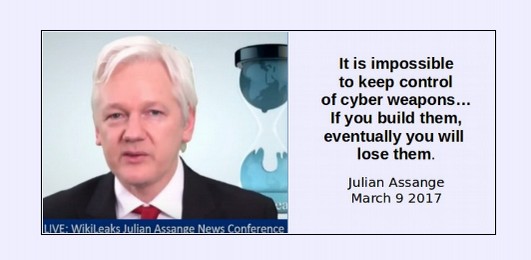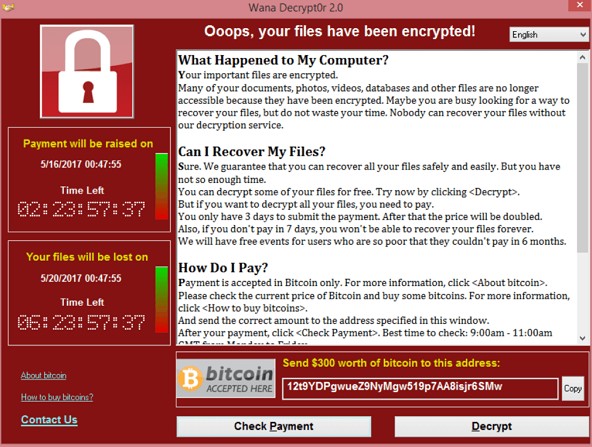
The Wanna Cry virus uses two cyber weapons called Eternal Blue and Double Pulsar. Thanks to the Wikileaks Vault 7 release on March 7, 2017, we know that both of these cyber weapons were developed by the NSA. These cyber weapons were developed by the NSA along with hundreds of other cyver weapons using tax payer dollars. But instead of protecting us, these offensive weapons are being used against us. https://wikileaks.org/ciav7p1/
In August 2016, a group called the Shadow Brokers was able to download a huge number of NSA Cyber Weapons. These weapons have now been released into the wild - meaning just about any computer hacker is now able to set up their own version of the NSA to attack Windows computers. According to one security expert, “It’s a business model that works and you don’t need a lot of investment to actually get a decent return. You can buy ransomware kits on the dark web, you can buy all the tool sets you need to undertake your own ransomware campaign quite easily.”
http://heavy.com/tech/2017/05/wannacry-wannacrypt-decryptor-virus-attacks-microsoft-nsa/
Also thanks to Wikileaks, we know that these cyber weapons take advantage of the open back door in the Windows operating system to infect and take over Windows computers through the Windows Web Browser (which is the open back door). Many security “experts” have described this as a “file sharing” problem. But it is actually much bigger than that. On March 14, 2017, Microsoft issued a “patch” which they claimed solved the Eternal Blue problem. But the patch is merely a bandaid that places some restrictions on file sharing but does not address the underlying problem – which is the open back door in the Windows computer operating system.

Predictably, on May 15, 2017, a strongert mutation of the WannaCry virus began attacking computers. Europol, the European police agency warned, "The hackers have already evolved the malware, and will probably continue to do so."
According to Zero Hedge, “at least a dozen other NSA tools are currently being discussed and worked on as the basis of potential new cyber weapons on hacking forums on the dark web.”
http://www.zerohedge.com/news/2017-05-16/hackers-sell-second-nsa-developed-cyber-weapon-dark-web
On May 16, 2017 (this morning), ShadowBrokers issued a statement claiming to have many more hacking tools they will be releasing in the coming weeks and months. Here is a quote from their statement: “TheShadowBrokers Monthly Data Dump could be being web browser, router, handset exploits and tools, select items from newer Ops Disks, including newer exploits for Windows 10, compromised network data from more SWIFT providers and Central banks.”
https://steemit.com/shadowbrokers/@theshadowbrokers/oh-lordy-comey-wanna-cry-edition@theshadowbrokers/oh-lordy-comey-wanna-cry-edition
Who is behind the Wanna Cry virus?
It could be anyone from a 14 year old kid with a new laptop to the Italian mob. Cyber blackmailers just need an internet connection and a laptop plus a little knowledge of how to access the cyber weapons now being given away for free on the Dark Web. According to a German security expert: "Just because the attacked affected 200,000 computers and 100 countries, there doesn't have to be a large-scale structure behind it. The weapon - the software - is that powerful."
http://www.dw.com/en/cybercrime-just-tip-of-iceberg-in-organized-criminality-study-finds/a-38860692
Sounding the Alarm
I have written numerous articles over the years warning that US spy agencies, including the NSA and CIA, were completely out of control. It is not merely that the NSA and CIA waste billions of tax payer dollars. The cyber weapons they create are so dangerous that they are capable of bringing down the entire US and world economy. Imagine the banking system, transportation and energy computer networks all crashing at the same time. Imagine a 14 year old kid being able to download everything needed to create the cyber version of a nuclear bomb and getting it all for free in a matter of minutes. This is the kind of danger the NSA has inflicted on all of us by creating these out of control cyber weapons.
Here is a diagram from an article I wrote just 2 months ago based on the Wikileaks releases. According to various Wikileaks CIA documents, here is what the CIA and NSA are doing:
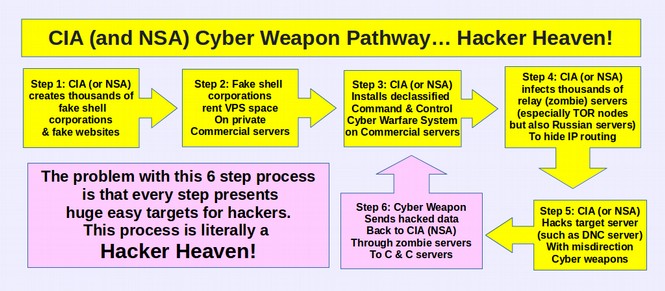
https://turningpointnews.org/hack-everything-special-report/hack-everything-part-9-wikileaks-finds-cia-fingerprints-on-russian-smoking-gun
In short, thanks to the NSA’s arrogant mis-use of billions of dollars of US tax payer funds, this latest cyber attack is just the beginning of a more long term assault on Windows computers. Over the coming days, weeks and months, we can expect hackers to create more powerful viruses all thanks to the NSA and the Windows open back door. As computer expert Jacob Applebaum once said, it will be “worse than your worst nightmare.” Instead of wasting our time worrying about Russian hackers, we should have been worried about our own NSA – which is after all more than ten times larger than the Russian hacking team.
Four years ago, I wrote a book called Free Yourself from Microsoft and the NSA, in which I described this Windows open back door and NSA cyber weapons. I predicted that this lethal combination would eventually lead to mass attacks by computer hackers.
https://freeyourselffrommicrosoftandthensa.org/
Others including William Binney and Edward Snowden (both formerly with the NSA) have also warned against the danger of allowing the NSA to access all Windows computers via the Windows back door. The problem is that any backdoor that can be used by the NSA can also be used by hackers once they gain possession of the NSA cyber weapons.
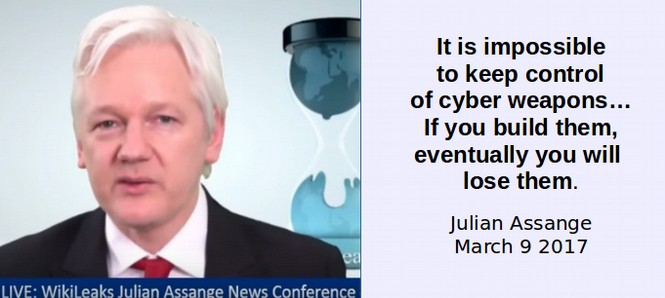
Assange noted during his March 9 2017 press conference that eventually consumers around the world will no longer trust US technology manufacturers – which will also cost US corporations billions of dollars. The mere fact that US corporations like Microsoft and Apple have already been confirmed to be Prism Partners of the NSA should cause folks even in the US to not trust US technology firms. The new Wikileaks revelation that the CIA has compromised 22,000 servers in the US should make it clear that we cannot trust US web servers and web hosts – a fact that I wrote about in a book over a year ago.
https://createyourowninteractivewebsite.com/1-start-here/1-3-how-to-protect-your-website
Here is what Julian Assange had to say about the CIA today (May 16 2017):
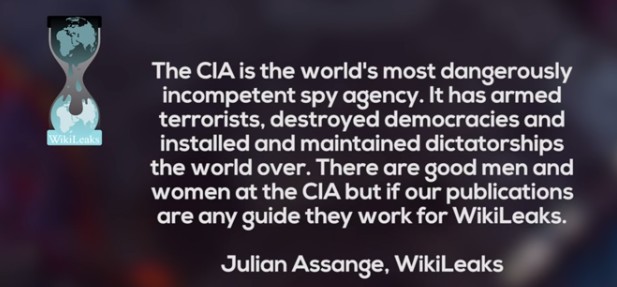
Why Microsoft will never close the backdoor to the Windows Operating System
The real solution to the insecurity of the Windows operating system is not to install some temporary bandaid patch – or even hundreds of bandaid patches. The only way to make the Windows operating system really secure is to close the backdoor in Windows. In other words, Microsoft needs to permanently and completely disconnect its web browser from its core operating system. The reason Microsoft will never close this back door is that they are trying to make money off the Windows operating system. Thus, they want to make sure that folks have a legal copy of Windows by building in a function that allows your computer to “phone home” to Microsoft and allows Microsoft to remotely control and shut down your computer if they find anything on your computer they do not like. The NSA uses this same remote control function to control your computer – and so do computer hackers. It is short sighted greed that prevents Microsoft from producing a secure operating system. Linux computers do not need to phone home because the Linux operating system is free – so no need to check, remotely control or shut down computers.
The good news is that, as I have also written about for many years, the CIA (and the NSA) are having trouble hacking Linux computers. This is almost certainly due to the distributed nature of Linux operating systems (there are more than 100 variations) and the fact that the Linux operating system specifically excludes web browsing tools from the core of the operating system. Below is an image of the CIA Linux hacking page (taken from the Wikileaks Vault 7 release) confirming that CIA efforts to hack Linux computers is still incomplete:
Clearly the NSA and CIA are trying very hard to break into the Linux operating system. But so far, their only success has been by compromising the UEFI startup program. This is why I recommend that even if you are using a Linux computer, you should not use the UEFI startup program and instead to use the COREBOOT startup program. Meanwhile the Apple and Windows pages in the Wikileaks documents are filled with hundreds of attacking methods.
Conclusion… It is time for Real Computer Security
I have spent years studying the NSA. I mistakenly thought it was the biggest and worst threat to world peace and the world economy. I now realize I was wrong. The CIA appears to be twice as large as the NSA. This is like doing battle against Godzilla for several years only to wake up one morning and learn that there is another monster twice the size of Godzilla. I was having trouble sleeping before these new Wikileaks CIA documents. Now I am really having trouble sleeping.

These are important security issues that affect every computer user in the entire world. It is time not only to end the NSA and CIA but it also time for every computer user who cares about the future of our economy to move away from unsafe and badly designed operating systems such as Microsoft and Apple and replace them with the free, secure Linux Operating system. Here is a link on how to make the move to Linux: https://learnlinuxandlibreoffice.org/

Please share this report with anyone you know who is interested in learning the truth about the real computer security. As always, we look forward to your questions and comments.
Regards,
David Spring M. Ed.
Turning Point News.org
Email: david (at) turningpointnews.org