about what our government is really up to. If we fail to protect and stand up for these whistleblowers, the day may come when we no longer have access to the truth.
Conclusion
I have spent years studying the NSA. I mistakenly thought it was the biggest and worst threat to world peace and the world economy. I now realize I was wrong. The CIA appears to be twice as large as the NSA. This is like doing battle against Godzilla for several years only to wake up one morning and learn that there is another monster twice the size of Godzilla. I was having trouble sleeping before these new Wikileaks CIA documents. Now I am really having trouble sleeping.

Wikileaks has said that the 8,000 pages are just one percent of the total CIA information they have. This means that the total release of CIA documents might go as high as 800,000 pages! Just as the Snowden documents in June 2013 confirmed my prior research, the Wikileaks documents in March 2017 have provided further confirmation that my concerns about the NSA and CIA hacking operations were well founded.
These are important security issues that affect every computer user in the entire world. It is time not only to end the NSA and CIA but it also time for every computer user who cares about the future of our economy to move away from unsafe and badly designed operating systems such as Microsoft and Apple and replace them with the free, secure Linux Operating system. Here is a link on how to make the move to Linux: https://learnlinuxandlibreoffice.org/
It is also time to move towards securely encrypted email such as Protonmail.com. Here is a qoute from the founder of ProtonMail: “This opens up a terrifying new narrative where government spies are actively deploying viruses and trojans against their own citizens, joining the ranks of common cybercriminals.”
It is also time to put an end to the crazy Russian hacking stories. The real enemy of the people is not Russia. It is the spy network right here in the US. The greatest danger to our freedom is our own CIA and NSA.
Please share this report with anyone you know who is interested in learning the truth about the 2016 DNC hack. As always, we look forward to your questions and comments.
Regards,
David Spring M. Ed.
Turning Point News.org
Email: david (at) turningpointnews.org