December 29 2016: The DHS/FBI Grizzly Steppe Report Turns out to be Proof that the NSA does not like the TOR Project
The Department of Homeland Security and the FBI release a joint report which they claim provides evidence of Russian Hacking of the US Election. In fact, there is no evidence in the report linking Russia to anything. But there is plenty of evidence linking the attacks to the NSA.https://www.us-cert.gov/sites/default/files/publications/JAR_16-20296A_GRIZZLY%20STEPPE-2016-1229.pdf
The “alternative names list” for the Russian hacking programs on page 4 specifically referred to in the DHS/FBI report included the following: Cozy Bear, Cozy Duke, Cosmic Duke, Fancy Bear and MiniDuke.
As justification for launching a cyber war against Russia, on page 5 of their press release, the US government also falsely accused the Russians of creating a hacking program called PAS_TOOL_PHP_WEB_KIT. This web kit is a commonly available hacking program that even you can download. The following article claims that this program was made by Ukrainians not Russians.
https://www.wordfence.com/blog/2016/12/russia-malware-ip-hack/
The DHS/FBI press release and numerous main stream media reports also noted that several private cyber security consultants agreed that the Russians were responsible for hacking the DNC and specifically that Fancy Bear and Cozy Bear were involved in the DNC attacks. For example, see the following fake news from NBC:
http://www.nbcnews.com/news/us-news/cozy-bear-explained-what-you-need-know-about-russian-hacks-n648541
December 30 2016 Glaring Problems with the Grizzly Steppe Report
Beginning on December 30, 2016, several articles were written exposing problems with the Grizzly Steppe report. I wrote an article with screen shots of the data file and an analysis of many of the IP addresses. This analysis showed that the IP addresses had no link to the Russians. You can read this short report at this link:https://turningpointnews.org/exposing-political-corruption/dhs-fbi-claim-of-russian-hacking-is-fake-news
TOR Exit Nodes… The Real Smoking Gun
In my report, I provided research on several domain names and IP addresses provided in the Grizzly Steppe report. My research showed that none of the domain names or IP addresses had any relationship to Russian hackers. But one of the IP addresses was a TOR Exit Node. Here is a quote from my report:
“178.20.55.16 is a proxy server with no known location but has been used as a TOR router exit node. A proxy server is another name for a mirror or server used to bounce information from one server to another in order to hide the true location of the original server. This proxy server is associated with the domain name nos-oignons.net. This domain name was registered on December 31 2012 and is valid until December 31 2017. In other words, whoever got this domain name paid for its use for 5 years. But they did registered the domain name anonymously. The website associated with this server appears to be a group in France promoting the TOR router. They became an association in May 2013 – 5 months after getting the domain name. The group currently has 5 members and it costs one Euro to join this group. Their website was reported 9 days ago as having been infected with the Zeus virus. This infection does not leave tracks on server logs. So it is difficult to tell where it came from. Removal of this virus requires a complete rebuild of the server. In short, some agency decided to take out this server and then use it to make a cyber attack on some US government agency and thus have the IP address listed on the DHS-FBI list as one of 895 indicators of Russian hacking.”
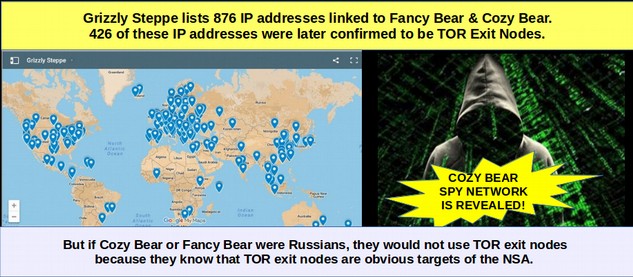
As discussed earlier in this report, research by others has now confirmed that there were 426 TOR exit nodes on the Grizzly Steppe list. Thus about half of the Grizzly Steppe list were TOR exit nodes. More important, since there are only about 1,000 TOR exit nodes in the entire world, about 42% of all TOR exit nodes were on the Grizzly Steppe list. Since the general public has no idea what TOR is and why this is important in terms of linking the NSA to the DNC hacks, we will provide a brief explanation of TOR.
What is TOR?
TOR stands for the The Onion Router. The Onion Router is a web browser, similar to Firefox or Google Chrome. But it is also a network of proxie servers used to hide the idenity and location of the person visiting the TOR web browser. The route taken by the data is passed through several TOR IP addresses bouncing the signal all around the world. The only thing that can be confrimed is the final step in this path. The final step is called a TOR exit nodes. Anyone, including the NSA can tell the location and identity of the server at the final step. Because the NSA does not like people hiding from them, the NSA does not like TOR. The NSA therefore has a long and ugly history of attacking TOR exit nodes (as well as attacking the TOR home website). TOR exit nodes take great risks in that they stand in the way of the most powerful hacking group in the world – the NSA.
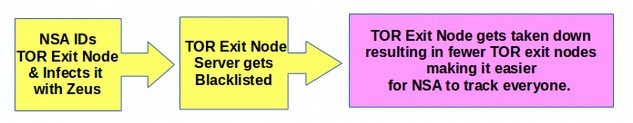
How the NSA attacks TOR exit nodes is very devious. But I did briefly explain this in my previous article on December 30, 2016. Basically, the NSA attacks the server that the exit node website is located on and infects the server with a very bad virus. Zeus is only one of several viruses used by the NSA. Also the NSA is not the only one using Zeus to infect websites and servers as Zeus is readily available on the Internet.
As I stated in my prior article, once the server is infected, folks begin to file complaints about it to blacklisting agencies. The servers are quickly blacklisted and their content is no longer shown. The company owning the infected server needs to take it off line and clean it up (not an easy process) before putting it back up. The server then needs to prove to the black listing agencies that it is completely clean before traffic is restored. Here is a diagram of this NSA TOR server take down process:
This is why the presence of such a huge number of TOR exit nodes in the Grizzle Steppe list is so alarming. It is clearly a smoking gun that the Grizzly Steppe list is a list of servers being targetted by the NSA. Since this is also a list of IP addresses that have been associated with Fancy Bear and Cozy Bear, we can conclude that there is some relationship between Fancy Bear and Cozy Bear to the NSA. If Russia were really Fancy Bear or Cozy Bear, they would not be using TOR exit nodes for the simple reason that TOR is one of the biggest threats to total NSA domination of the Internet. In addition, they would not use TOR exit nodes because they are certainly aware that TOR Exit Nodes are being targeted and taken down by the NSA. Russian hackers know which servers are TOR exit node servers because TOR publishes a list of these servers. Here is a link to this list: https://check.torproject.org/exit-addresses
It would be a simple matter for Russian hackers to use servers that are not TOR exit node servers. Thus, the Grizzly Steppe IP list is proof that Cozy Bear and Fancy Bear are not related to Russian Hackers. They are NSA hackers. Here is a link to the TOR website where you can download TOR and learn more about it. https://www.torproject.org/

There were several other excellent articles shooting holes in the DHS/FBI report. This is a brief summary of two of the best that provided very strong evidence that Russia was not involved in the hacking of the DNC:
#1 TOR EXIT NODES IMPLICATE NSA AS THE DNC HACKER: The 876 alleged Russian Hacking attacks in the DHS/FBI report come from IP addresses in 62 countries all over the world. Nearly half of them (49%) are TOR Exit nodes. Here is a map of attacks:
http://jerrygamblin.com/2016/12/30/grizzly-steppe-ip-and-hash-analysis/
As I noted in my first report, these IP addresses are mostly outside of Russia with the US being the most common location. 367 of these IP addresses (or 42% of the total in the report) are now or in the past were TOR Exit Nodes meaning that anyone can use them.
https://theintercept.com/2017/01/04/the-u-s-government-thinks-thousands-of-russian-hackers-are-reading-my-blog-they-arent/
Here is a quote from the above link:
“I found out, after some digging, that of the 876 suspicious IP addresses that the Department of Homeland Security and the Department of National Intelligence put on the Russian cyber attacker list, at least 367 of them (roughly 42%) are either Tor exit nodes right now, or were Tor exit nodes in the last few years...(using a more complete data set of historical TOR exit nodes), it turns out that 426 of the IP addresses in the Grizzly Steppe report are historical Tor nodes, so it’s actually 49% rather than 42%.”
Many more of these Grizzly Steppe IP addresses are public broadband servers also easily accessed by almost anyone. I understand that hackers can create bot nets which combine thousands of hacked servers together to make Denial of Service attacks. But that is not what the DHS/FBI report is alleging. They are alleging 876 separate hacking attacks from 876 separate servers.
Our prior article diligently reviewed many of these Grizzly Steppe IP addresses and could not find any link at all to the Russian government. But we did find some links to the NSA. For example, we provided a link to a hacked TOR node in France. Over 300 of the IP addresses provided in the DHS/FBI report are from hacked TOR Exit nodes – meaning that these exit nodes have been blacklisted and will soon be taken off line. Such a massive attack against the TOR project is devastating because there are only about 1000 TOR exit nodes in the entire world. https://metrics.torproject.org/relayflags.html
Whoever Cozy Bear and Fancy Bear are, they seem to be interested in taking down the TOR project. Who in the world would want to get rid of so many TOR exit nodes??? TOR exit nodes provide an important public service by allowing folks to surf the Internet anonymously. The TOR anonymous web browser has about 1.5 million daily users.
Getting rid of the exit nodes would be the end of the line for the Tor Project.
It turns out that the NSA does not like TOR because it makes hacking harder for the NSA. The NSA has been known to attack the TOR project in the past. In fact, according to documents leaked by Edward Snowden, the NSA uses three or more cyber weapons to attack the TOR project and has referred to the TOR project as one of their biggest obstacles in their drive for “Total Awareness.” These weapons are called Quantum, Foxacid and XkeyScore.
Here is an article that discusses these attacks calling TOR a “high priority target of the NSA”:
https://www.schneier.com/blog/archives/2013/10/how_the_nsa_att.html
The fact that 426 of the IP addresses are or were TOR exit nodes most of which were hacked is further strong indication that the above IP map implicates the NSA rather than the Russians. The NSA has been attacking TOR exit nodes for years in an attempt to get rid of TOR. The list of 876 IP addresses provided in the DHS/FBI report does confirm that Cozy Bear and Fancy Bear have been active. But this list also supports my claim that Cozy Bear and Fancy Bear are NSA hacking projects – not Russian hacking projects.
Moreover, the NSA has the money to be hacking sites in 62 countries whereas the Russians have a more limited budget and cannot afford to be hacking computers in 62 countries.
Why Russian Hackers would not use US Servers to Call Home
In addition to 426 of the Cozy Bear/ Fancy Bear servers being TOR exit nodes, over 80 servers had IP addresses located in the US.
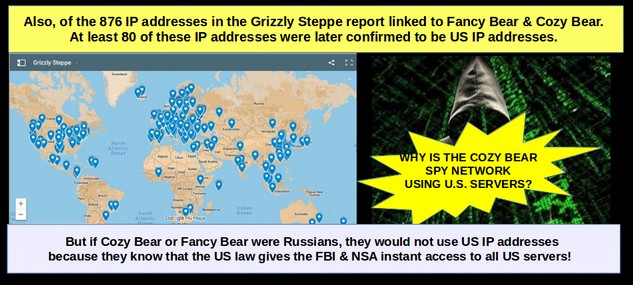
In addition, over 90% of the IP addresses were in countries friendly to the US. Even the IP addresses located in Russia were found to be broadband addresses available to the general public. It is unlikely that Russian hackers would be using any of these IP addresses for their spy network.
Let us be clear. We are not at all saying that the Russians never hack US computers. We have no doubt that the Russians try to access US government computers on a daily basis (as do many other governments and as do a bunch of teenagers from from across the US). Talk to any hacker at a hacker conference and you will find out that nearly all of them would like to hack US government servers. This is just how hackers are. They like a challenge. We are simply reviewing the evidence for Cozy Bear and Fancy Bear because the DHS/FBI report claimed that they were both Russian hacking programs. Our review of the evidence indicates that these programs are not Russian programs but NSA programs.
#2 The DHS/FBI claim that a PHP script was evidence of Russian hacking proven to be false
On page 5 of their press release, the US government falsely accused the Russians of creating a hacking program called PAS_TOOL_PHP_WEB_KIT. Here is a link to a report which goes into detail on why this PHP script cited by DHS/FBI was not evidence of Russian hacking.
https://www.wordfence.com/blog/2016/12/russia-malware-ip-hack
The authors easily obtained the PHP script by googling it which led to this download link:
http://profexer.name/pas/download.php
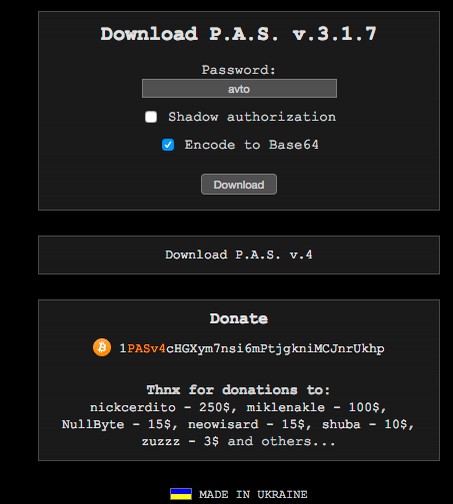
Note the Ukrainian flag and the claim it was “Made in Ukraine”. This is pretty typical of the NSA coders sense of humor. You can make a donation to the hacking team by clicking on an anonymous Bitcoin link. This is also typical NSA humor. The latest version of this hacking program, which is intended to hack Wordpress websites, is version 4.1.1.
Here is what the control panel of this hacking program looks like:
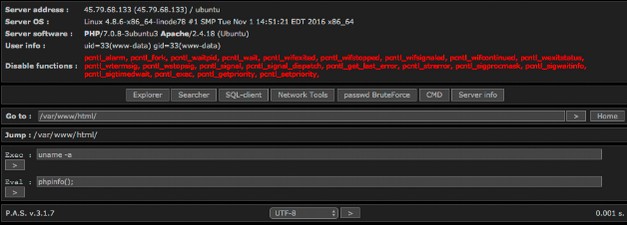
This free and handy open source hacking program includes a file browser, a file search function, a database to download the contents of a hacked site database, a scanner, a tool to view server configuration files and a tool to brute force attack passwords. Best of all, all of the instructions and the control panel itself are written in English – no need to learn Russian!
Every American should be disgusted and alarmed that this easily available program was attributed to the Russians in the DHS/NSA Report and this same program is now being used as an excuse to launch a cyber warfare attack against Russia. This madness has to be stopped. Please share this information with everyone you know!
December 30, 2016 Security Expert John McAfee Explains why he is certain the Russians did not hack the DNC
This is a quote from a TV interview:“When the FBI or any other agency says the Russians did it or the Chinese did it, or the Irans did it, that is a fallacy. Any hacker capable of breaking into something is capable of hiding their tracks. If I were the Chinese and I wanted to make it look like the Russians did it, I would use Russian language within the code. I would use Russian techniques for breaking into an organization. So there is simply no way to assign a source for any attack. This is a fallacy. This is what the FBI wants us to believe so they can manipulate our opinions. I can promise you this. If it looks like the Russians did it, then I can guarantee you it was not the Russians.”
https://www.youtube.com/watch?v=aDTKKmBjlwE
John then appeared on another show and said he thought it might be a 15 year old boy since the person made some basic errors. Here is a quote from John:
“The hack on the DNC used a piece of malware a year and a half old. This was done by an independent one person kid. This was not an organized state that did this. “We have many cyber weapons but we have no protection. We have no security. If we did, our country could not have been hacked by a 15 year old boy.”
“The Grizzly Steppe Report is not just flimsy. It is propaganda intended to incite the American people.”
https://www.youtube.com/watch?v=C2jD4SF9gFE
https://www.rt.com/usa/372219-larry-king-mcafee-cybersecurity/#.WGaDFP9c4q4.facebook
John has been interviewed on several TV and Radio shows and is likely the leading proponent of the theory that the DNC was really attacked by teenagers.

In fact, it was the 2015 German hack that used a piece of malware a year and a half old and therefore was likely done by a teenager. We have no idea what version of software was used in the DNC hack because the FBI never did an investigation and Crowdstrike has never released the source data (merely making claims about the source data that it was linked to the German attack).
We have great respect for John and will consider his argument in more detail later in this report.

