September 2015: Cozy Bear also known as Cozy Duke attacks DNC network.
The timing of the first Cozy Bear attack on the DNC was first reported in the New York Times to be September 2015 with the FBI contacting the DNC almost immediately.
http://www.nytimes.com/2016/12/13/us/politics/russia-hack-election-dnc.html?_r=0
However, a report released on January 6, 2017 by the FBI called “Assessing Russian Activities and Intentions in Recent US Elections” states on page 2 that “In July 2015, Russian Intelligence gained access to the Democratic National Committee (DNC) networks and maintained that access until at least June 2016.”
https://www.dni.gov/files/documents/ICA_2017_01.pdf
We will accept the New York Times version of events and dismiss the 2017 FBI report for several reasons:
#1 If the hack of the DNC began in July 2015, this would mean that the FBI sat on this information for more than two months before telling the DNC. Alternately, it would mean that the NSA sat on the hack for two months before telling the FBI. We are certain that the NSA either is Cozy Bear or was monitoring Cozy Bear servers due to past Cozy Bear attacks. We do not believe that either the FBI or NSA would sit on such important information for two months.
#2. The January 6 2017 FBI report contains many other inaccurate and obviously false statements. For example, the 2017 FBI report maintains that the hackers had access until June 2016. This can not possibly be true as Crowdstrike completely cleaned the DNC servers on May 1 2016 and monitored them closely after that. I realize that Guccifer claimed that he had access to the DNC servers until June 2016. But we are certain he was not telling the truth as he also made several other untrue statements and because we are certain that Crowdstrike would have cleaned him out on May 1 2016.
#3: We have discovered several other attempts by the US Intelligence community to change the narrative to make it look like Cozy Bear had access as early as May 2015. We have researched all of these claims and found them to be completely false.
We therefore believe that the original story told by the FBI agent to the NY Times in 2016 has the most validity. According to this FBI agent, he personally warned the DNC that their servers were hacked by a group called the Dukes in September 2015 - but the DNC tech team took no significant action because they did not believe he was actually from the FBI. Nothing was done for months. The incompetent mess was described in detail in a New York Times story a year later. The NY Times article states that the FBI called the DNC repeatedly but was ignored because DNC staffers thought he was an impostor rather than a real FBI agent. The NY Times article claimed that the FBI knew the Dukes were Russians and had a long history opposing them. If this were really the case, then the actions of the FBI and the DNC border on incompetence. The NY Times article links to the F Secure Report (we have already quoted about the Dukes which concluded the Dukes were Russian based on the Cozy Duke Time Stamps. As noted before, the F Secure Report ignored a mountain of information such as server call back locations indicating that the Dukes were not Russians but Americans).
Our Comments on the September 15 Cozy Bear DNC Attack
There is a fundamental problem with the first DNC attack. The FBI had evidence that a major crime had been committed with Russians hacking DNC server in Washington DC. Yet all they did was call the DNC? This is not what is supposed to happen when a major crime is committed. The FBI is required to lock down the crime scene and take position of any and all evidence in order to launch an investigation. Warrants are supposed to be entered. The hacked server is supposed to be examined. The server logs would certainly supply important clues that could eventually be traced back to the alleged hackers.

Why didn’t the FBI take control of the crime scene in September 2015???
At the very least, the FBI should should have gotten a copy of the server logs. Instead, we found out on January 5, 2017 that according to the DNC, the FBI has never examined the DNC hacked server and never asked to examine the hacked server.
https://www.buzzfeed.com/alimwatkins/the-fbi-never-asked-for-access-to-hacked-computer-servers?utm_term=.jhKq72BRv#.tgBLXokNE
A day later, the FBI disputed this claim by stating that they had asked to examine the DNC server logs in May 2016 – but the DNC refused their request.
https://www.wired.com/2017/01/fbi-says-democratic-party-wouldnt-let-agents-see-hacked-email-servers/
According to the FBI official, “This left the FBI no choice but to rely upon a third party for information. These actions caused significant delays and inhibited the FBI from addressing the intrusion earlier.”
Are you kidding me? Since when does the FBI have to get anyone’s permission, other than a judge, to seize evidence after a major crime has been committed? Had the FBI gotten the server and the DNC taken steps to clean the server, we would not today be faced with the difficult task of figuring out who hacked the DNC – and possibly the DNC would not have lost the national election – an election on which they spent over one billion dollars trying to win. The failure of the FBI to take this action is one of many questions that has never been adequately addressed.
March 22, 2016: Fancy Bear Prepares to Attack the DNC
Seven months after Cozy Bear gained access to the DNC server, Fancy Bear decided they wanted in on the action too. So Fancy Bear registered a domain with a typo—misdepatrment.com—to look like the company hired by the DNC to manage its network, MIS Department. Go to Whois.net to find out who owns this fake domain name. https://www.whois.net/default.aspxHere is what you will get:
Domain Name: MISDEPATRMENT.COM
Name Server: 1A7EA920.BITCOIN-DNS.HOSTING
Updated Date: 22-apr-2016
Creation Date: 22-mar-2016
Expiration Date: 22-mar-2017
Put in plain English, Fancy Bear used a Bitcoin hosting account to hide their identity. They created the domain name on March 22, 2016 and updated it on April 22, 2016. They need to renew it by March 22, 2017 or someone else will be able to get that domain name.
On June 17, 2016, a pro-government security group called ThreatConnect stated that the person who registered this domain used the name Frank Merdeux. ThreatConnect did not mention and did not seem to be aware of the EFF connection we described above or the Ukrainian connection we describe below. Here is a quote from the June 17 Threat Connect report:
“In reviewing the Domain Whois information reveals that the domain was registered on March 22, 2016 by frank_merdeux@europe[.]com. Farsight lists the earliest domain use as March 24, 2016. On April 24th, 2016 the domain misdepatrment[.]com moved from the parking IP Address 5.135.183[.]154 to the FANCY BEAR Command and Control IP Address 45.32.129[.]185 where it remains resolved at the time of this writing. The domain misdepatrment[.]com closely resembles the legitimate domain for misdepartment.com. Of note, MIS Department Inc. is a technology services provider that lists a variety of clients on its website, one of which is the DNC.”
https://www.threatconnect.com/blog/tapping-into-democratic-national-committee/
Put in plain English, this domain name was supposedly not activated on the Internet until March 24, 2016 when it was moved from the IP address 5.135.183.154 to the IP address 45.32.129.185. But in fact, it was used in a hacking attack on March 22, 2016. This two day gap has never been explained. Nevertheless, here is who controls these two “Fancy Bear” IP addresses: http://whatismyipaddress.com/ip-lookup
5.135.183.154 links to a clean server located in France with no apparent purpose. The domain name is similar to the IP address: ip-5-135-183.154.eu. The person and address that owns this domain name according to WHO IS was not disclosed.
45.32.129.185 links to a corporate server in San Jose CA 95113. The organization is called Choopa LLC. Their domain name for this server is vultr.com. This group appears to have several servers and several IP addresses as they use each IP address as a sub domain of their primary domain.
A WHO IS look up of this domain name revealed the following ownership information:
Server Name: VULTR.COM.PROMEDICALEBOOKS.COM
IP Address: 45.32.60.43
Registrar: GODADDY.COM, LLC
Domain Name: VULTR.COM
Name Server: NS1.CHOOPA.COM
Updated Date: 04-sep-2015
Creation Date: 06-oct-2008
Expiration Date: 06-oct-2020
Put in plain English, this domain name was created in 2008 and is paid until 2020. It is registered with a US corporation called GoDaddy which has servers located in Arizona. Given the broad powers given to the FBI over US corporate servers, it is highly unlikely that Russians would use US servers either to register their domain names or as a host location for their servers. Like much of the evidence we provide in this report, this evidence has never been disclosed to the public.
Go to https://www.vultr.com/ and you will see that they claim to be a web host with servers in 15 cities around the world. Choopa.com is a web host located in New Jersey with branches in LA, Amsterdam & Toyko.
45.32.60.43 is another of several servers owned by Choopra LLC. But this server is in Tokyo.
Promedicalebooks.com is not an active domain name. However, a WHO IS lookup reveals the following ownership:
Domain Name: PROMEDICALEBOOKS.COM
Registrar: GODADDY.COM, LLC
Name Server: NS1.VULTR.COM
Updated Date: 17-aug-2016
Creation Date: 22-jun-2016
Expiration Date: 22-jun-2017
The June 22 2016 creation date cannot possibly be true as it was active since at least March 2016. Perhaps it had lapsed and was renewed in June 2016 which would reset the clock. Clearly whoever these people are, they like GoDaddy. But there is no need for real web hosts to use GoDaddy since most web hosts are their own domain registrars. So this seems odd. In any case, since US laws extend to all US corporations, Russian hackers are not only unlikely to use servers located in the US, they are unlikely to use servers owned by any US corporation.
March 22, 2016: Billy Takes the Bait (so did Podesta)
On the same day that Fancy Bear registered the misleading domain name, William “Billy” Rhinehart, a regional field director at the Democratic National Committee, received an email from Google warning him that someone tried to access his account and that he should immediately change his password. He complied. Unfortunately for Mr. Rhinehart, it wasn’t Google who sent him that email. He, along with many others, were a victim of Fancy Bear.
The Smoking Gun (TSG) was able to obtain the original spear phishing email directly from Billy Rhinehart and shared it with ThreatConnect, who posted this screenshot of the email’s headers and identified the actual sender of the email as a Russian domain:
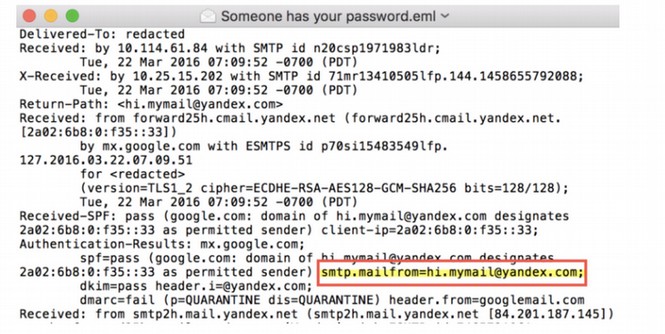
While the above screen shot seems to implicate Russian hackers, in fact it really implicates American hackers trying hard to fool people into thinking that the DNC was hacked by Russians.
A skeptical security consultant named Jeffrey Carr has written a detailed analysis of this email address. //medium.com/@jeffreycarr/can-facts-slow-the-dnc-breach-runaway-train-lets-try-14040ac68a55#.ftklbv624">https://medium.com/@jeffreycarr>
Here is a quote from his analysis:
“What’s Wrong With This Picture? Yandex is the Google of Russia. Like Google, Yandex is a search engine, and, like Gmail, Yandex‘s users can open a free email account. When you visit Yandex.ru and create a new email account, the email assigned to you has the .ru domain. However,
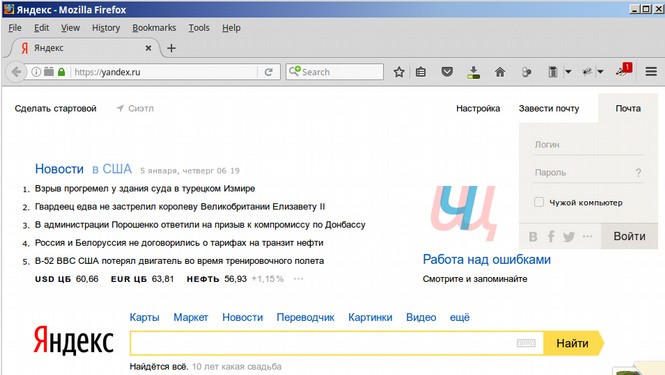
Alternately, if your Russian is not that good, you can just do a Google Search and go to the following link which is conveniently written in English to get your Yandex.com free page: https://passport.yandex.com/registration?mode=register
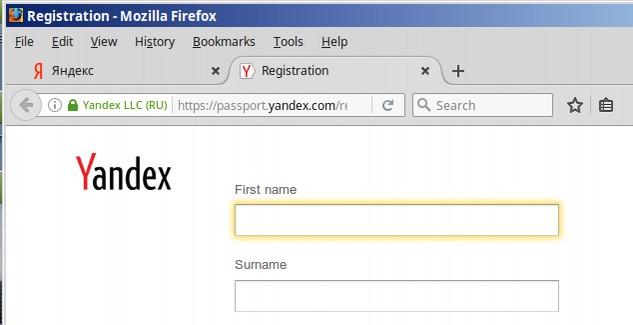
Here is the rest of the quote from Jeffrey Carr:
“Everything, including the CAPTCHA, will be in English. The point that I’m trying to make is that if anyone in Russia wanted to spear phish employees of the DNC, then creating a @yandex.com email address instead of a @yandex.ru email address is not only unnecessary extra effort but it makes absolutely no sense. However, you know what does make sense? That the person who opened the account DOESN’T SPEAK RUSSIAN! He went with Yandex.com because all analysis stops with merely the name of a Russian company, a Russian IP address, or a Russian-made piece of malware. To even argue that a Russian intelligence officer let alone a paranoid Russian mercenary hacker would prefer a Yandex.com email to a Yandex.ru email is mind-numbingly batshit insane. I have no idea who created
The Yandex.com screen shot is strong evidence that the DNC hack was not from a Russian but from a not very bright American pretending to be a Russian. This is only one of at least 20 indicators that the DNC email scam was not carried out by Russians or at the very least that Fancy Bear was not a Russian. The fact that this evidence was completely ignored by so-called security experts at Crowdstrike and elsewhere appears to be evidence of a deliberate plan to deceive the American people as to the real source of Fancy Bear and Cozy Bear. But let’s get back to our Timeline because there is more – a lot more.
March 22, 2016: Fancy Bear used a Ukrainian Server in their Email Attack
On March 22, 2016, Fancy Bear sent out thousands of fake Google Email Notices to all kinds of people, including members of the DNC including John Podesta (whose 60,000 emails were later published by Wikileaks). Here is a copy of this hacking email as published in the New York Times: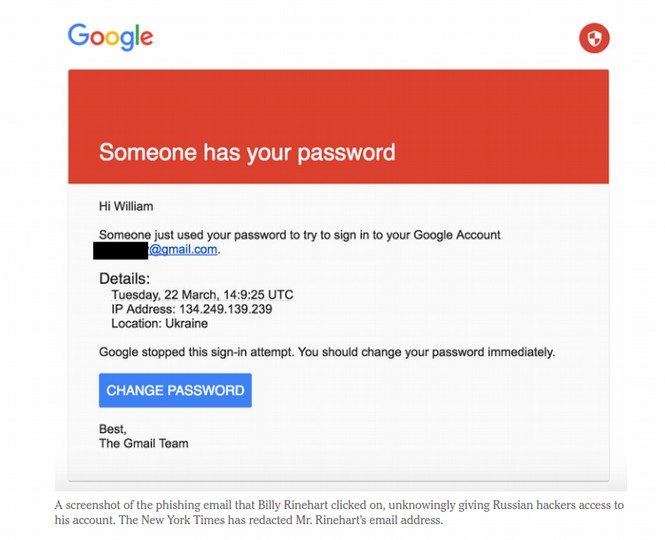
Note that the IP address of the person who supposedly used the password to the Gmail account is located in Ukraine. IP 134.249.139.239 is a broadband server in Ukraine. This may not seem to be important because the IP is open to easy access. But the fact that the IP address is in Ukraine is significant. Why would the Russians want to run an email campaign using a Ukrainian IP address? This does not make any sense.
John Podesta clicked on this link and thought he was resetting his password. In fact, he was sending the password to Fancy Bear because the link redirecting him to a form that may have looked like a Google Password reset form but was in fact a fake form. Here is a 2012 NSA document provided by Edward Snowden in 2013 confirming that the NSA uses a nearly identical strategy to gain access to a person’s email account.
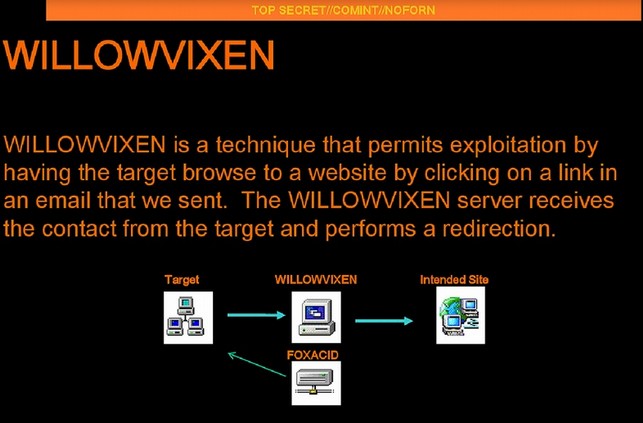
April 2016: Cozy Bear and Fancy Bear settle in to their new DNC Home.
Cozy Bear has been hacking the DNC in real time since September 2015. Fancy Bear joined in the feast on March 22, 2016. Both had unlimited access to data until May 1.
May 1, 2016: Crowdstrike kicks Cozy Bear & Fancy Bear Out of DNC Server
The FBI (again) notified the DNC that their network had been hacked. This time, the DNC finally believes the FBI and calls in Crowdstrike, who locate two intrusions and reset the DNC system. Until this time, the hackers were able to read all DNC email and chats. After about two hours of work, Crowd Strike found “two sophisticated adversaries” on the DNC network. The two groups were“APT 28” (Fancy Bear) and “APT 29.” (Cozy Bear)May 2016: Crowdstrike issues report – but does not release it to the public.
Crowdstrike issued their first report but never released it to the public. I spent a great deal of time looking for this report and if anyone has it, I am hoping you will email it to me.
Our Comments on the DNC Hack
There appears to have been some sort of effort to hide the DNC hack from the public perhaps because Clinton had not yet secured the Democratic Party nomination and they worried that yet another email scandal may have further harmed her reputation. This is the only reason I can think of to explain why the FBI failed to examine the DNC servers (something we learned on January 5, 2017). But this still does not explain the actions of the DNC or FBI. As we noted early, hacking the DNC server was a major crime. So why did the DNC call Crowdstrike instead of the FBI? When a crime is committed, you call the police. You do not call some consulting firm to clean up the crime scene before the police arrive because there is the danger that the consultants will destroy important evidence. The FBI should have gone in and taken charge on Day 1.
However, the wheels were about to fall off the DNC bus. At some point, someone gave some information to Wikileaks and they were about to go public with it. It also appears that more than one group hacked the DNC and stole their documents. But another strange thing was about to happen. An entire group of people are about to start blaming the Russians for these hacks. Perhaps this mistake was made because the Russians had falsely been accused of being Cozy Bear and Fancy Bear in the past. But it would not have taken much research to realize that there was more evidence pointing to the NSA than there was pointing to Russia.
So it seems more likely that whoever was behind this massive propaganda campaign did not want to know the truth. Somehow, it served their purpose to have Americans hating Russia. Apparently, this group was so arrogant that they felt they could keep the truth hidden forever. But the truth is a powerful weapon. It will eventually come out either through the evidence presented in this report – or some future leak or hack. When it does, the American people will once again realize they are being lied to by their own government. Hopefully, then, the people will finally vote for real political change.
Now back to the timeline because there is a lot more evidence in the coming pages that Russia was not responsible for the DNC hack. The hack may be over. But the spin is about to begin.

