This leads to the important question of how Wikileaks got all of the emails and other data it released which certainly did influence the outcome of the US elections. According to both of the major sources in Wikileaks, Julian Assange and Craig Murray, they got the data from “a disgusted DNC Democrat” who was mad about how the DNC treated Bernie Sanders.
http://www.washingtontimes.com/news/2016/dec/14/craig-murray-says-source-of-hillary-clinton-campai/
Both Murray and Assange have repeatedly stated that they did not get the information from the Russians. We therefore conclude that if the DNC was hacked (which it likely was), then it was hacked by the NSA using Cozy Bear and Fancy Bear as a cover – knowing that Cozy Bear and Fancy Bear were specifically written to fool consultants like Dimitri and Cloudstrike into thinking that it was a Russian hacking program. Obviously, the NSA is not going to give any of its information to Wikileaks. But in addition to these two hacks by Cozy Bear and Fancy Bear, a disgusted member of the DNC also got the information directly from the DNC database, put it on a jump drive and handed the jump drive to Craig Murray. In other words, we conclude that the DNC was hacked and also subjected to an insider leaker. Thus, Wikileaks claim that it was a leak is true. But their claim that it was not a hack may not be accurate as there is evidence of a hack.
The Difference Between a Leak and a Hack
Here is a link to a group called Veteran Intelligence Professionals for Sanity who outline the capability of the NSA and explain the difference between a leak and a hack:
https://consortiumnews.com/2016/12/12/us-intel-vets-dispute-russia-hacking-claims/
Here is a quote from this group of US Intelligence veterans:
“Leak: When someone physically takes data out of an organization and gives it to some other person or organization, as Edward Snowden and Chelsea Manning did.
Hack: When someone in a remote location electronically penetrates operating systems, firewalls or any other cyber-protection system and then extracts data.
All signs point to leaking, not hacking. If hacking were involved, the National Security Agency would know it – and know both sender and recipient. Any data that is passed from the servers of the Democratic National Committee (DNC) or of Hillary Rodham Clinton (HRC) – or any other server in the U.S. – is collected by the NSA.”
Here are the signers of this statement:
For the Steering Group, Veteran Intelligence Professionals for Sanity (VIPS)
William Binney, former Technical Director, World Geopolitical & Military Analysis, NSA; co-founder, SIGINT Automation Research Center (ret.)
Mike Gravel, former Adjutant, top secret control officer, Communications Intelligence Service; special agent, Counter Intelligence Corps and former United States Senator
Larry Johnson, former CIA Intelligence Officer & former State Department Counter-Terrorism Official
Ray McGovern, former US Army infantry/intelligence officer & CIA analyst (ret.)
Elizabeth Murray, Deputy National Intelligence Officer for Middle East, CIA (ret.)
Kirk Wiebe, former Senior Analyst, SIGINT Automation Research Center, NSA (ret.)
These are six of the leading NSA whistleblowers and everyone one of them knows the full horrific power of the NSA. If only all Americans knew what these six people know (The main reason I am writing this article is to help increase the awareness of the American people about the true power of the NSA). Sadly, most Americans are not even aware of the difference between a leak and a hack and thus are easily misled by the current campaign to blame Russia for whatever cyber attacks are occurring in the US.
Were either Cozy Bear or Fancy Bear Teenage Hackers?
Since the DNC hackers made some rather basic mistakes, some have concluded that either or both of the hacks could have or must have been done by bored teenagers. There are many recent examples of teenagers hacking computer systems much more secure than the DNC server to support this theory.
On February 19, 2016, a 15 Year old boy arrested for hacking the FBI on February 16, 2016. He was part of a group that repeatedly attacked the FBI and CIA over a period of several months.
http://thehackernews.com/2016/02/fbi-hacker-arrest.html
Here is a quote: “Another 15-year-old teenager got arrested in Scotland, by British Police for breaking into the FBI Systems on 16th February. Under the Britain’s anti-hacking law, Computer Misuse Act 1990, the boy has been arrested for his role in hacking and unauthorized access to the digital material. Another member of the same group got arrested from the United Kingdom last week. The 16-year-old British teenager was suspected of hacking into the CIA and the FBI.
The two boys had downloaded more than 200 Gigabytes of top secret data on tens of thousands of FBI agents and other high level officials in the FBI, CIA and DHS. The boys also hacked into AOL emails of CIA director John Brennan and hacked into the personal phone accounts and email accounts of the US spy chief James Clapper of the FBI Deputy Director Mark Giuliano.
Here is another article about this attack: How did a couple of boys bring down the entire US Intelligence system? They claimed that they got into the US Department of Justice email account. From there, it was simply a Sunday joy ride through all of the data of the FBI, CIA and DHS. This was all done on line through their home computer using information readily available on the Internet.
http://thehackernews.com/2016/02/fbi-dhs-hacked.html
Nor is this an isolated incident. In 2015, a 14 year old boy began shutting down government and corporate computers all over the world from the comfort of his bedroom. He eventually got caught after using Skype (which has a direct link to the NSA). The judge decided not to send him to jail reasoning that jail would destroy him and he had “just gotten carried away thinking he was cool.” She did order that his computer be destroyed to reduce the chances of any future attacks.
http://www.telegraph.co.uk/news/2016/07/20/teenage-hacker/
Here is a link to a story about 10 teenage hackers:
http://www.huffingtonpost.com/2012/07/18/teen-hackers-10-stories-o_n_1683387.html
Here are some quotes from the article:
“Over the past two years, we’ve seen a ton of stories about teenage tech geniuses who have pushed legal boundaries by cracking the codes of governments and other major institutions, sometimes from their own bedrooms. From a 15-year-old who broke into over 250 websites to the 18-year-old who took down Lady Gaga, click through the slideshow below for some of the most unbelievable teen hackers who have made headlines recently.”
“In 2011, British teens Ryan Cleary, 20, and Jake Davis, 19, made headlines for targeting the CIA, the Pentagon, NHS, Sony, Nintendo and The Sun. Most notably, the pair - known as "LulzSec" online - pranked The Sun by replacing its homepage with a spoof of Rupert Murdoch's obituary.”
“18-year-old hacker, who called himself DJ Stolen, hacked into the personal computers of several pop stars. He stole multiple unreleased tracks from Lady Gaga, Ke$ha, Leona Lewis, Justin Timberlake, and Mariah Carey over the course of two years and sold them online.”
“In April, 2012, the Austrian police arrested a 15-year-old for hacking into a shocking 259 companies. He is the country's youngest arrested hacker and is estimated to have broken into an average of three sites per day.”
“A Greek teenager was arrested last year for allegedly hacking into websites of the U.S. government and Interpol, ending a two-year chase. A raid of his house revealed 130 fake credit cards. Allegedly, his back is tattooed with the statement, "Capitalism is opportunity and opportunity is freedom."
“Two Norwegian teens were arrested in connection to a string of computer attacks. The BBC alleges that the targets may have included the British Serious Organized Crime Association, the Norwegian lottery, and a German newspaper.”
My point in telling these stories is to demonstrate how poor Internet security really is right now. Those who claim that teenage boys could not possibly hack into the DNC server simply do not know what they are talking about. As noted earlier X Agent is out in the wild and available to be used by anyone. Windows computers and servers are particularly susceptible to hacking due to the always open NSA back door. Until adults do a better job of demanding secure computers and servers, we are going to see even more stories of teenagers hacking into government and corporate computer systems.
Earlier I explained why I concluded that the 2015 German Parliament Fancy Bear attack must have been a teenager. The heartbleed problem with Open SSL is simply too well known for either the Russians or NSA to be that dumb. Without more accurate research and information, it would be impossible to tell for sure who hacked the DNC in September 2015 and March 2016.
However, in the preceding pages I have analyzed many IP addresses that all lead to what look to me to be NSA servers. Ironically, what really tipped the scales towards this conclusion was the list of IP addresses in the December 2016 Grizzly Steppe Report. There is no other rational explanation for so many TOR exit nodes appearing in any list other than concluding it was the NSA trying as usual to get rid of TOR. Teenagers would have no interest in attacking the TOR project. In fact, they would have a strong interest in protecting the TOR project as it would be the main thing reducing the chances of being captured.
How Many Leaks or Hacks Were There and How Many Data Dumps Were Given to Wikileaks?
Wikileaks has stated at various times that their source was a disgusted Democratic Party insider who leaked information they had gotten directly from the DNC server. But Wikileaks has also stated at other times in other interviews that their source was a disgusted US Intelligence Agent – meaning someone from the NSA, CIA or FBI got data indirectly through a hack and then gave the data to Wikileaks.
In researching our detailed timeline of events, it appears that Wikileaks was actually given as many as four sets of data at various points in time. First, they were given data from the Clinton private server which they published on March 16, 2016.
Then they were given data from the DNC server which they published on July 22, 2016 (this is what led to the resignation of the DNC Chair and the walk out of Bernie delegates at the Democratic National Convention). They appear to have had this data since some time in May 2016.
Then they published the Podesta emails and Clinton Wall Street speeches beginning on October 7, 2016. According to Craig Murray and others, they seem to have been given this information from one or more sources in September 2016. Thus, there was a combination of leaks and hacks involving several servers and several sources and that the answer to the question of who provided information to Wikileaks is “All of the above.”
The following is the timing of Wikileaks Data Dumps as taken from the Wikileaks website:
https://wikileaks.org/-Leaks-.html
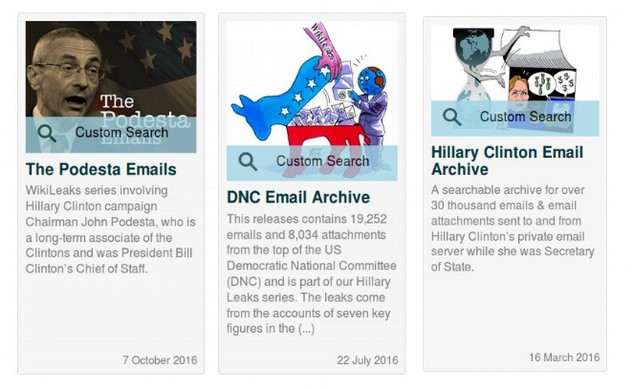
As just one possible example, the Clinton emails could have come from a teenage hacker, the DNC emails could have been a leak from a digusted Democratic Party insider and the Podesta emails and Wall Street speeches could have come from a disgusted NSA agent using the Cozy Bear and/or Fancy Bear hacks on the DNC and or Podesta Gmail accounts.
What would help clarify who gave what and when would be the release of the DNC server logs. I am really disappointed that the FBI has not released the server logs and that they failed to do a proper investigation in September 2015. But even without this information, we have provided at least 20 reasons in this report to conclude beyond any reasonable doubt that it was not the Russians who attacked the DNC. Thus, there is no honest reason to start a cyber war against Russia. However, I think our government will try to start a cyber war against Russia for the simple reason that a lot of corporations will make a boat load of money. We will cover that problem in our final section.

